Configuring the Ranger HDFS Plugin for SSL
The following steps show how to configure the Ranger HDFS plugin for SSL. You can use the same procedure for other Ranger components.
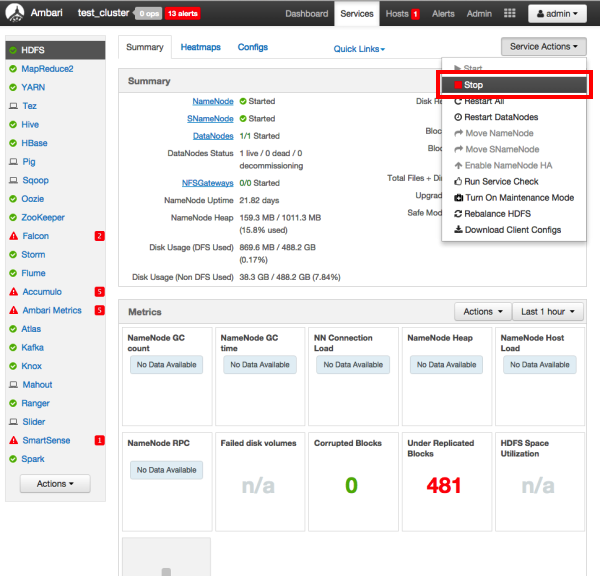
Stop HDFS by selecting Service Actions > Stop.
Under Ranger Settings, provide the value in the External URL box in the format
https://<hostname of policy manager>:<https port>.Select Advanced ranger-hdfs-policymgr-ssl and set the following properties:
xasecure.policymgr.clientssl.keystore-- Enter the public CA signed keystore for the machine that is running the HDFS agent.xasecure.policymgr.clientssl.keystore.password-- Enter the keystore password.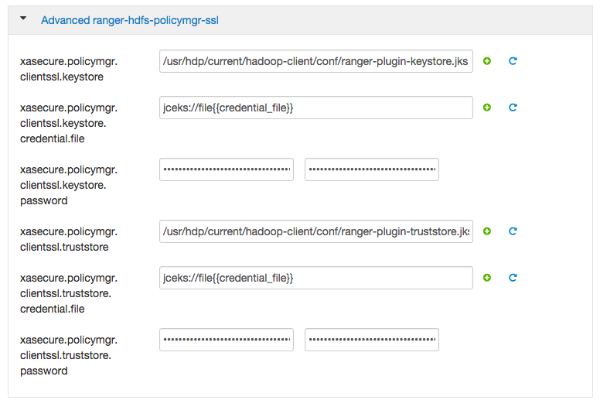
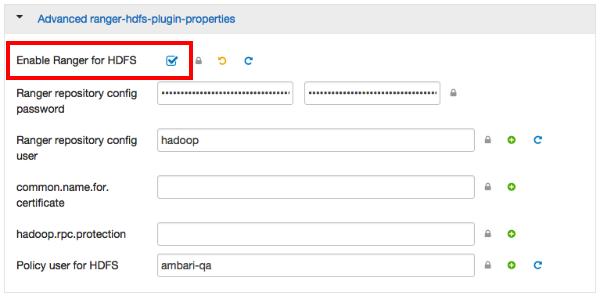
Select Advanced ranger-hdfs-plugin-properties, then select the Enable Ranger for HDFS check box.
Click Save to save your changes.
Start HDFS by selecting Service Actions > Start.
Restart Ranger Admin.
Log into the Ranger Policy Manager UI as the admin user. Click the Edit button of the HDFS repository and provide the CN name of the keystore as the value for Common Name For Certificate, then save your changes.
Start the HDFS service.
Select Audit > Agents. You should see an entry for your repo name with HTTP Response Code 200.
![[Note]](../common/images/admon/note.png) | Note |
|---|---|
This procedure assumes that the keystores provided for the Admin and agent are signed by a public CA. Provide an identifiable string as the value for Common Name when generating certificates. Important note: In the case where multiple servers talking to ranger admin for downloading policies for the same service/repository (e.g. HBase Master and Region servers, multiple NameNodes or Hive servers in an HA environment, be sure to use the repo name or a common string across all of the nodes (such as HbasePlugin, HdfsPlugin etc). (Note this and enter the same value in Common Name For Certificate field in the edit repository page in the Policy Manager UI). |
![[Note]](../common/images/admon/note.png) | Note |
|---|---|
Ranger Admin will use the JAVA truststore, so you need to add your
plugin certificate inside the Java truststore. Alternatively, you can
specify a custom truststore by editing
-Djavax.net.ssl.trustStore=/etc/security/ssl/truststore.jks -Djavax.net.ssl.trustStorePassword=hadoop For example: JAVA_OPTS=" ${JAVA_OPTS} -XX:MaxPermSize=256m -Xmx1024m -Xms1024m
-Djavax.net.ssl.trustStore=/etc/security/ssl/truststore.jks
-Djavax.net.ssl.trustStorePassword=hadoop" |