Add a new shared provider configuration
An example of how to add new authorization provider in the manager shared provider configuration.
It is possible that you add a brand new shared provider configuration. In
this example you will see how to create
testProviders with the
following providers set:authentication:ShiroProvider(LDAP) orPAMidentity-assertion:Defaultauthorization:Ranger(XASecurePDPKnox)
This particular
authorization provider is set as follows
(in its JSON
descriptor):{
"role": "authorization",
"name": "AclsAuthz",
"enabled": "true",
"params": {
"knox.acl.mode": "OR",
"knox.acl": "KNOX_ADMIN_USERS;KNOX_ADMIN_GROUPS;*"
}
}-
From Cloudera Manager > Knox > Configuration, add the following entry in the
Knox Gateway Advanced Configuration Snippet (Safety Valve) for conf/cdp-descriptors.xml:- name =
providerConfigs:testProviders - value =
role=authentication#authentication.name=ShiroProvider#authentication.param.main.pamRealm=org.apache.knox.gateway.shirorealm.KnoxPamRealm#authentication.param.main.pamRealm.service=login#role=identity-assertion#identity-assertion.name=Default#role=authorization#authorization.name=XASecurePDPKnox
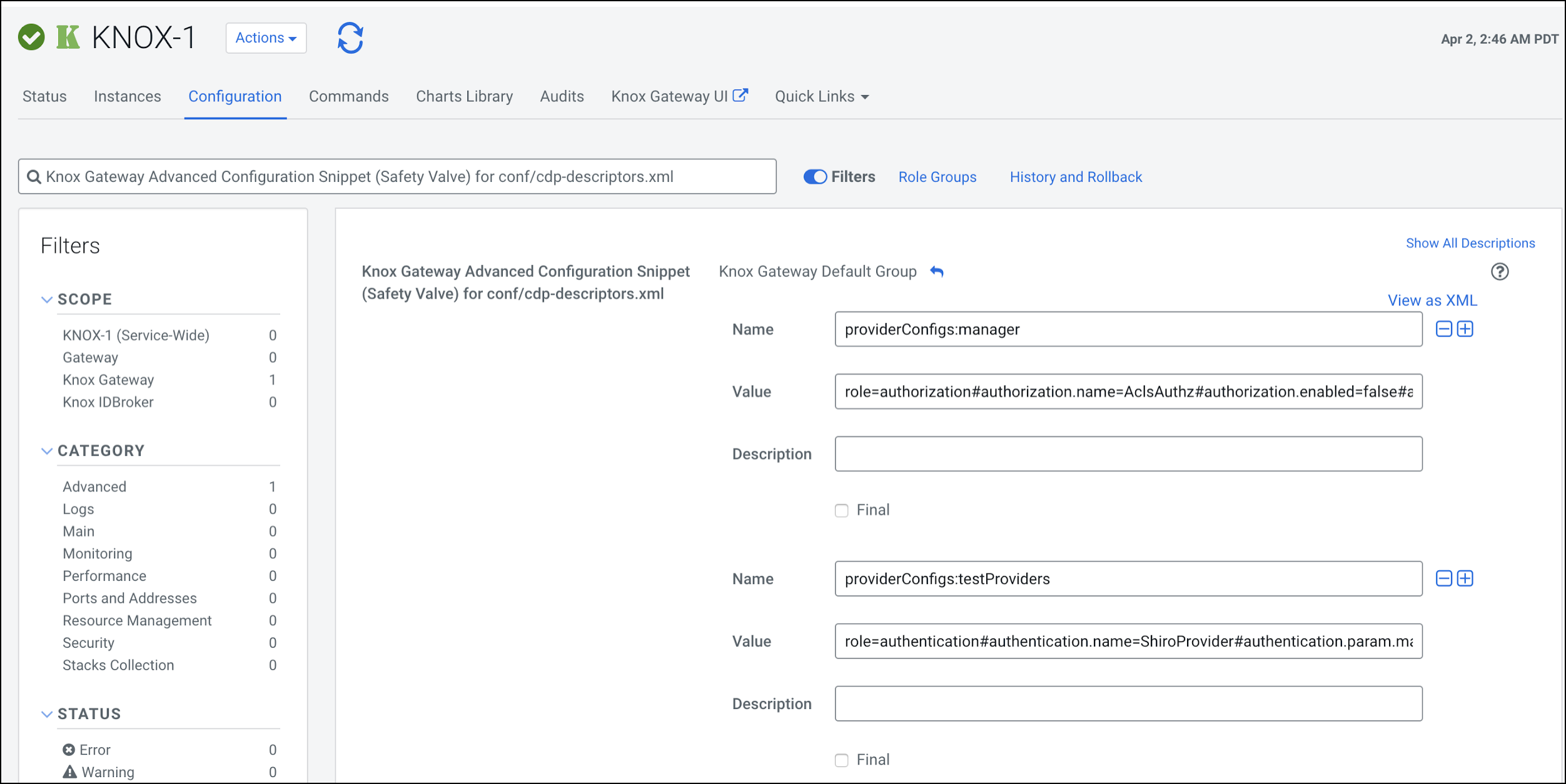
- name =
- Save your changes.
- Refresh the cluster.
-
Validate:
$ curl -ku knoxui:knoxui 'https://johndoe-1.abc.cloudera.com:8443/gateway/admin/api/v1/providerconfig/testProviders' { "providers" : [ { "role" : "authentication", "name" : "ShiroProvider", "enabled" : true, "params" : { "main.pamRealm" : "org.apache.knox.gateway.shirorealm.KnoxPamRealm", "main.pamRealm.service" : "login" } }, { "role" : "identity-assertion", "name" : "Default", "enabled" : true, "params" : { } }, { "role" : "authorization", "name" : "XASecurePDPKnox", "enabled" : true, "params" : { } } ] }
