SRM security example for a cluster environment managed by a single Cloudera Manager instance
To run SRM in a secure environment with two clusters that have identical security
configuration and are managed by the same Cloudera Manager, you must configure security for the
SRM service and the srm-control command line tool on both clusters.
s
Consider the following replication environment.
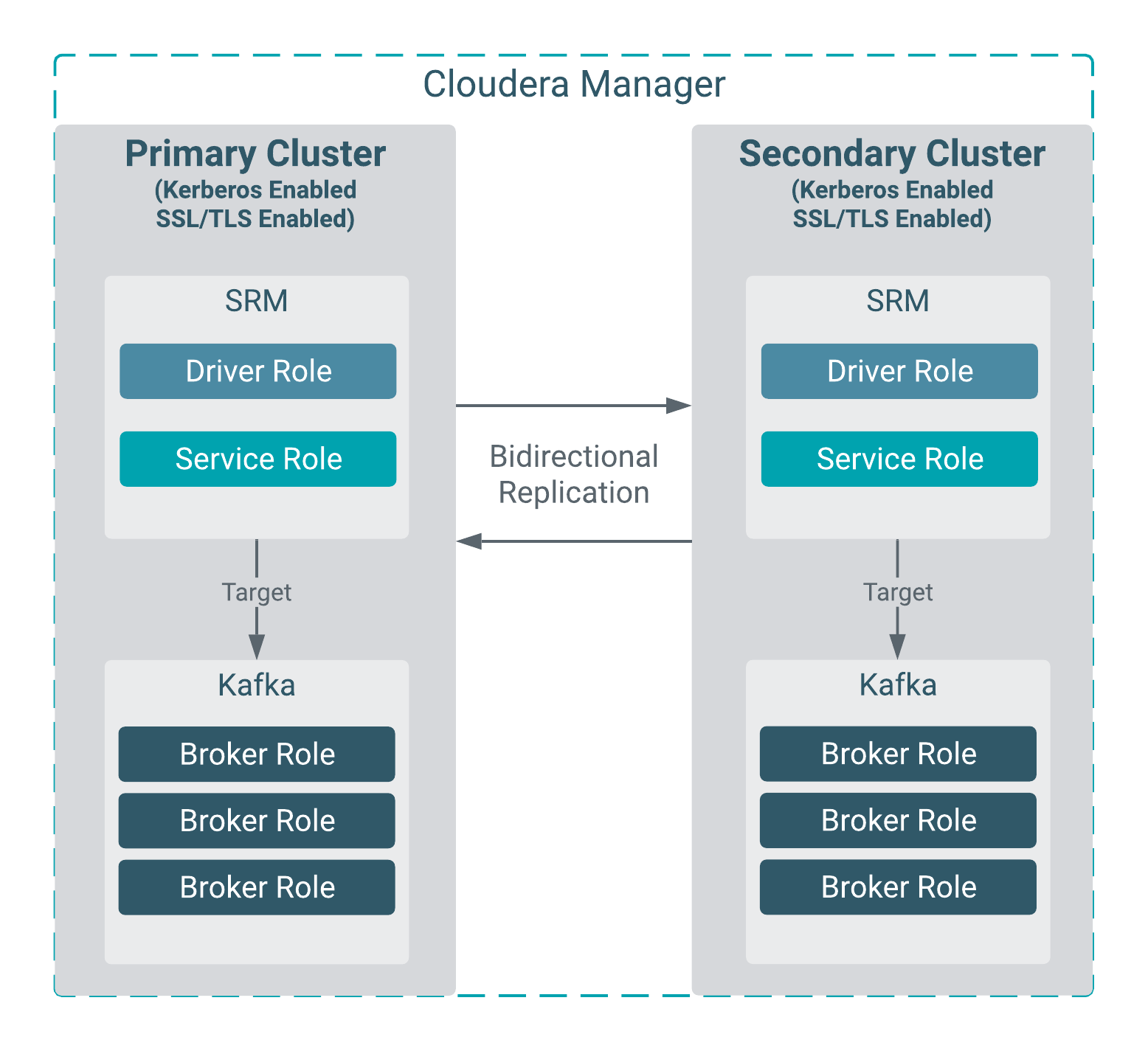
There are two clusters, each with a Kafka and a Streams Replication Manager (SRM) service deployed on it. Both clusters are managed by the same Cloudera Manager. The clusters have an identical security setup. TLS/SSL, Kerberos, and Auto-TLS are enabled on both clusters. In addition, the same Kerberos KDC and trusted CA is used by both clusters. Data replication is bidirectional. All SRM driver and service roles target the same cluster and Kafka service they are deployed in.
srm-control command line tool
on both clusters. In this scenario, the SRM service is configured with Cloudera Manager. The
srm-control tool can be configured either with Cloudera Manager or
environment variables. 