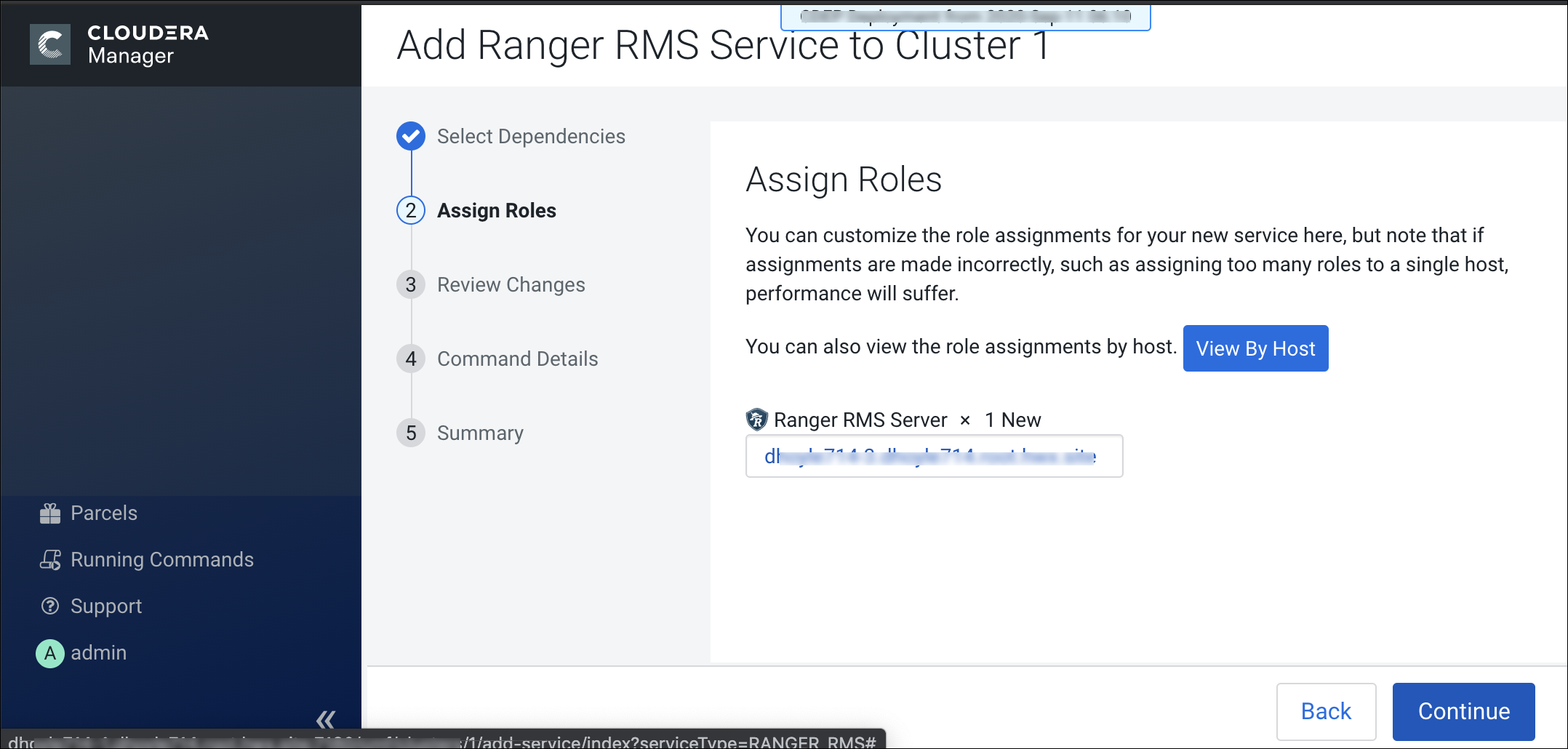
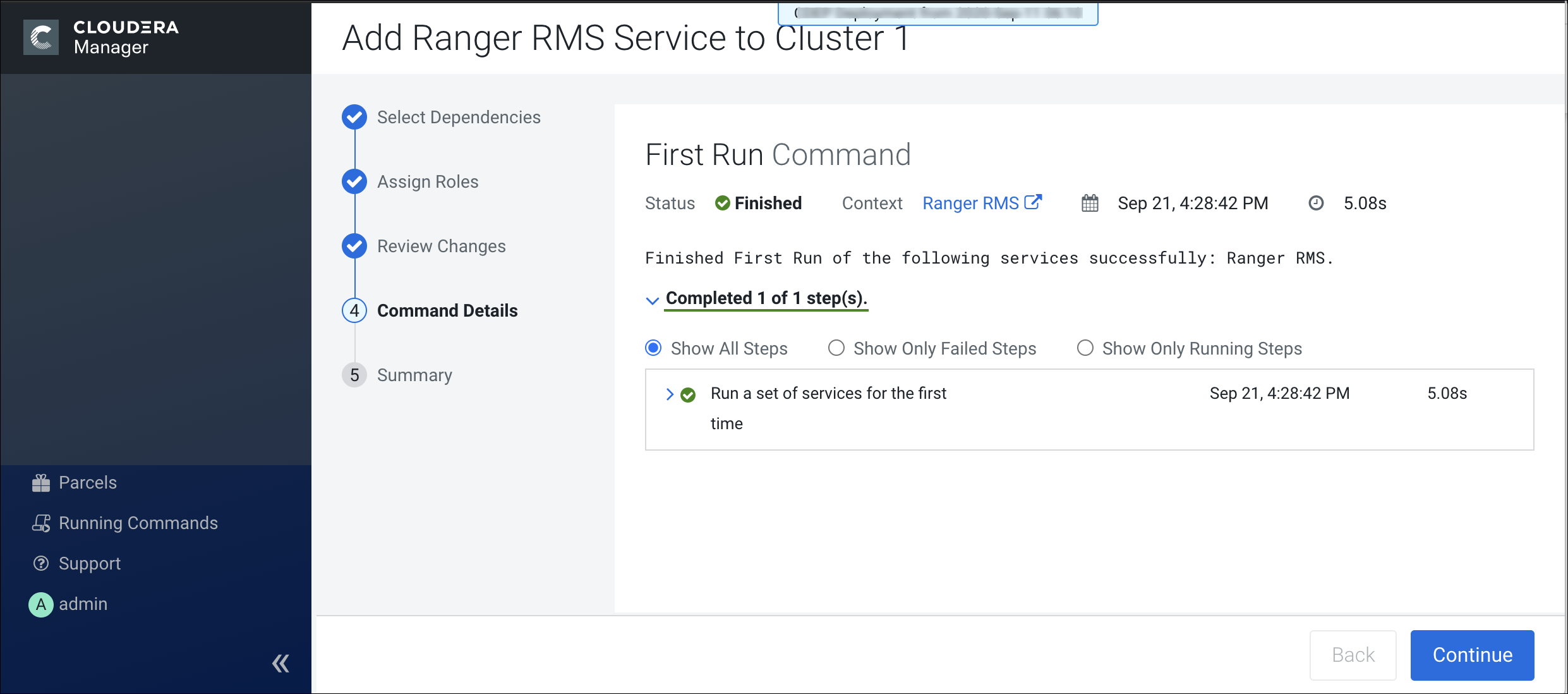
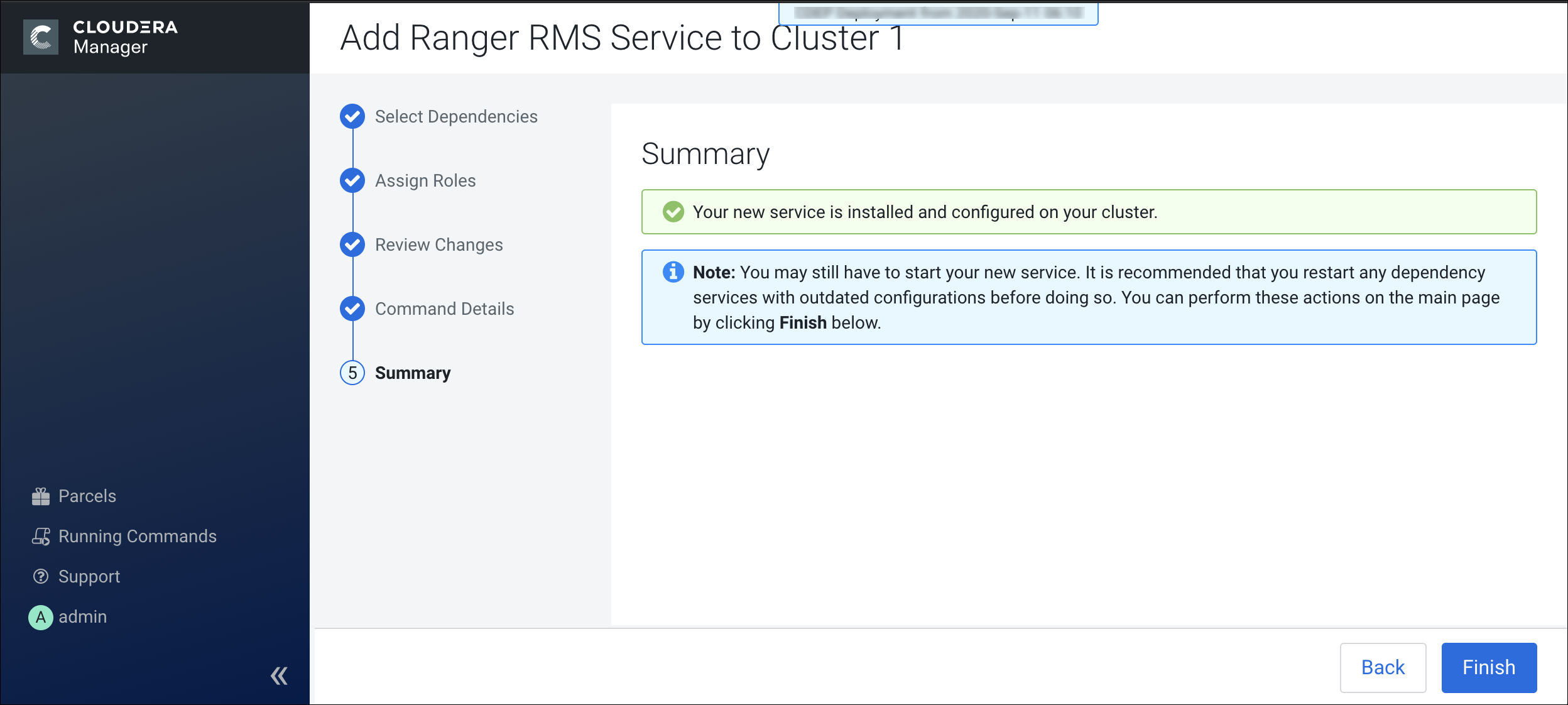
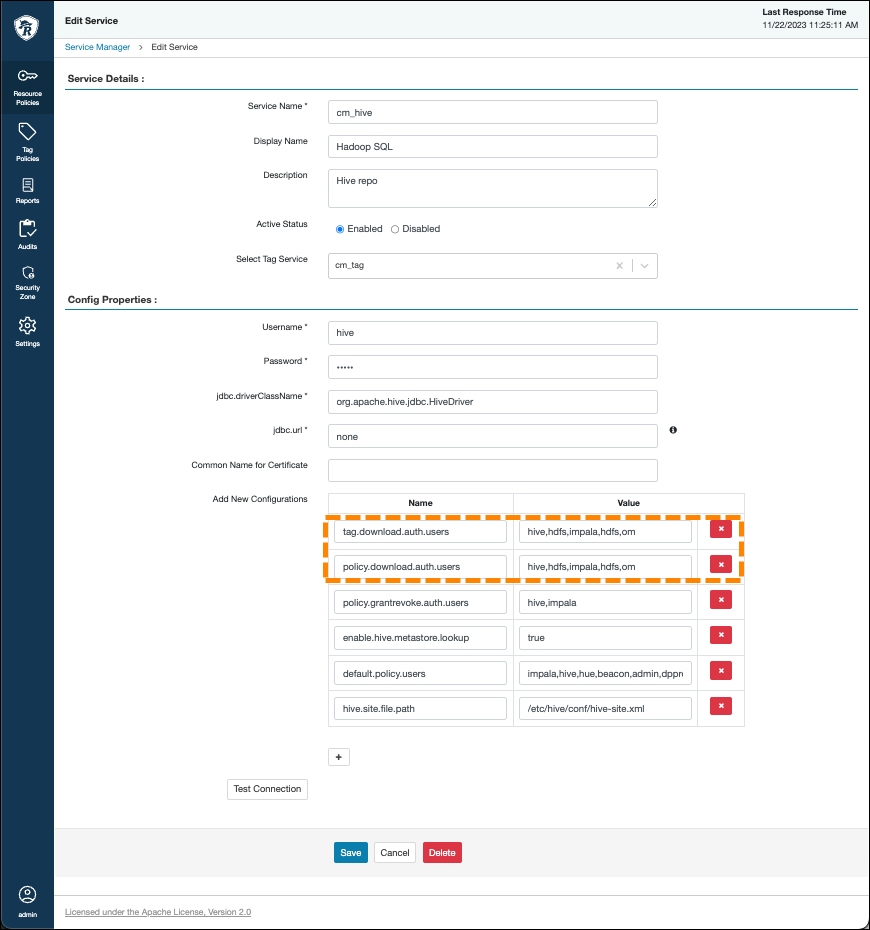
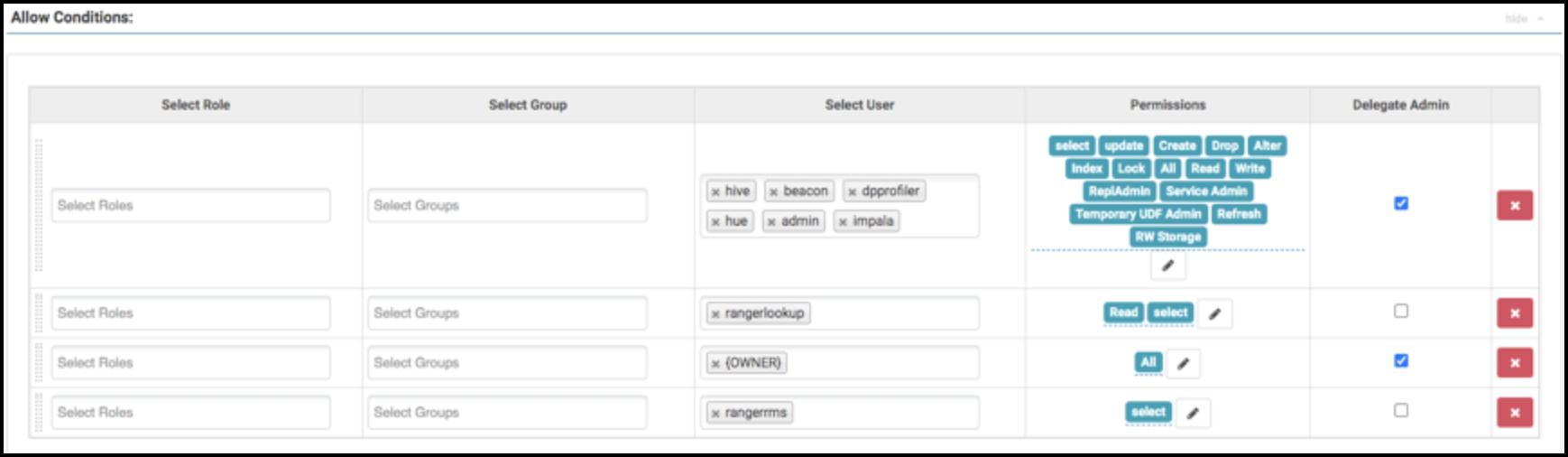
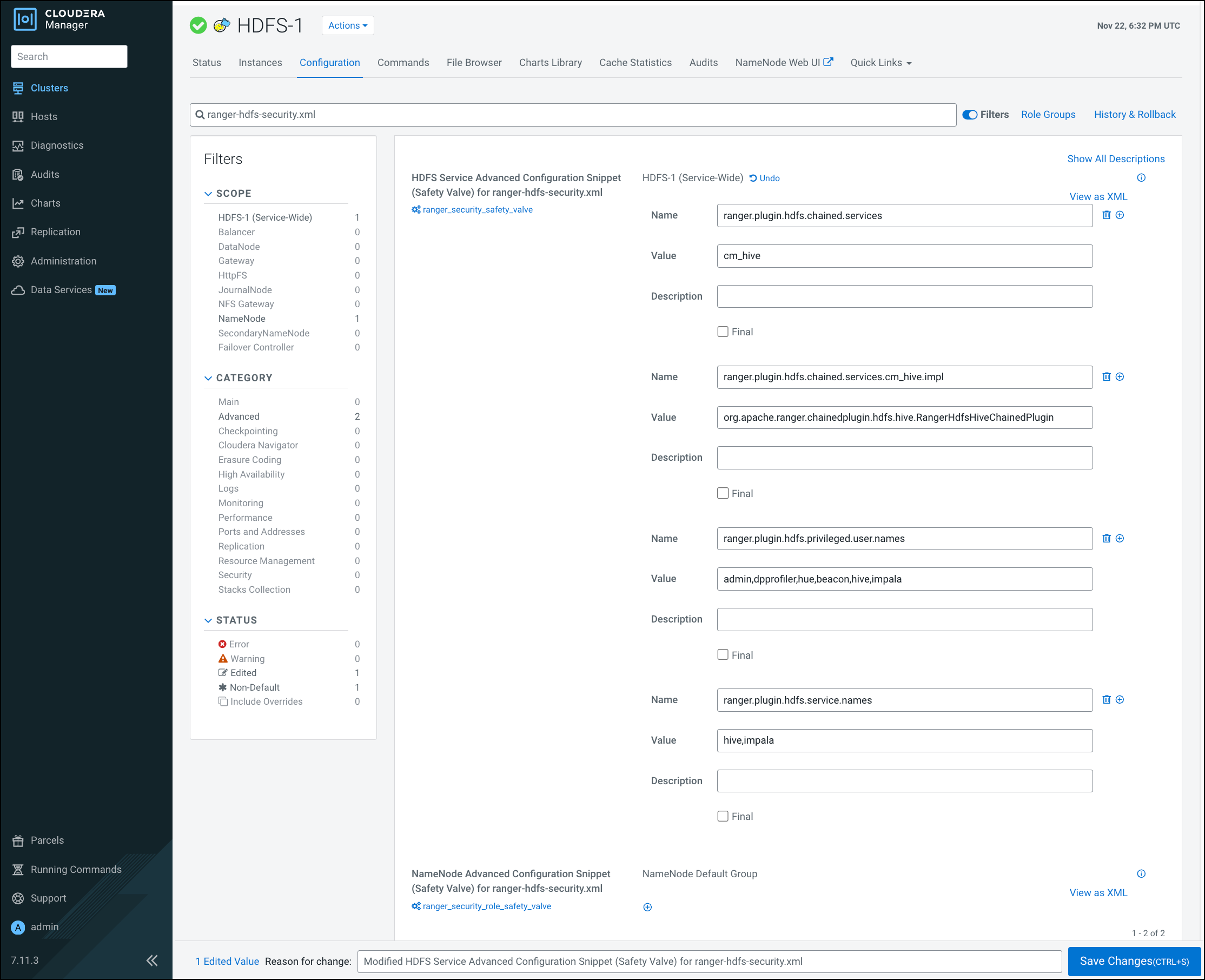
Installing Ranger RMS
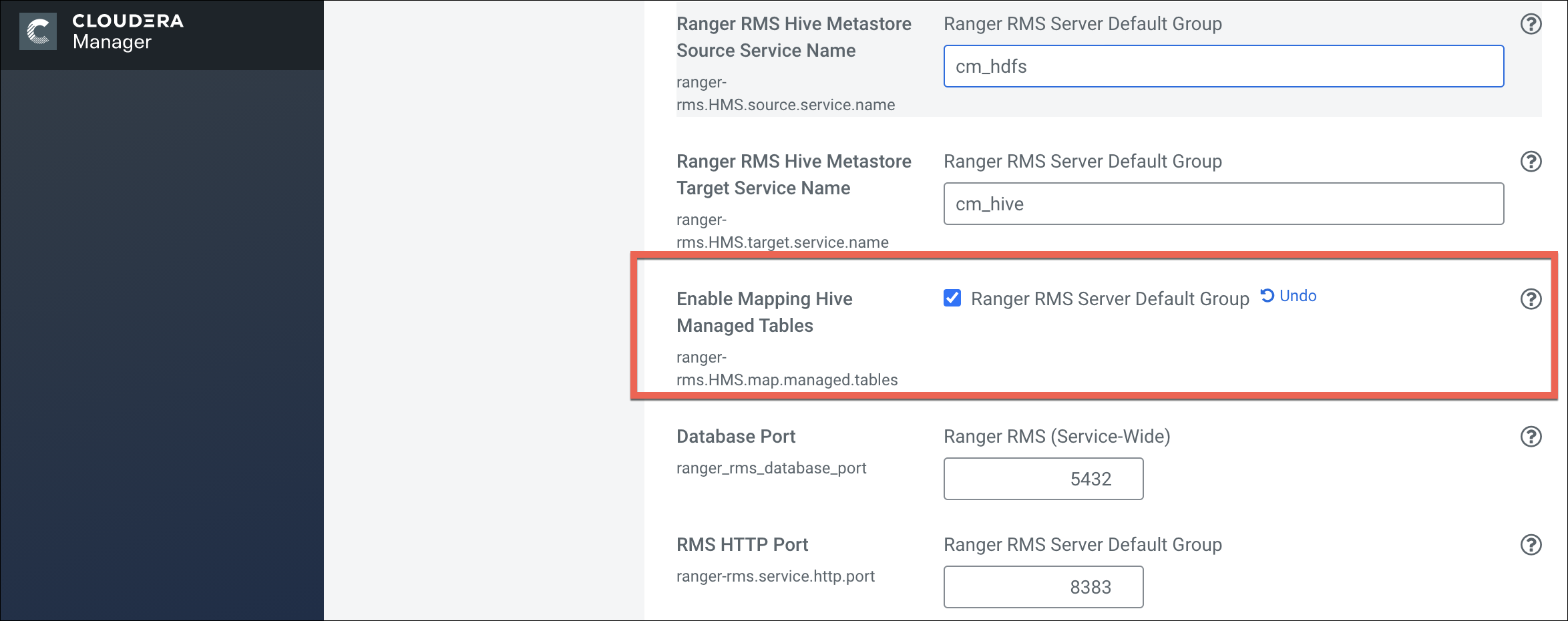
Ranger Resource Mapping Server (RMS) enables automatic translation of access policies from Hive to HDFS.
Legacy CDH users used Hive policies in Apache Sentry that automatically linked Hive permissions with HDFS ACLs. This was especially convenient for external table data used by Spark or Hive.
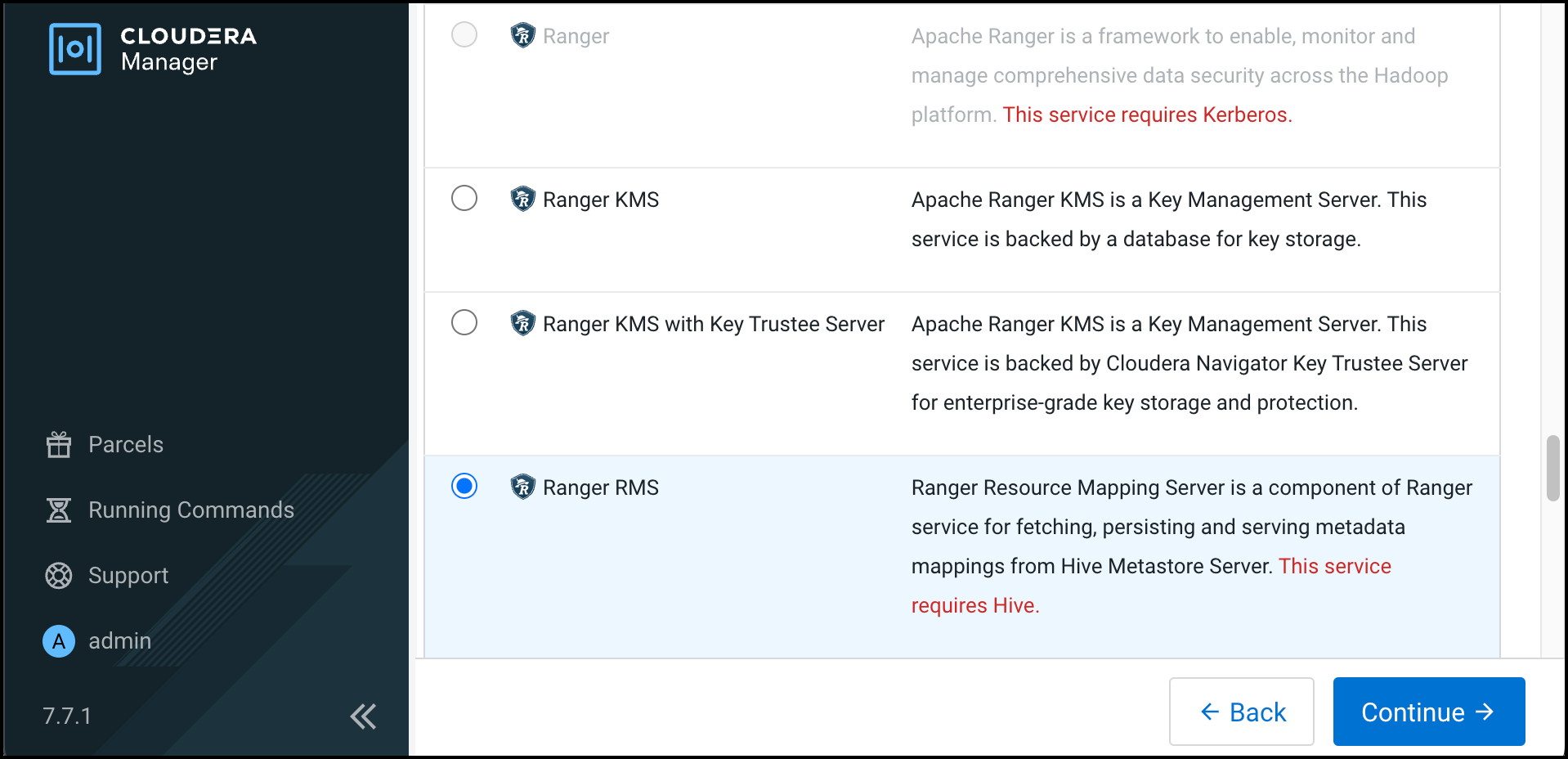
Previously, Ranger only supported managing Hive and HDFS policies separately. Ranger RMS
(Resource Mapping Server) allows you to authorize access to HDFS directories and files using
policies defined for Hive tables. RMS is the service that enables Hive-HDFS ACL Sync.
You must have installed:
- A CDP Private Cloud Base 7.1.4 or higher version cluster with Apache Ranger, Hive, and HDFS.
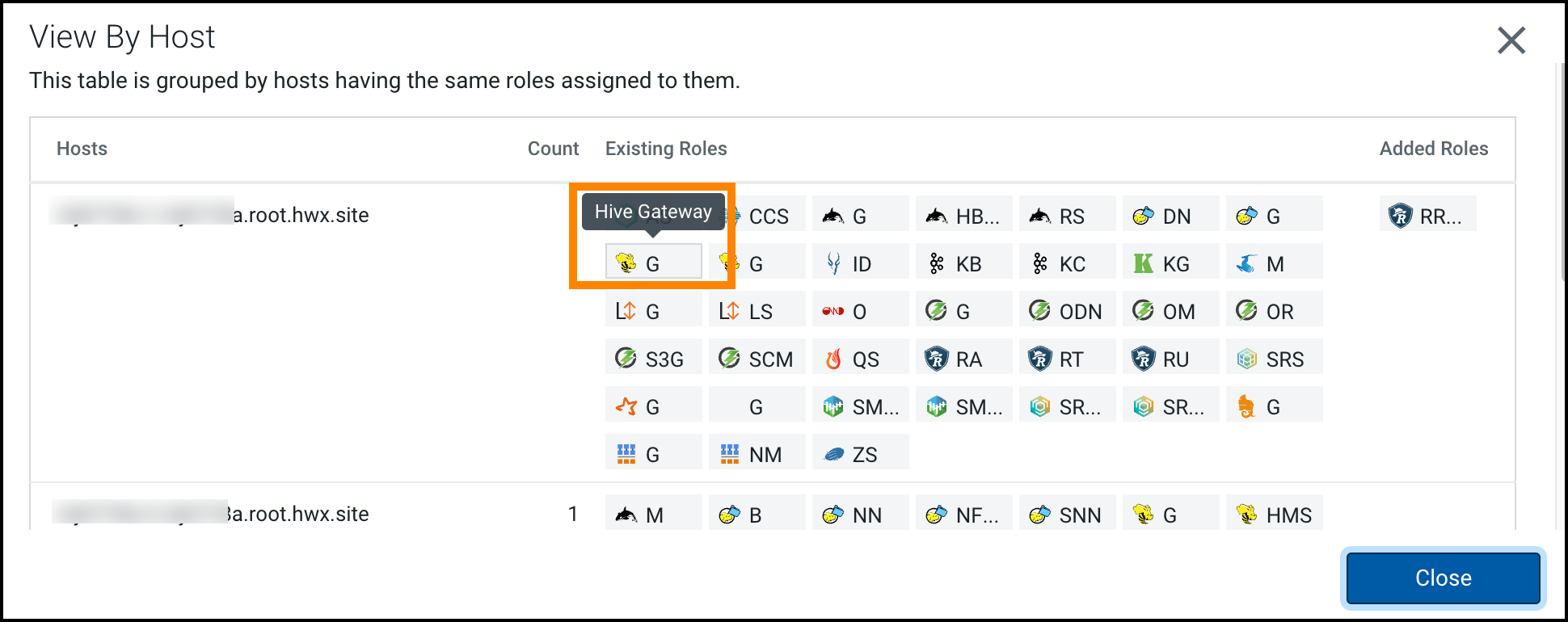
- Ranger RMS on the host where Hive_Gateway is available.
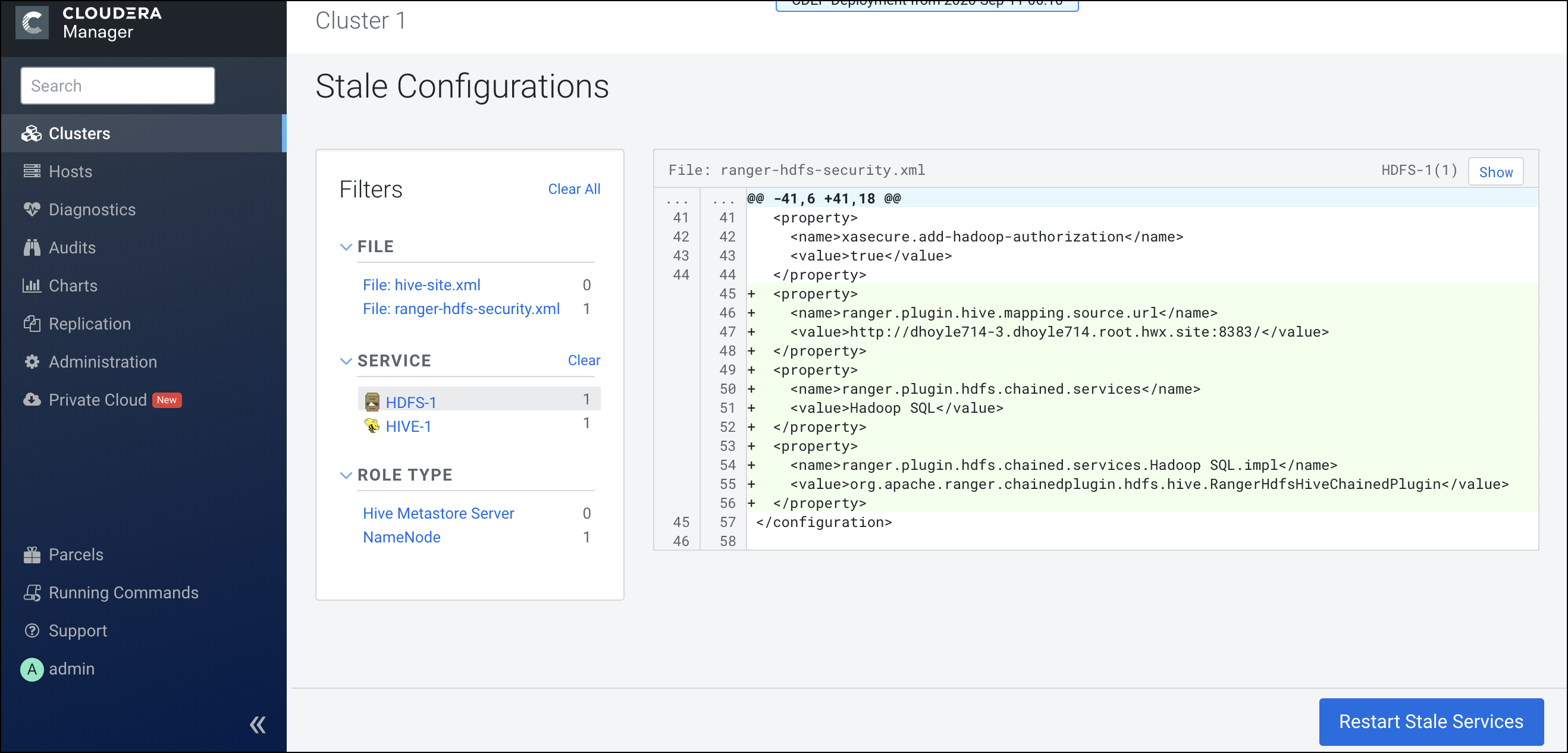
 , then click
, then click