Authenticating Hue users with Knox SSO
You can use the Apache Knox Gateway to interact with Hue REST APIs and the Hue user interface, along with other CDP components and services. To set up Knox Single Sign-on (SSO) to authenticate users, you must configure the KnoxSpnegoDjangoBackend property using Cloudera Manager.
To authenticate users using Knox SSO, you must have Knox installed on your CDP cluster, also known as a secure cluster.
- Sign in to Cloudera Manager as an Administrator.
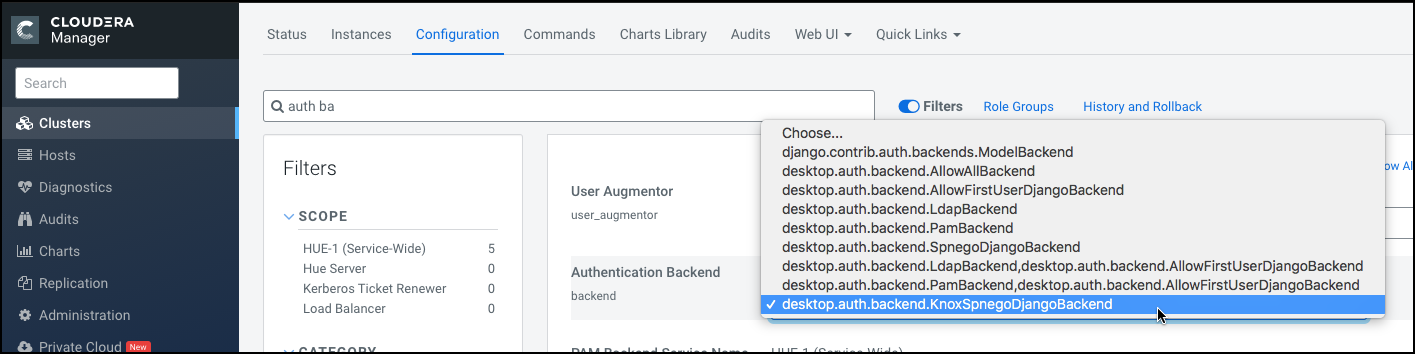
- Go to Clusters > Hue service > Configurations and search for the Authentication Backend field.
-
Select desktop.auth.backend.KnoxSpnegoDjangoBackend from
the dropdown.
-
Go to Hue Service Advanced Configuration Snippet (Safety Valve) for
hue_safety_valve.ini) and comment or remove any SAML-specific
configurations, if present.
- Click Save Changes.
-
Go to Clusters > $Knox service > Instances and note down the hostnames of the Knox Gateways.
You must provide these details in the next step.If you have set up Knox in High-Availablity (HA) mode, then you can see more than one Knox Gateways listed on the Instances tab.
- Go back to Clusters > Hue service > Configurations and search for the Knox Proxy Hosts field.
-
Enter the hostname of the Knox Gateway that you noted earlier.
If you have set up Knox HA, then click + to add another hostname.
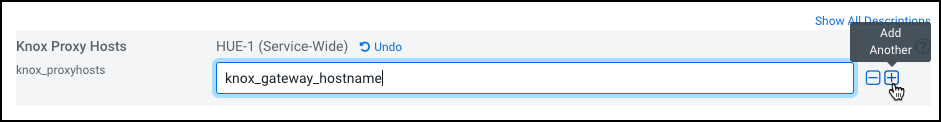
- When integrating Hue with Knox, it is essential to deploy a Hue Load Balancer. After deployment, specify the Load Balancer hostname in the Knox Proxy Hosts field by clicking the + icon.
-
Click Save Changes.
You would see the following warning:
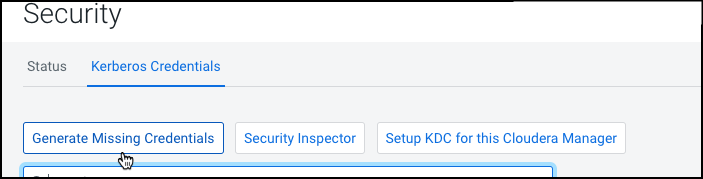
Role is missing Kerberos keytab. Go to the Kerberos Credentials page and click the Generate Missing Credentials button. - Click Administration on the Cloudera Manager left navigation panel and select Security.
-
Go to the Kerberos Credentials tab and click
Generate Missing Credentials.
A pop-up showing the status is displayed.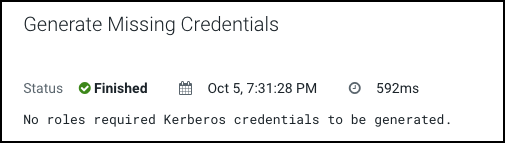
-
Go to Clusters > Hue service and click Restart next to
Actions.
-
On the Stale Configurations page, click Restart
Stale Services.
The Restart Stale Services wizard is displayed.
-
On the Review Changes page, select Redeploy
client configuration, and click Restart
Now.
The Command Details page shows the live status as the service restarts.When all the steps are complete, click Finish.
-
From the Hue service page, click Web UI > Knox Gateway UI.
The Knox Gateway UI is displayed. -
On the General Proxy Information page, expand the CDP
Proxy topology by clicking + cdp-proxy under
Topologies.
The list of services that are configured with the cdp-proxy topology is displayed.
-
Click on the Hue logo.

You should be able to log in to the Hue web UI.You can also log into Hue using the following URL:https://[***HOSTNAME***]:[***PORT***]/gateway/cdp-proxy/hue/ -
Go to Clusters > Knox > Configuration and add the following entries in the Knox Simplified
Topology Management - cdp-proxy field:
HUE:httpclient.socketTimeout=[***TIMEOUT-IN-MINUTES***]HUE:httpclient.connectionTimeout=[***TIMEOUT-IN-MINUTES***]Replace [***TIMEOUT-IN-MINUTES***] with the actual timeout value depending on the load on your load on the cluster or environment. For example, to set a timeout of 20 minutes, specify 20m. The default timeout value is 5m. - Restart the Knox service.
