Restricting classifications based on user permission
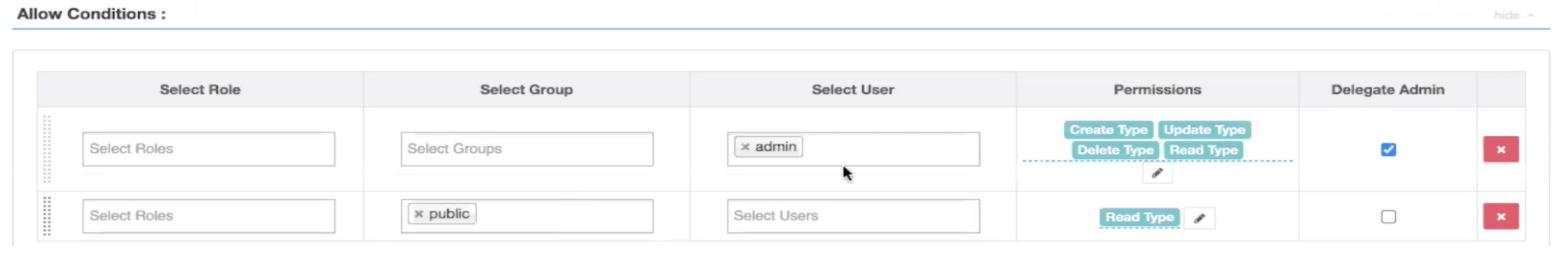
The Apache Atlas authorization model has been updated with a new permission, type-read, to enable restricting visibility of types to specific users, groups, and roles.
Atlas authorization model supports permissions to create, update, delete types, which enables setting up policies to restrict who can perform create, update, delete on types (like classifications, business metadata). Note that all authenticated users were allowed to perform read operation on types.
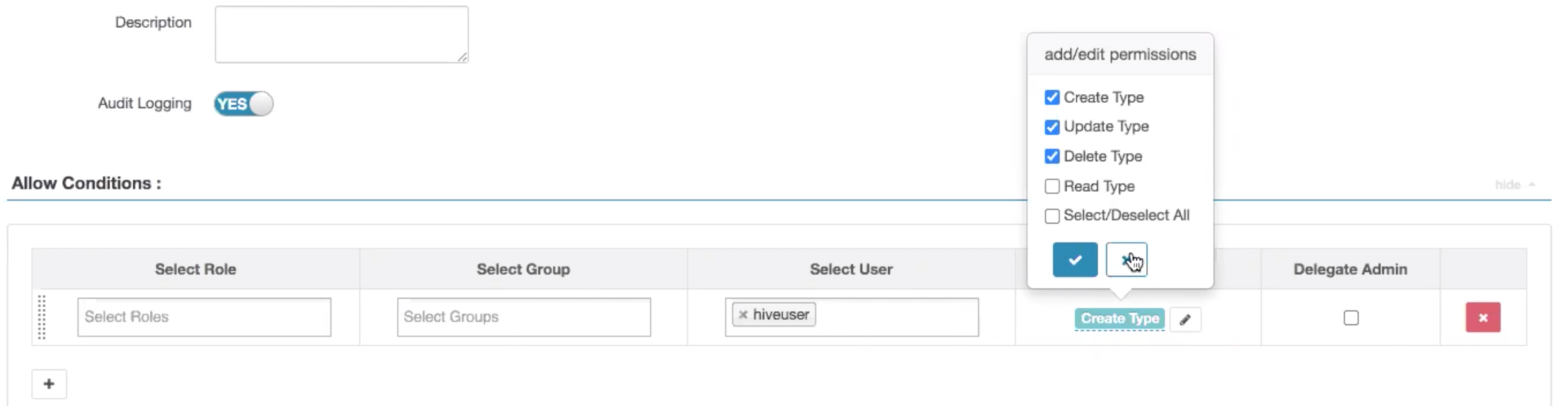
In the updated model, users with type-create or type-update or type-delete permission will implicitly be granted type-read permission. Also, to be compliant with earlier user experience, a default policy is created to allow type-read operation to all authenticated users. Security administrators can update the default policy and add new policies to restrict type-read operation to specific users.
Prior to this update, new permission, the type-read access was not
available and read access for typedefs was public. Now the objective for Read
Type permission is to have the ability to set access control permission
on visibility of classifications and other typedefs (entitydef,
enumdef, structdef, and
business_metadatadef) in Atlas.
Previously, policy permission types only included Create Type, Update Type, and Delete Type.