If your cluster uses Apache Knox for perimeter security in Cloudera Base on premises, you can connect to an Apache Hive
endpoint through Knox. You set the HiveServer transport mode and reference your Java
keystore.
Automate the creation of an internal certificate authority (CA) using Auto-TLS (see link below).
Set up SSL, including trust, for Knox Gateway clients.
-
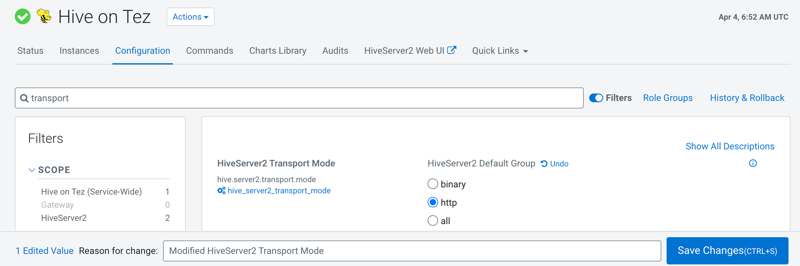
In Cloudera Manager, click , and change the Hive on Tez service transport mode in Cloudera Manager to
http.
KNOX discovers the service automatically and builds a proxy URL for Hive on
Tez only when the transport mode is http.
-
Download the
Knox Gateway TLS/SSL client trust store JKS file from Knox, and save it
locally.
You can find the location of the JKS file from value of the Knox property
gateway.tls.keystore.path.
-
In the Hive connection string, include parameters as follows:
jdbc:hive2://<host>:8443/;ssl=true;transportMode=http; \
httpPath=gateway/cdp-proxy-api/hive; \
sslTrustStore=/<path to JKS>/bin/certs/gateway-client-trust.jks; \
trustStorePassword=<Java default password>
In this example, changeit is the Java default password for
the trust store.