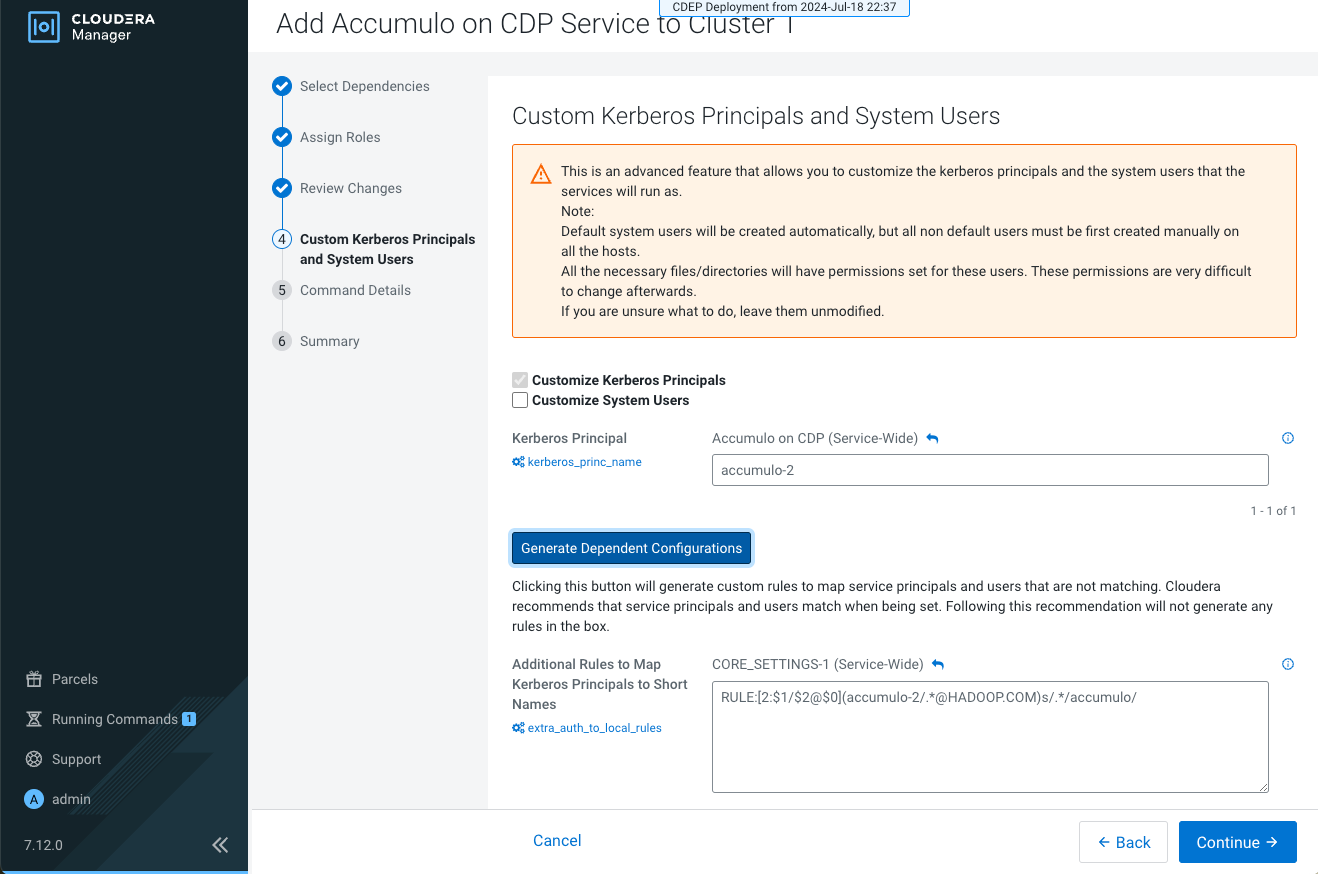
Customizing Kerberos Principals
The custom Kerberos principals is an advanced optional feature that allows you to customize the Kerberos principals for the Accumulo service. Learn how to customize the Kerberos principals in the Cloudera Manager.
- Cloudera Manager configures CDP services to use the default Kerberos principal names. Cloudera recommends not changing the default Kerberos principal. Do not change the Kerberos principal for existing clusters and services.
- If your security policies require you to customize the Kerberos principals for services, contact Cloudera Professional Services for additional help. Configuring the recommended solution requires extra steps and automation outside CDP to succeed.
- Use the following steps only when adding a new service to a new cluster created by enabling custom Kerberos principals using Cloudera Manager. Customizing a system username is not supported at the moment.
- Ensure that you are using the latest version of Cloudera Manager. The minimum supported version is CM 7.11.3.0.
- Before customizing the Kerberos principals in the Cloudera Manager, enable the feature flag for custom Kerberos principals before setting up the cluster. See Enabling feature flag for Custom Kerberos Principals and System Users.
- Before adding a new service with custom Kerberos principal, you must use the Ranger UI and update the appropriate policies.
- Add the following
auth-to-localrule in the Additional Rules to Map Kerberos Principals to Short Names property in the HDFS service using Cloudera Manager.RULE:[2:$1/$2@$0](<custom_accumulo_princiapl>/.*@<realm_name>)s/.*/accumulo/Replace the <custom_accumulo_princiapl> and <realm_name> options with the actual values you plan to use during the Accumulo installation.
For more information on adding the
auth-to-localrule, see Using auth-to-local rules to isolate cluster users.