Installing Ranger KMS backed by a Database and HA
The tasks and steps for installing the Ranger Key Management System (KMS) with High Availability (HA) service that uses a database as the backing key store.
This task uses the Set up HDFS Data At Rest Encryption wizard to install a Ranger KMS with HA service that uses a database as the backing key store.
The following image shows the Set up HDFS Data At Rest Encryption page. When you select your encryption keys root of trust option, a list of tasks that you must do to enable encryption to-and-from HDFS is displayed.
You complete each task independently from the other tasks. Where, the task’s Status column indicates whether the step has been completed and the Notes column provides additional context for the task. If your Cloudera Manager user account does not have sufficient privileges to complete a task, the Notes column indicates the privileges that are required.
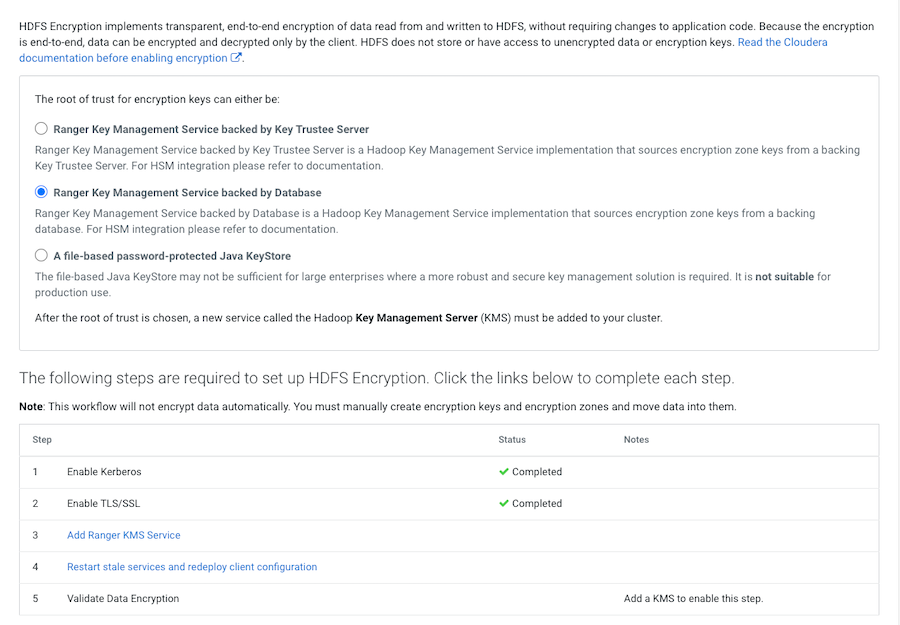
- Enable Kerberos
- Enable TLS/SSL
- Add a Ranger KMS Service
- Restart the stale services and redeploy the client configuration
- Validate the Data Encryption
- Update the Ranger KMS backed by a Database service's URL
- Create a Ranger Audit Directory
- The cluster in which Cloudera Manager and the Cloudera Ranger service is installed, is up and running.
- A Ranger KMS database has been created as the underlying keyStore mechanism. This database must be separate from the Ranger database.
- Communication through secure connections is enabled with the Transport Layer Security (TLS) protocol and your network authentication is enabled with the Kerberos protocol.
- You have securely recorded the following backing key store database access
credentials, as you will be required to supply them during the installation
steps:
- The Database name.
- The Database hostname.
- The user name and password that has full administrative privileges to the backing key store database.
Installing the Ranger KMS Service
The Set up HDFS Data At Rest Encryption wizard's installation step that installs the Ranger Key Management System (KMS) with High Availability (HA) service on your cluster.
Describes the steps that install the Ranger Key Management System (KMS) service on your cluster and associates it with your backing key store database.
Restarting the Stale Services and Redeploying the Client Configuration
The Set up HDFS Data At Rest Encryption wizard's step for restarting stale services and redeploying the client configuration.
Describes the steps that restart stale services after installing the Data-at-Rest HDFS Ranger KMS service option on your cluster.
Validating Data Encryption to-and-from HDFS
The Set up HDFS Data At Rest Encryption wizard's step for validating the data encryption to-and-from HDFS.
Describes the steps which verify that the Data-at-Rest HDFS Ranger KMS service option can successfully encrypt your data to-and-from HDFS.
Post-Tasks for the Data-at-Rest HDFS Ranger KMS Service
The post-tasks that you must perform after you have set up the Data-at-Rest HDFS Ranger KMS service option.
Describes the post-task steps.
- Update the Data-at-Rest HDFS Ranger KMS service's URL
- Create a Ranger Audit Directory
- (Ranger KMS with Key Trustee Server service only) Update the Authentication Properties and KMS Hadoop cache settings
