Generate tokens
How to generate Knox gateway tokens from the Knox homepage.
-
To access Knox generation management, go to
https://KNOX_GATEWAY_HOST:PORT/GATEWAY_PATH/homepage/home,
e.g.
https://localhost:8443/gateway/homepage/home. Click on Token Generation.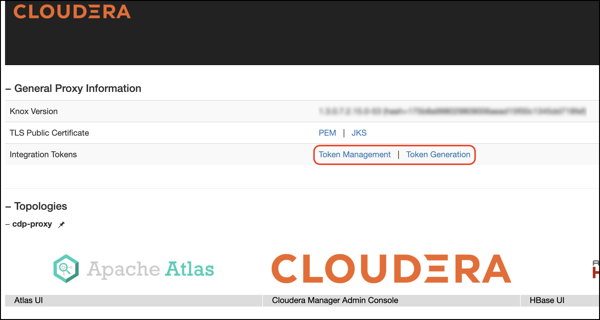
-
The following sections are displayed on the page:
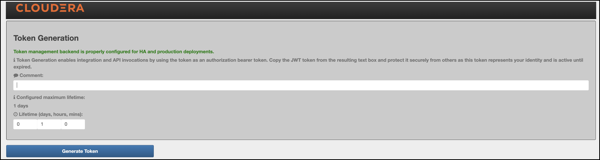
- Status bar: Message about the configured token state backend. There are
3 different statuses:
- ERROR: Displayed in red. Indicates a problem with the service backend which makes the feature not work. Usually, this is visible when end-users configure JDBC token state service, but they make a mistake in their DB settings.
- WARN: Displayed in yellow. Indicates that the feature is enabled and working, but there are some limitations.
- INFO: Displayed in green. Indicates when the token management backend is properly configured for HA and production deployments.
- Information label: Explains the purpose of the Token Generation page.
- Comment: Optional input field that allows end-users to add meaningful comments (mnemonics) to their generated tokens. The maximum length is 255 characters.
- Configured maximum lifetime: Informs the clients about the
knox.token.ttlproperty set in thehomepagetopology (defaults to 1 day(s)). If that property is not set (e.g. someone removes it from he homepage topology), Knox uses a hard-coded value of 30 seconds (aka. default Knox token TTL). - Custom maximum (token) lifetime: Can be set by adjusting the days/hours/minutes fields. The default configuration will yield one hour.
If Knox Token Integration - Enable Impersonation is set to true, another input field is shown on the UI called Generating token for (impersonation).
Using that input field our customers should be able to generate tokens on behalf of other users. For this to work, the Knox Token Integration - Proxyuser Block property has to be configured properly.
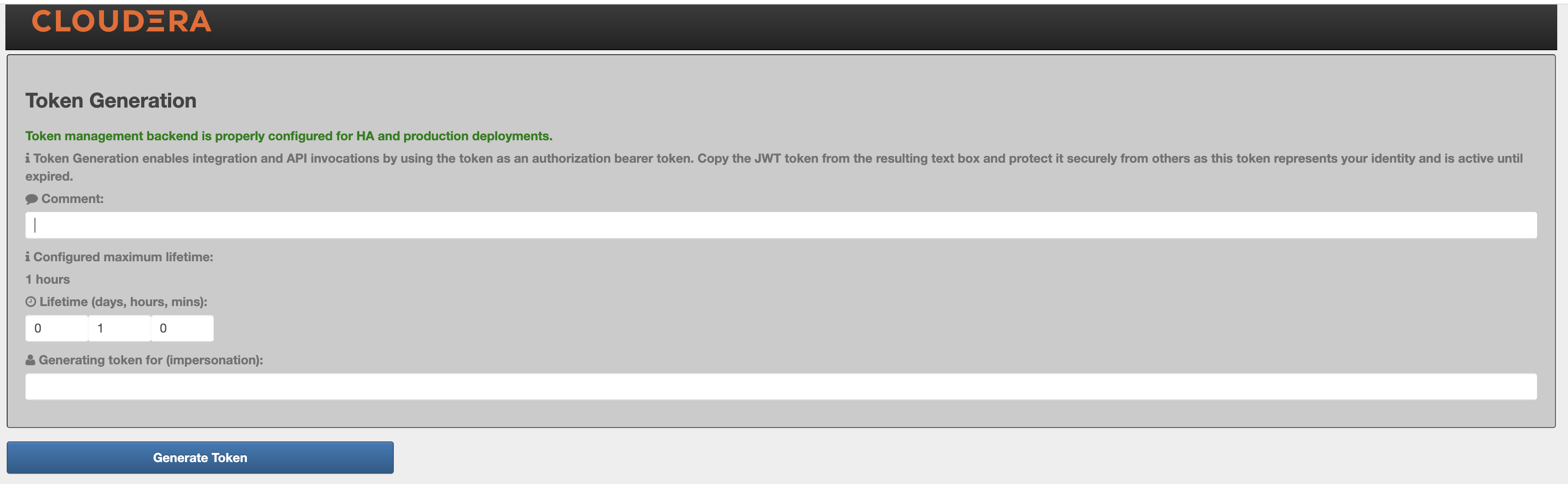
For more information, see Knox Apache User-guide: Token impersonation
- Status bar: Message about the configured token state backend. There are
3 different statuses:
-
Click Generate Token.
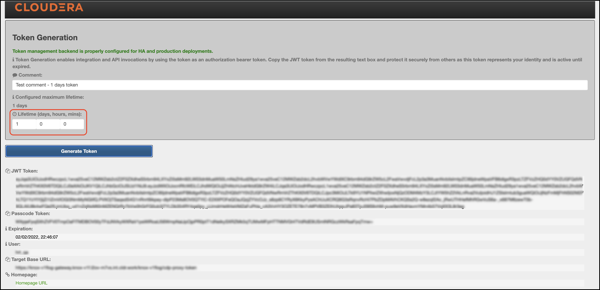
-
Use the token to authenticate your request. Click the icon beside your choice
on the page to copy the value to the clipboard:
- JWT token: serialized JWT, fully compatible with the old-style bearer
authorization method. You can use it as the ‘Token’
user:
$ curl -ku Token:eyJqa3U[...]uT5AxQGyMMP3VLGw https:/localhost:8443/gateway/cdp-proxy-token/webhdfs/v1?op=LISTSTATUS {"FileStatuses":{"FileStatus":[{"accessTime":0,"blockSize":0,"childrenNum":1,"fileId":16386,"group":"supergroup", "length":0,"modificationTime":1621238405734,"owner":"hdfs","pathSuffix":"tmp","permission":"1777","replication":0, "storagePolicy":0,"type":"DIRECTORY"},{"accessTime":0,"blockSize":0,"childrenNum":1,"fileId":16387,"group":"supergroup", "length":0,"modificationTime":1621238326078,"owner":"hdfs","pathSuffix":"user","permission":"755","replication":0, "storagePolicy":0,"type":"DIRECTORY"}]}} - Passcode token: Serialized passcode token, which can be used as the
‘Passcode’
user:
$ curl -ku Passcode:WkRFMk1XTmh[...]RVNFpXRTA= https://localhost:8443/gateway/cdp-proxy-token/webhdfs/v1?op=LISTSTATUS {"FileStatuses":{"FileStatus":[{"accessTime":0,"blockSize":0,"childrenNum":1,"fileId":16386,"group":"supergroup", "length":0,"modificationTime":1621238405734,"owner":"hdfs","pathSuffix":"tmp","permission":"1777","replication":0, "storagePolicy":0,"type":"DIRECTORY"},{"accessTime":0,"blockSize":0,"childrenNum":1,"fileId":16387,"group":"supergroup", "length":0,"modificationTime":1621238326078,"owner":"hdfs","pathSuffix":"user","permission":"755","replication":0, "storagePolicy":0,"type":"DIRECTORY"}]}}
- JWT token: serialized JWT, fully compatible with the old-style bearer
authorization method. You can use it as the ‘Token’
user:
