Step 4: Enable Kerberos using the wizard
How to enable Kerberos using the Cloudera Manager wizard.
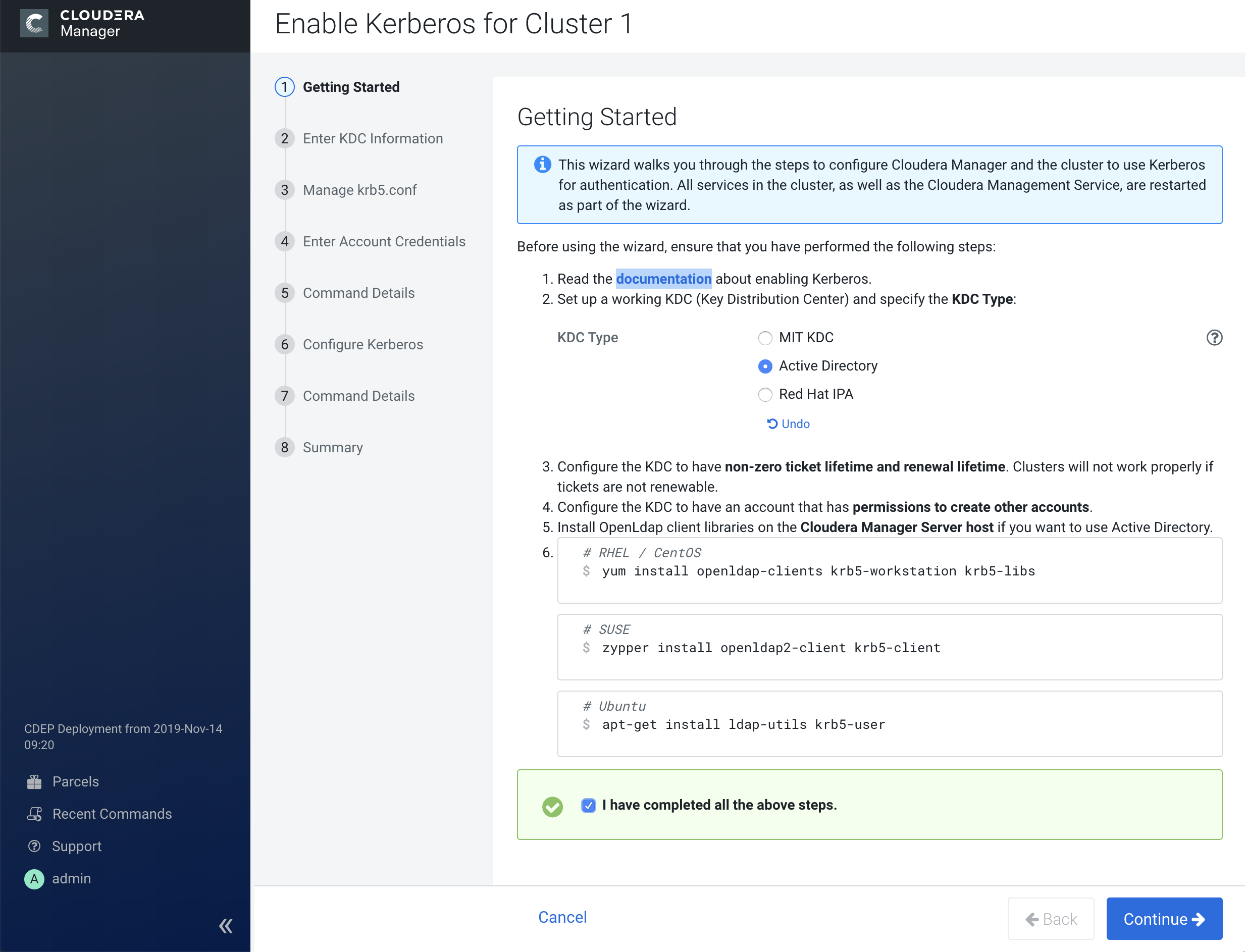
1. Getting Started
Learn about the tasks you need to perform before you enable Kerberos using the Cloudera Manager wizard.
- Set up a working KDC in Step 1 of the wizard as described below. Cloudera Manager supports authentication with MIT KDC, Active Directory, and Red Hat Identity Management/FreeIPA.
- Configure the KDC to allow renewable tickets with non-zero ticket lifetimes.
Active Directory allows renewable tickets with non-zero lifetimes by default. You can verify this by checking in Active Directory.
For MIT KDC, make sure you have the following lines in thekdc.conf.max_life = 1d max_renewable_life = 7d - If you are using Active Directory, make sure LDAP over TLS/SSL (LDAPS) is enabled for the Domain Controllers.
- Host names must be in lowercase. If you use uppercase letters in any host name, the cluster services will not start after enabling Kerberos.
- Create an account for Cloudera Manager that has the permissions to create other
accounts in the KDC. This should have been completed as part of
Step 3: Create the Kerberos Principal for Cloudera Manager Server
.
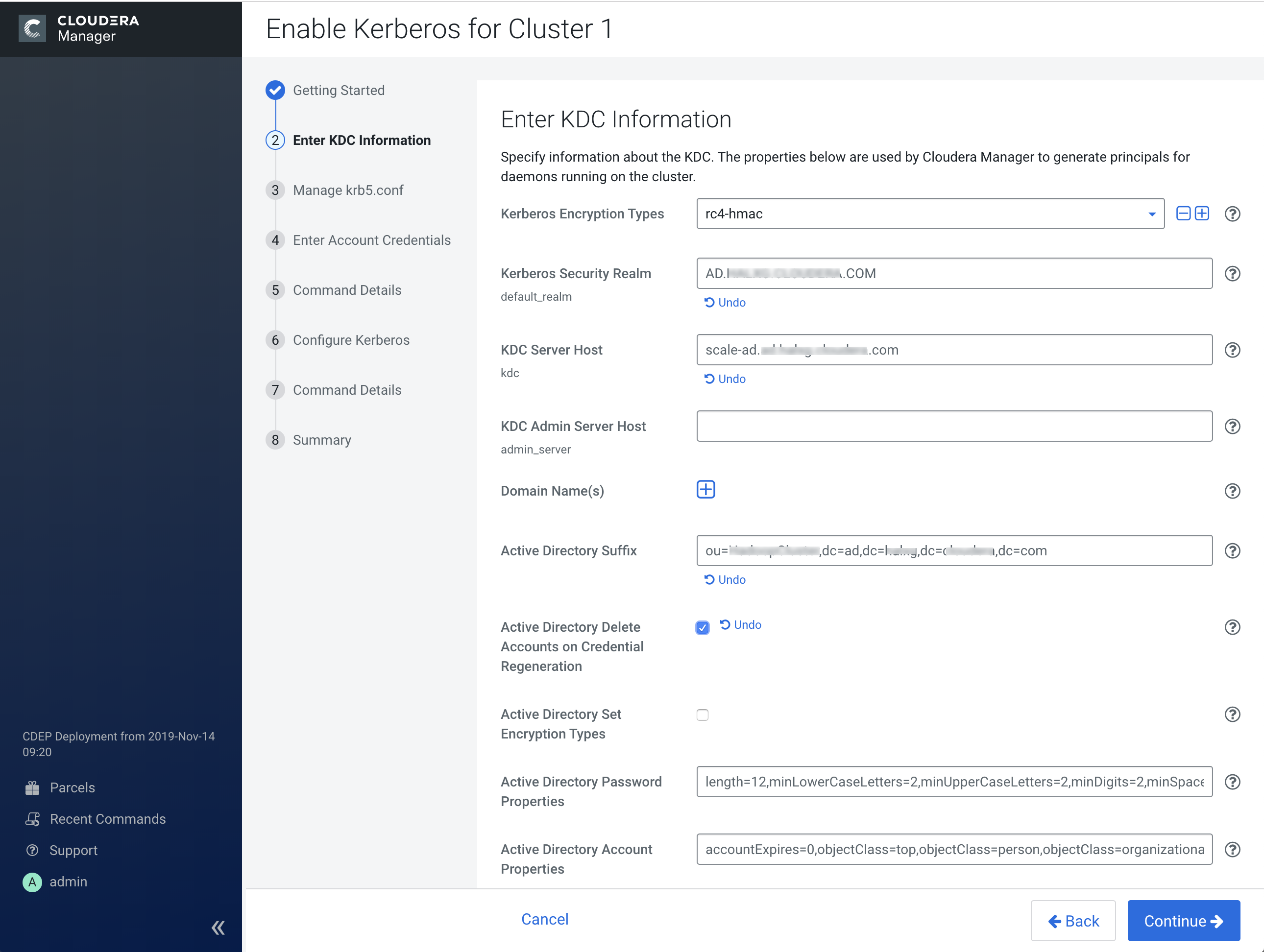
2. Enter KDC Information
Learn about how to enter configuration information for the KDC you are using.
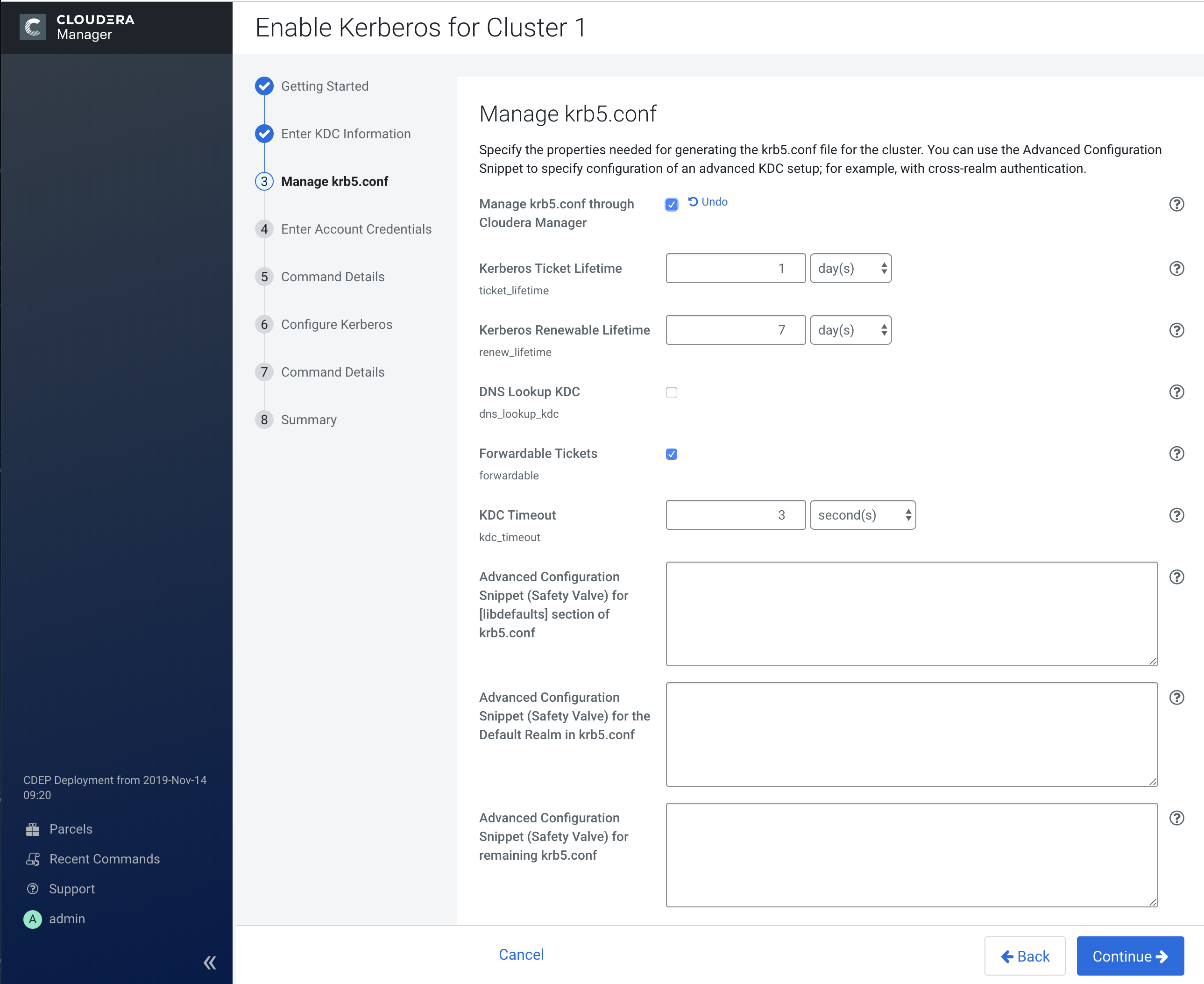
3. Manage krb5.conf
Learn about how to manage the krb5.conf file on your cluster.
You can use this page to specify whether or not Cloudera Manager deploys and manages the
krb5.conf file on your cluster.
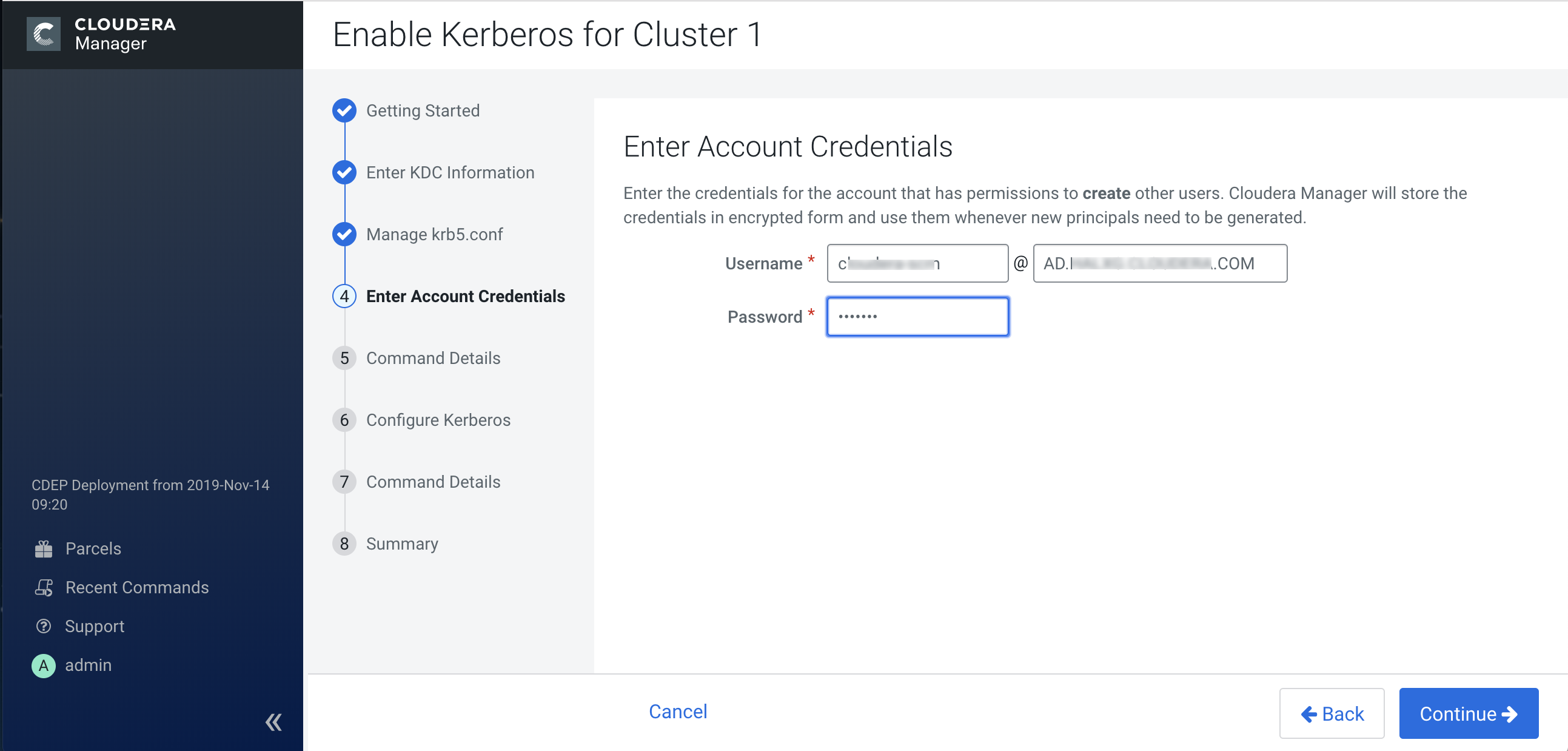
4. Enter Account Credentials
Learn about how to enter account credentials.
5. Command Details
Learn about the command details page.
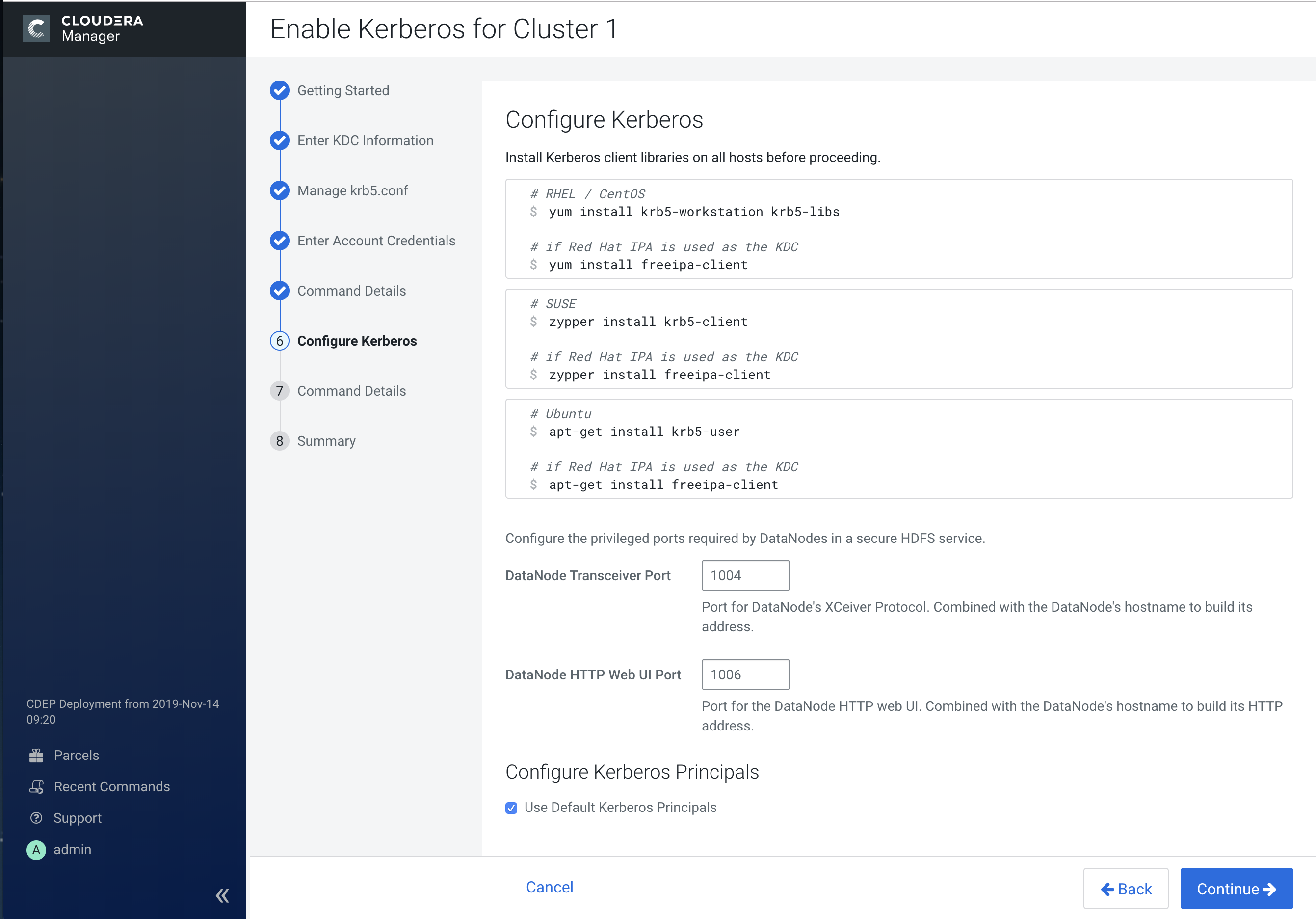
6. Configure Kerberos
Learn about how to configure Kerberos.
7. Command Details
Learn about the outcome of the Enable Kerberos command.
If an error message appears, you can fix the error, then click Resume. In the following example, we select Administration > Settings > Kerberos, then enter an invalid file name in the Custom Kerberos Keytab Retrieval Script box.
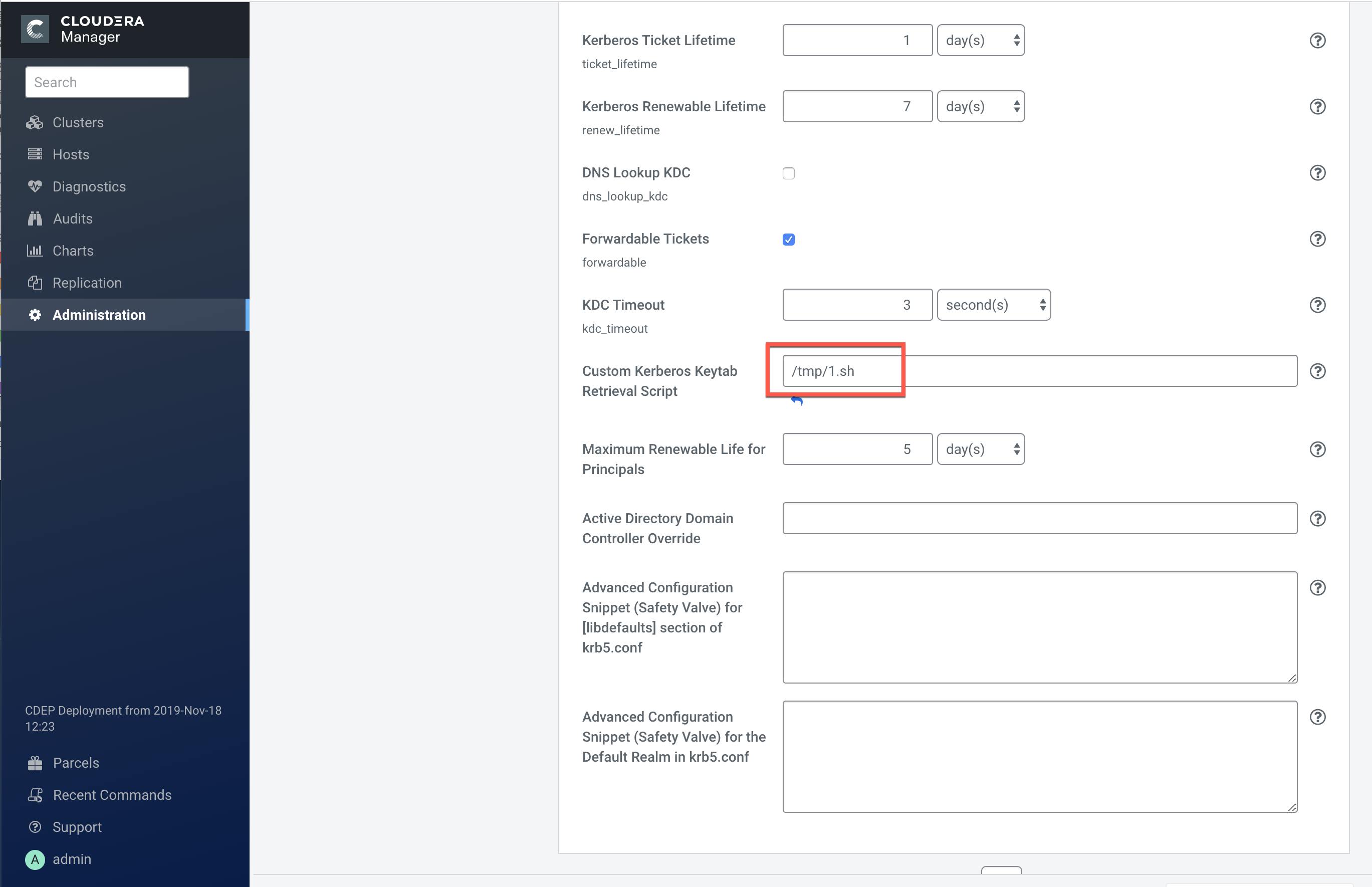
This causes a credential generation error. In this case we can remove the invalid script setting, then click Resume to resume the Enable Kerberos command.
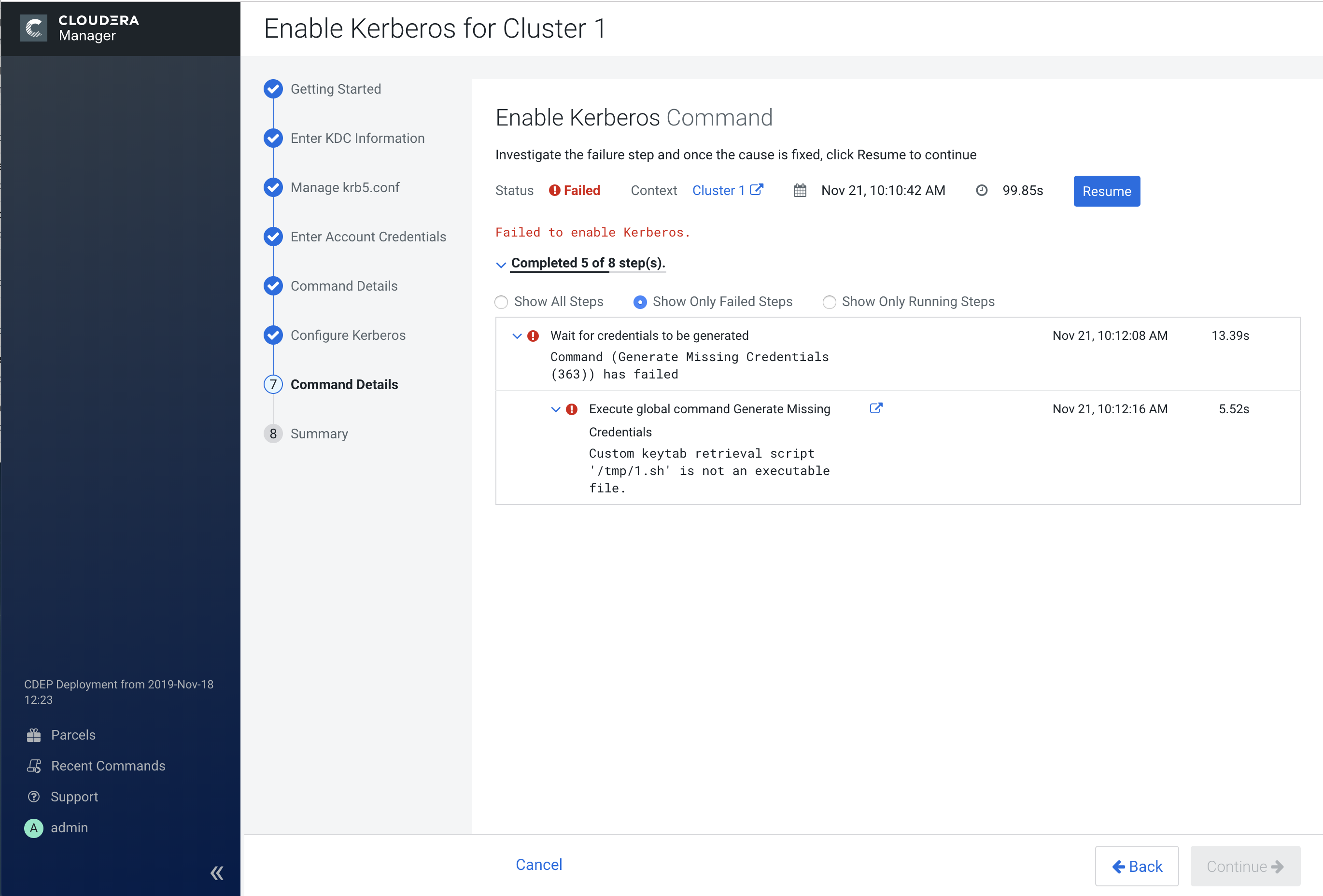
After the command finishes running, click Continue to proceed.
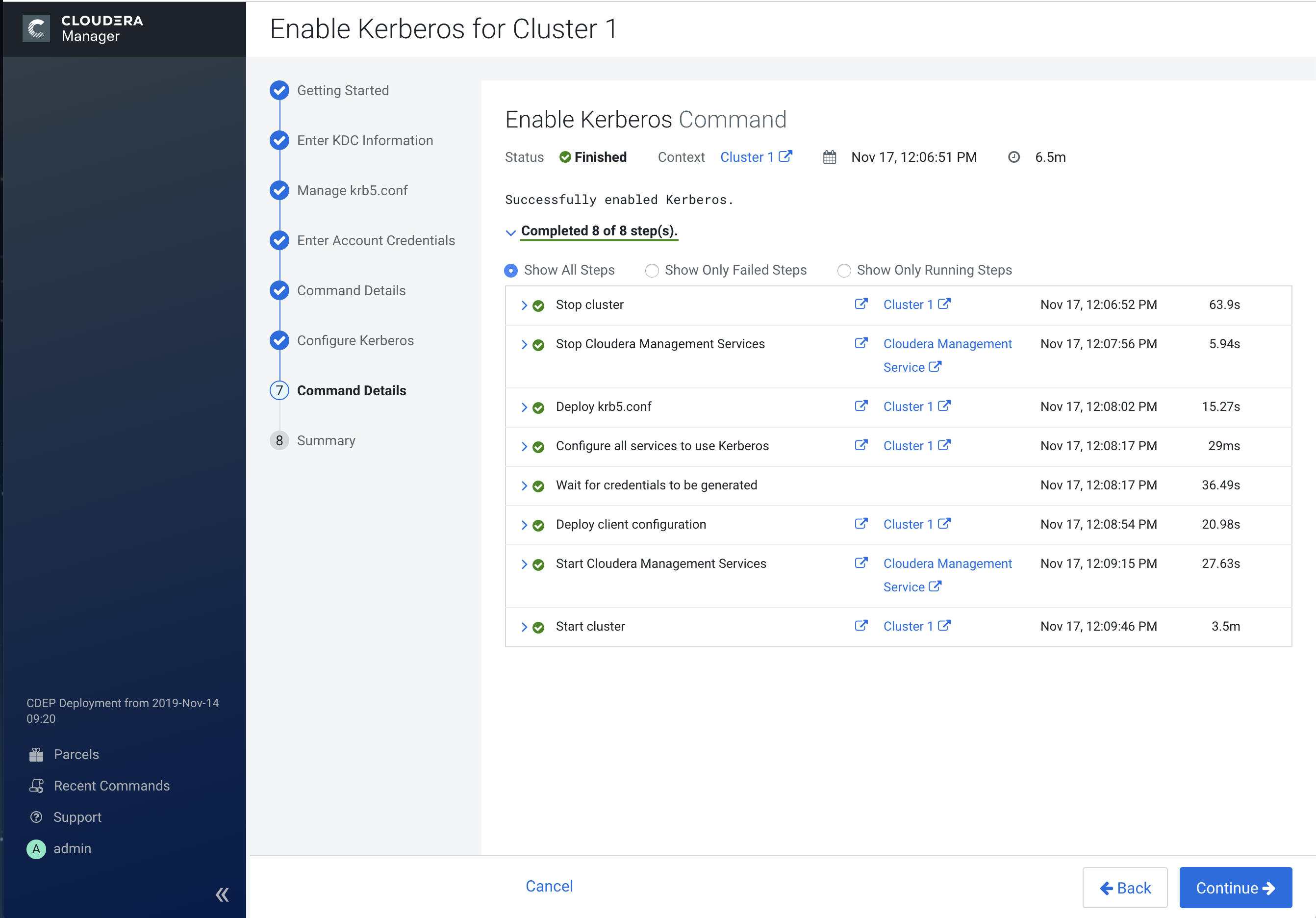
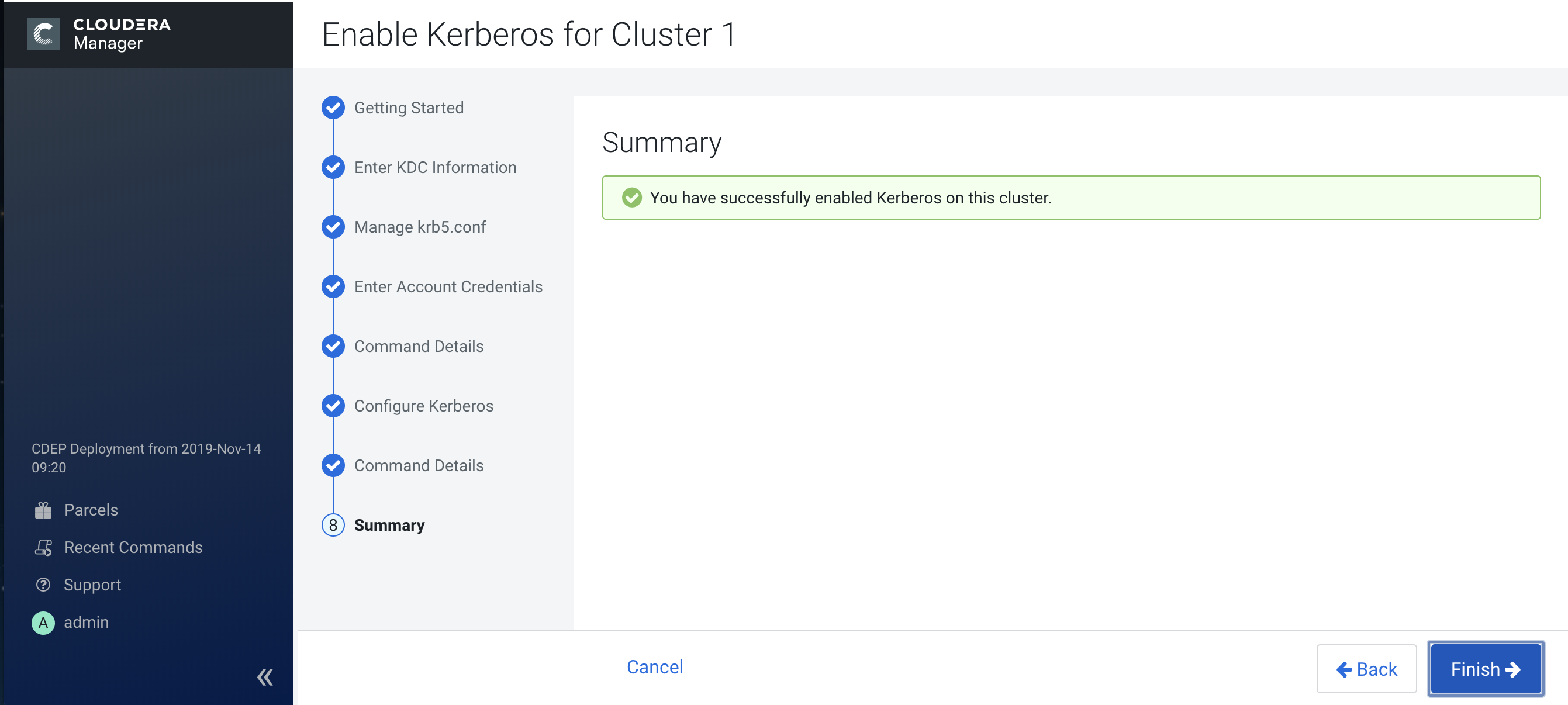
8. Summary
Learn about the summary of the task you performed.
The final step of the wizard lists the cluster(s) for which Kerberos has been successfully enabled. Click Finish to return to the Cloudera Manager Admin Console home page.
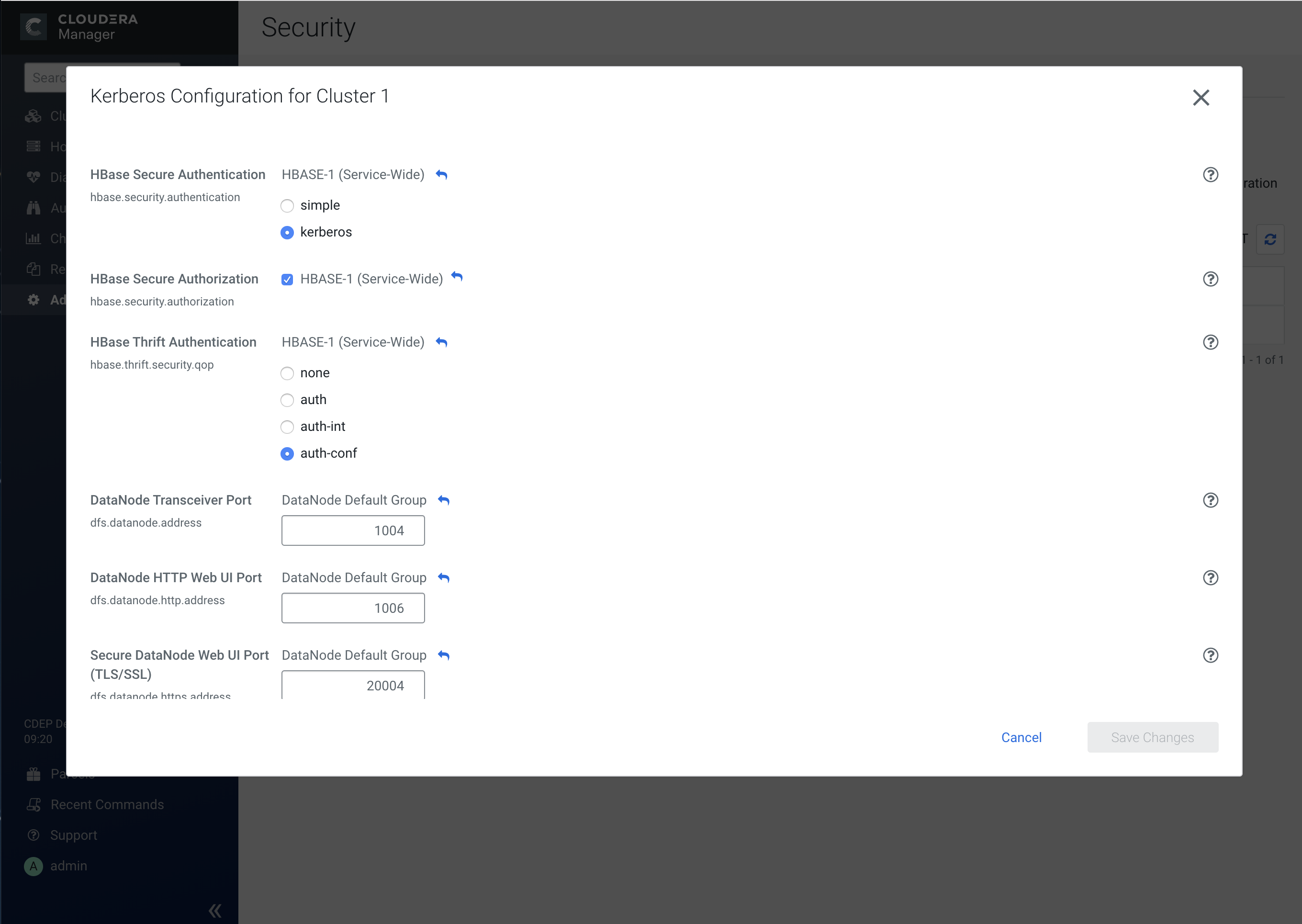
To view details about Kerberos-enabled services, select Administration > Security, then click the applicable row in the Kerberos column.
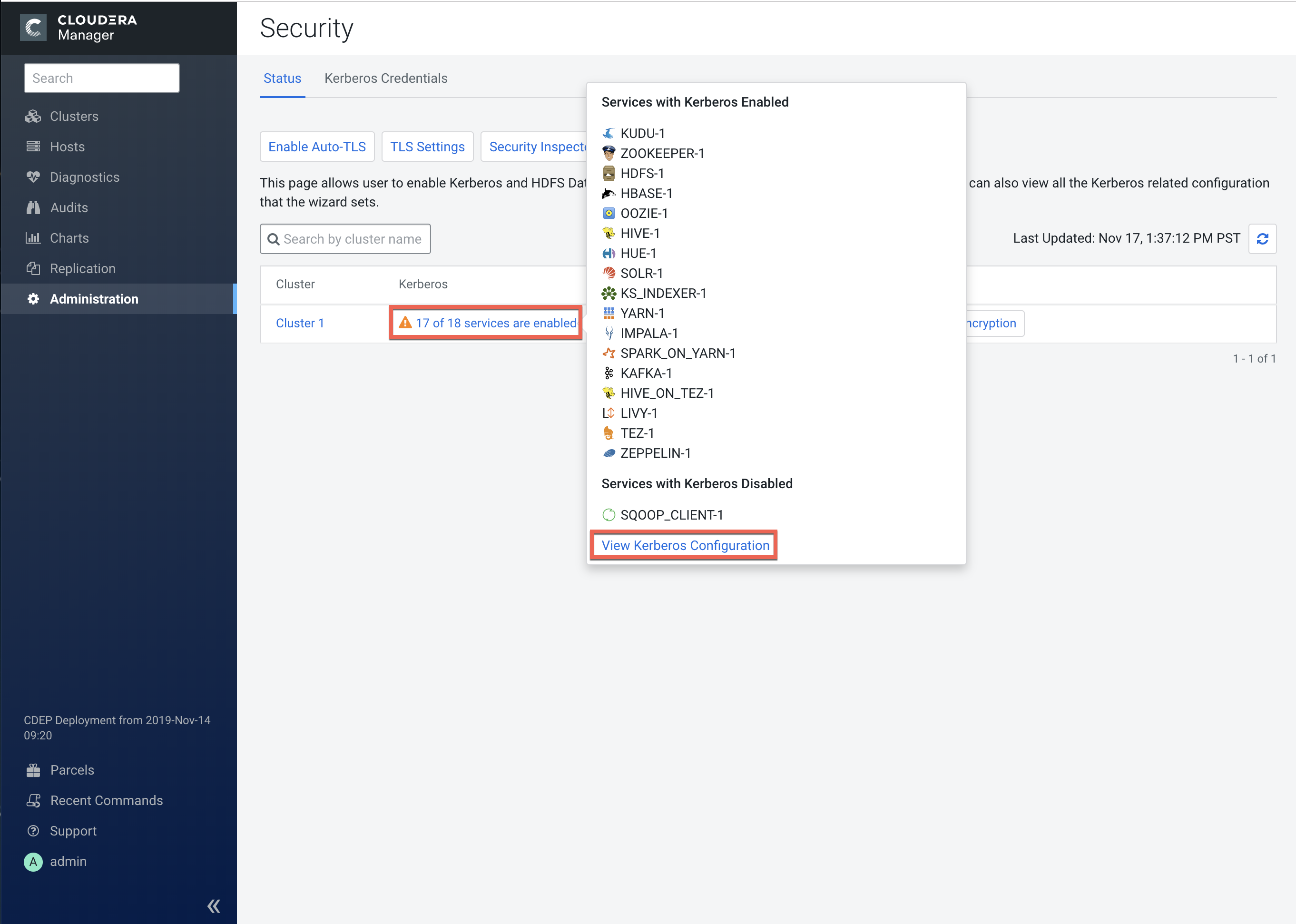
Click View Kerberos Configuration to view and edit configuration details for each service. Click Save Changes to save any configuration updates.