Configure Ranger Admin High Availability with a Load Balancer
For clusters that have multiple users and production availability requirements, you may want to configure Ranger high availability (HA) with a load-balancing proxy server to relay requests to and from Ranger.
- Configure an external load balancer to use with Ranger HA.
-
In Cloudera Manager, select Ranger, then select Actions > Add Role
Instances.
-
On the Add Role Instances page, click Select hosts.
-
On the selected hosts page, the primary Ranger Admin host is selected by default.
Select your configured backup Ranger host (
ranger-host2-fqdn). A Ranger Admin (RA) icon appears in the Added Roles column for the selected backup host. Click OK to continue.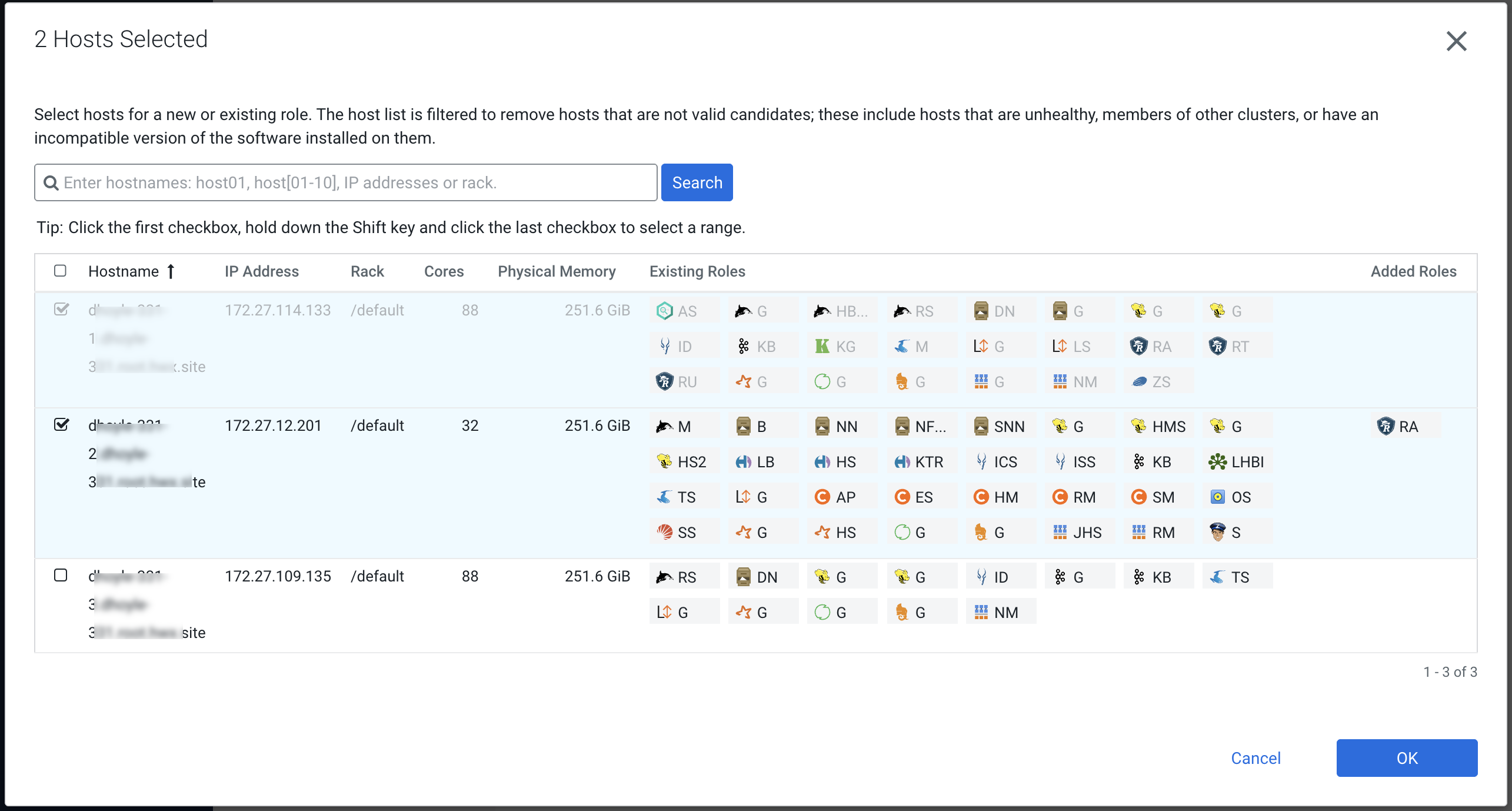
-
The Add Role Instances page is redisplayed with the new backup host. Click
Continue.
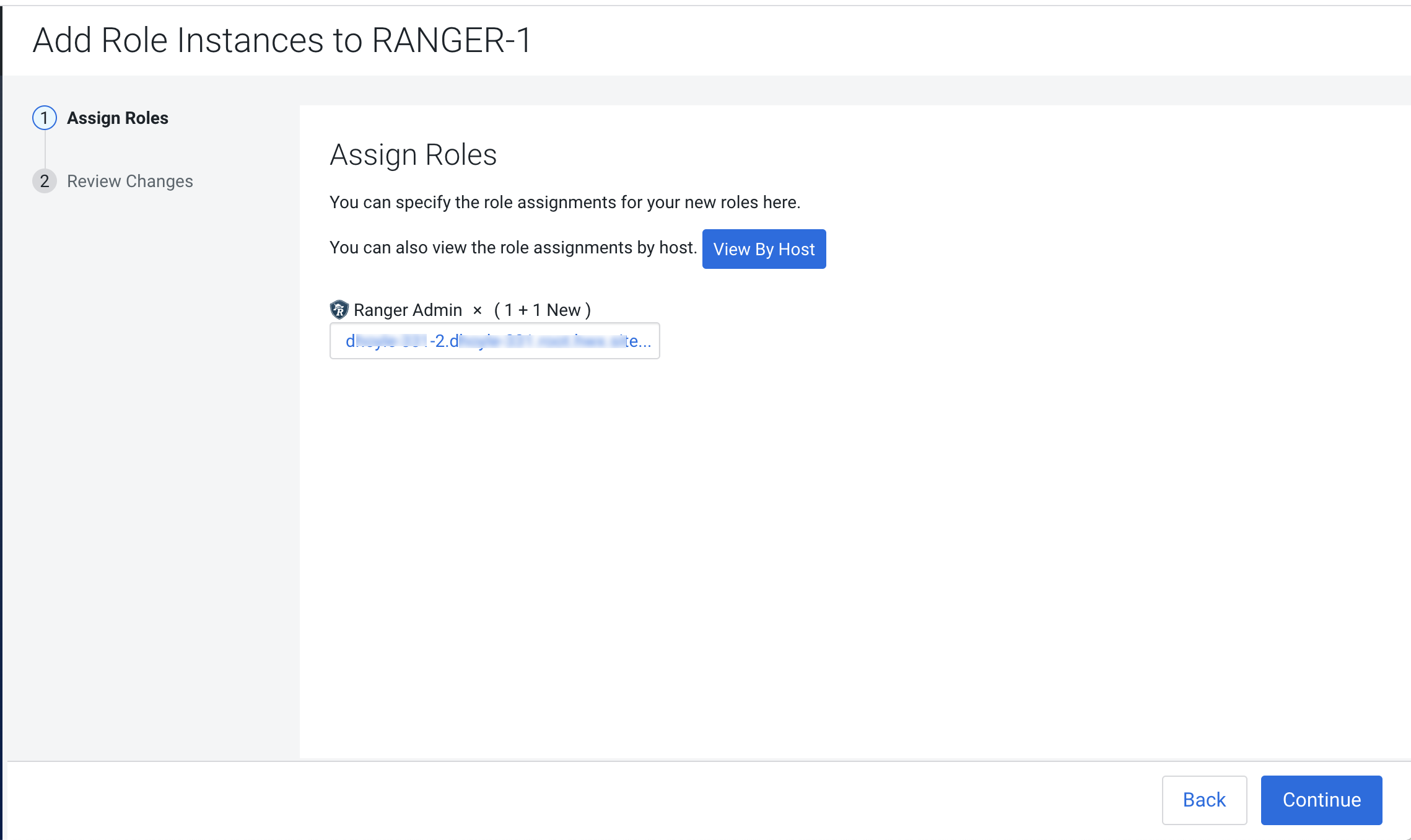
-
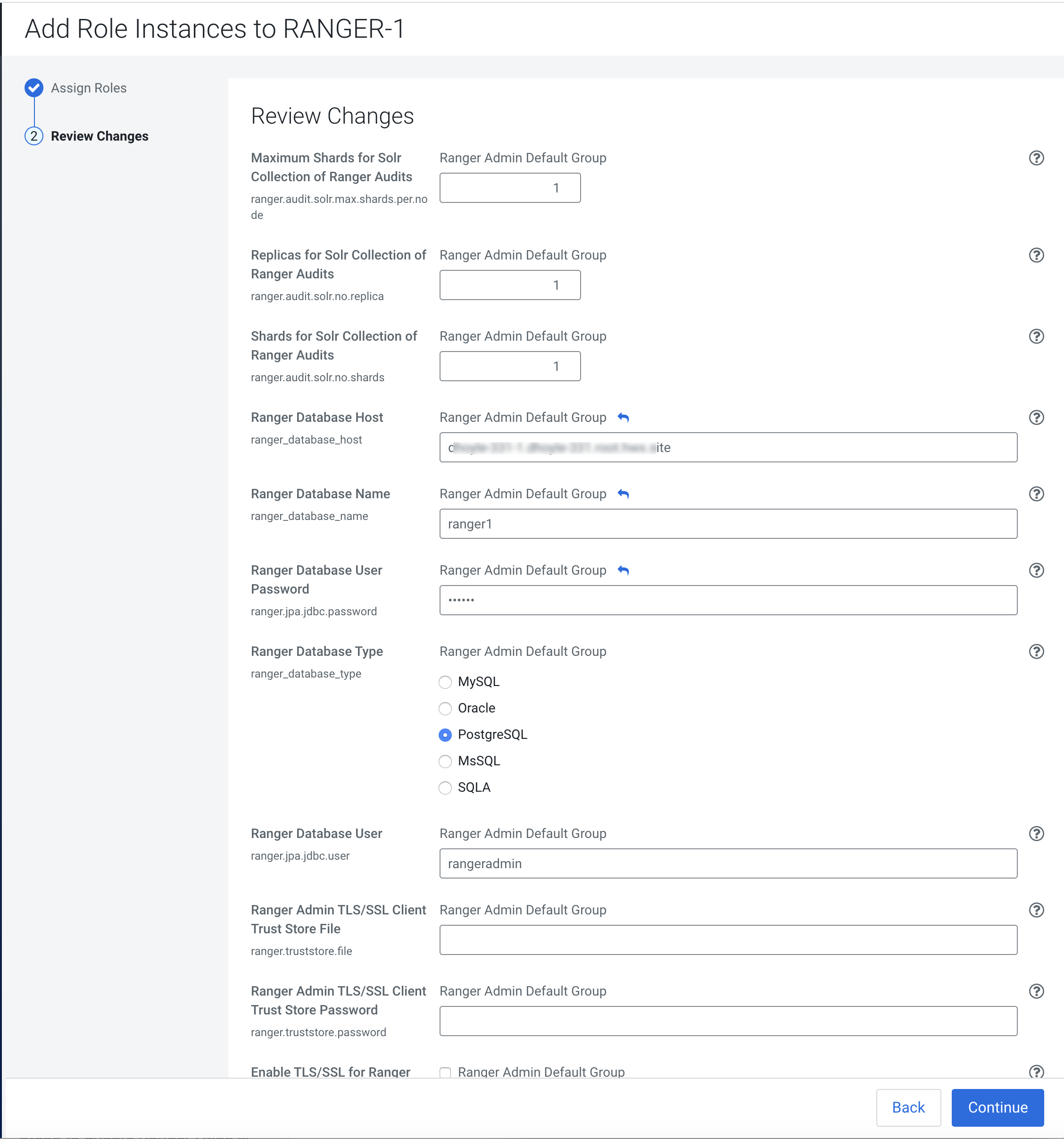
Review the settings on the Review Changes page, then click Continue.
-
Update the Ranger Load Balancer Address property
(
ranger.externalurl) with the load balancer host URL and port, then click Save Changes.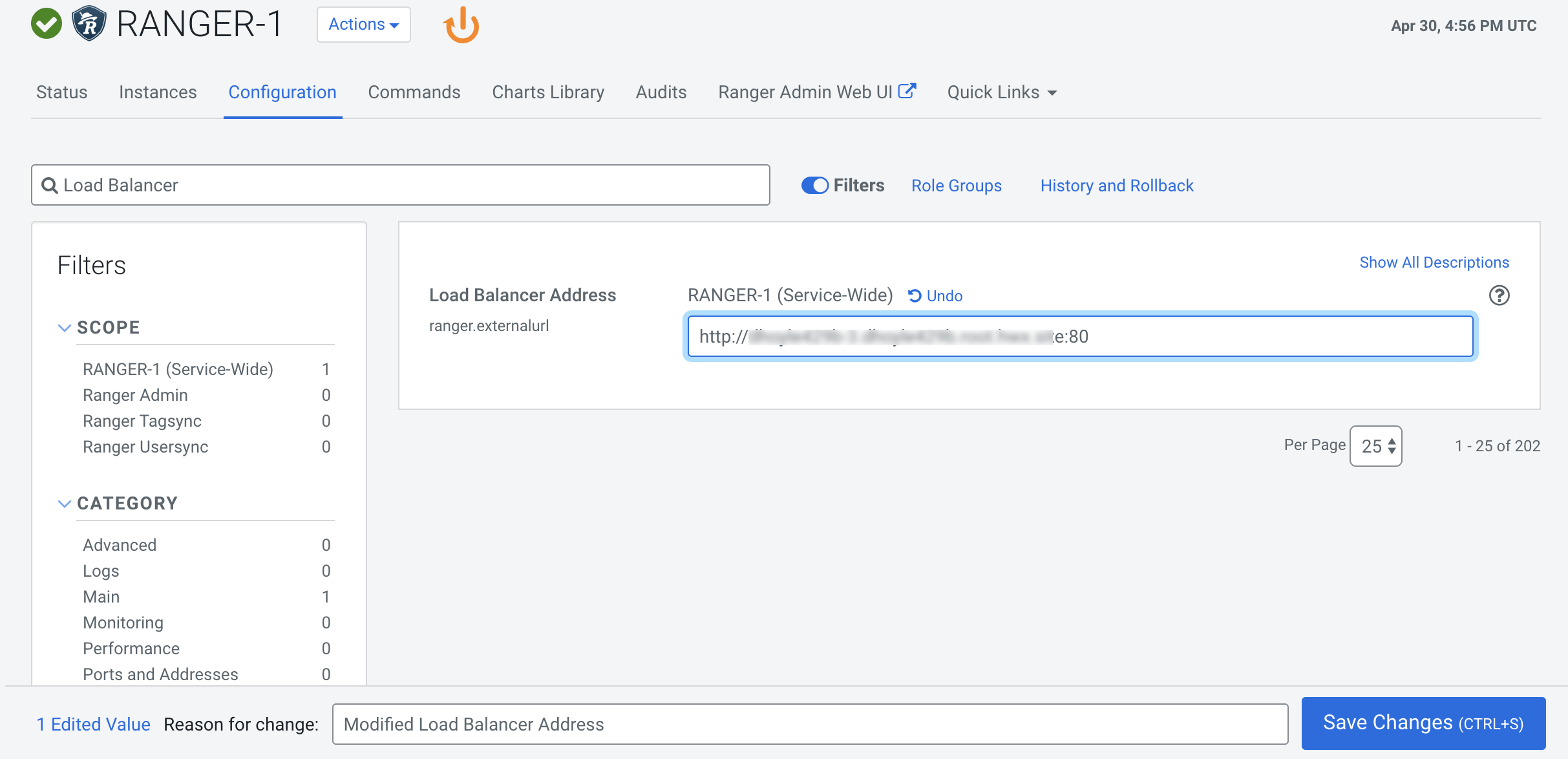
-
If Kerberos is configured on your cluster, use SSH to connect to the KDC server
host. Use the
kadmin.localcommand to access the Kerberos CLI, then check the list of principals for each domain where Ranger Admin and the load-balancer are installed.kadmin.local kadmin.local: list_principals
For example, if Ranger Admin is installed on <host1> and <host2>, and the load-balancer is installed on <host3>, the list returned should include the following entries:
HTTP/ <host3>@EXAMPLE.COM HTTP/ <host2>@EXAMPLE.COM HTTP/ <host1>@EXAMPLE.COM
If the HTTP principal for any of these hosts is not listed, use the following command to add the principal:
kadmin.local: addprinc -randkey HTTP/<host3>@EXAMPLE.COM
-
If Kerberos is configured on your cluster, complete the following steps to create a
composite keytab.
-
SSH into the Ranger Admin host, then create a keytabs directory.
mkdir /etc/security/keytabs/ -
Copy the ranger.keytab from the current running process.
cp /var/run/cloudera-scm-agent/process/<current-ranger-process>/ranger.keytab /etc/security/keytabs/ranger.ha.keytab -
Run the following command to invoke
kadmin.local.kadmin.local -
Run the following command to add the SPNEGO principal entry on the load
balancer node.
ktadd -norandkey -kt /etc/security/keytabs/ranger.ha.keytab HTTP/load-balancer-host@EXAMPLE.COM -
Run the following command to add the SPNEGO principal entry on the node where
the first Ranger Admin is installed.
ktadd -norandkey -kt /etc/security/keytabs/ranger.ha.keytab HTTP/ranger-admin-host1@EXAMPLE.COM -
Run the following command to add the SPNEGO principal entry on the node where
the second Ranger Admin is installed.
ktadd -norandkey -kt /etc/security/keytabs/ranger.ha.keytab HTTP/ranger-admin-host2@EXAMPLE.COM -
Run the following command to exit
kadmin.local.exit -
Run the following command to verify that the
/etc/security/keytabs/ranger.ha.keytabfile has entries for all of the required SPNEGO principals.klist -kt /etc/security/keytabs/ranger.ha.keytab -
On the backup (
ranger-admin-host2) Ranger Admin node, run the following command to create akeytabsfolder.mkdir /etc/security/keytabs/ -
Copy the
ranger.ha.keytabfile from the primary Ranger Admin node (ranger-admin-host1) to the backup (ranger-admin-host2) Ranger Admin node.scp /etc/security/keytabs/ranger.ha.keytab root@ranger-host2-fqdn:/etc/security/keytabs/ranger.ha.keytab -
Run the following commands on all of the Ranger Admin nodes.
chmod 440 /etc/security/keytabs/ranger.ha.keytab chown ranger:hadoop /etc/security/keytabs/ranger.ha.keytab
-
SSH into the Ranger Admin host, then create a keytabs directory.
-
Update the following
ranger-admin-site.xmlconfiguration settings using the Safety Valve.ranger.spnego.kerberos.keytab=/etc/security/keytabs/ranger.ha.keytab ranger.spnego.kerberos.principal=*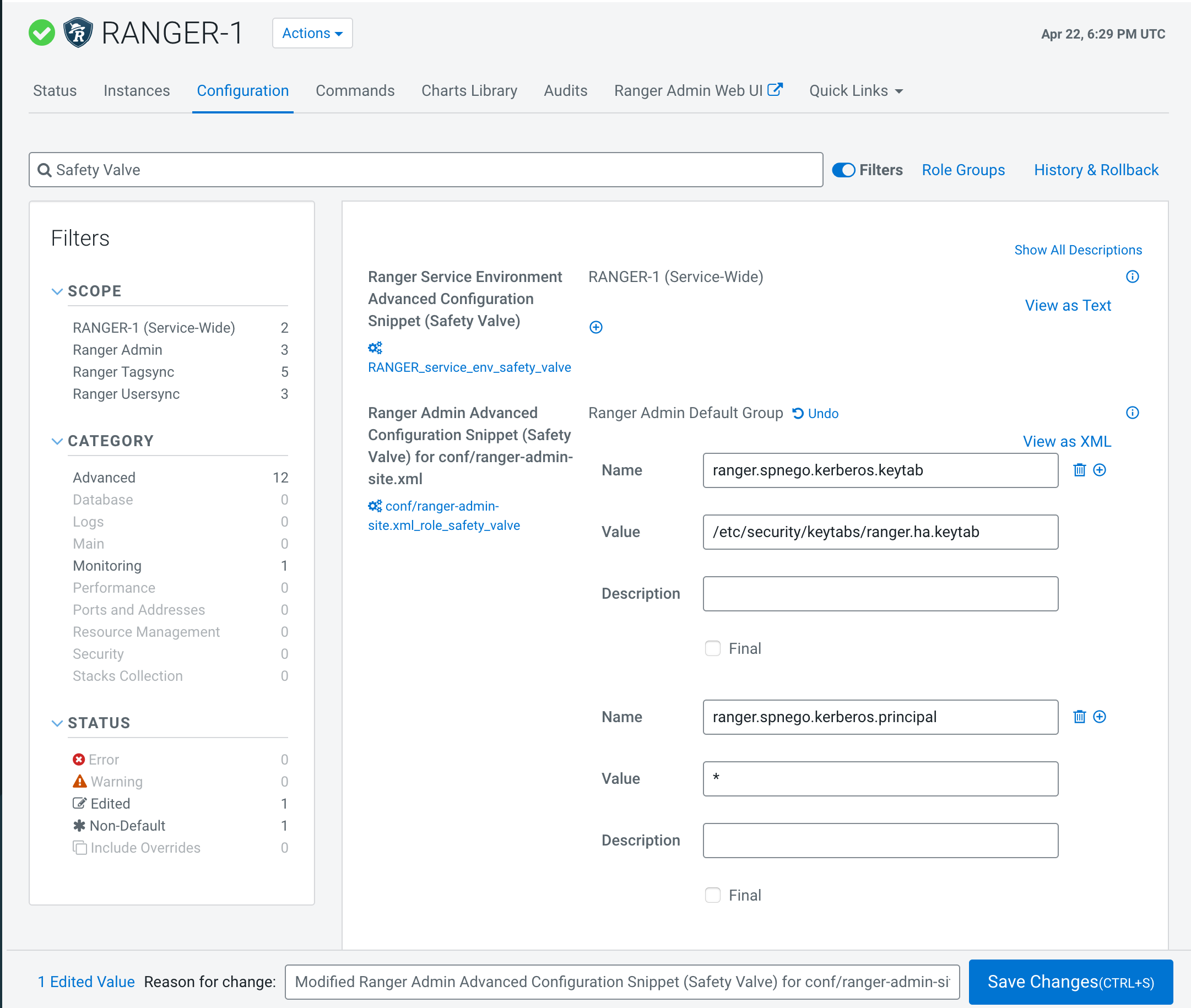
-
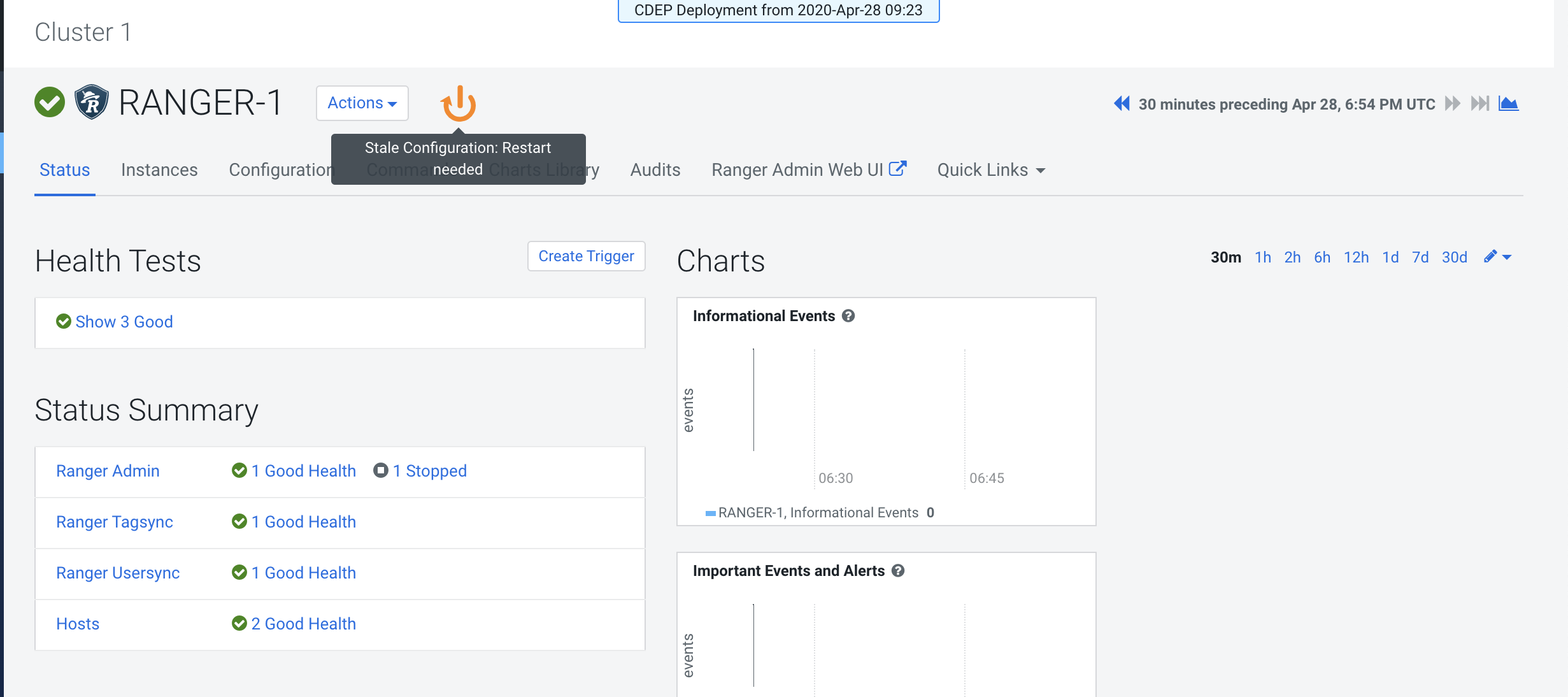
Restart all cluster services that require a restart, then click Finish.
-
Use a browser to check the load-balancer host URL (with port). You should see the
Ranger Admin page.

