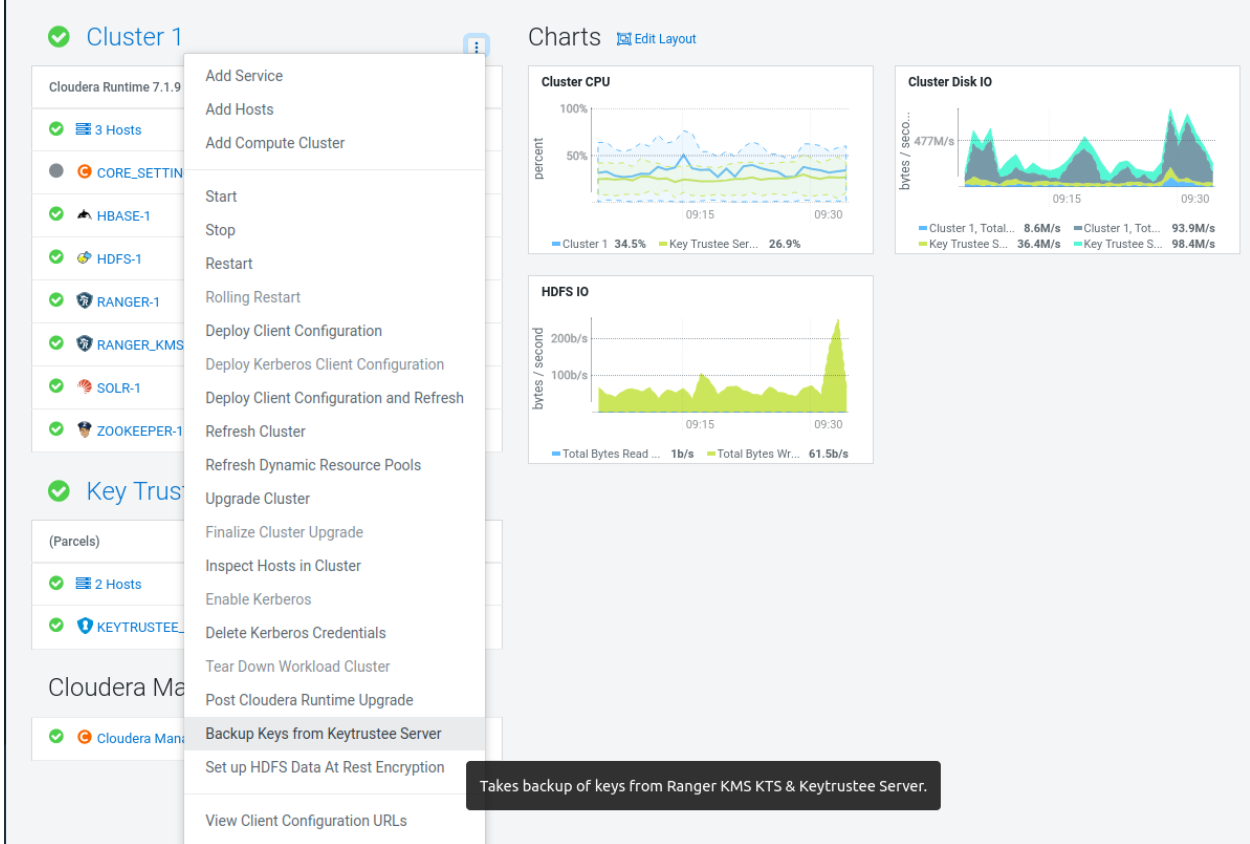
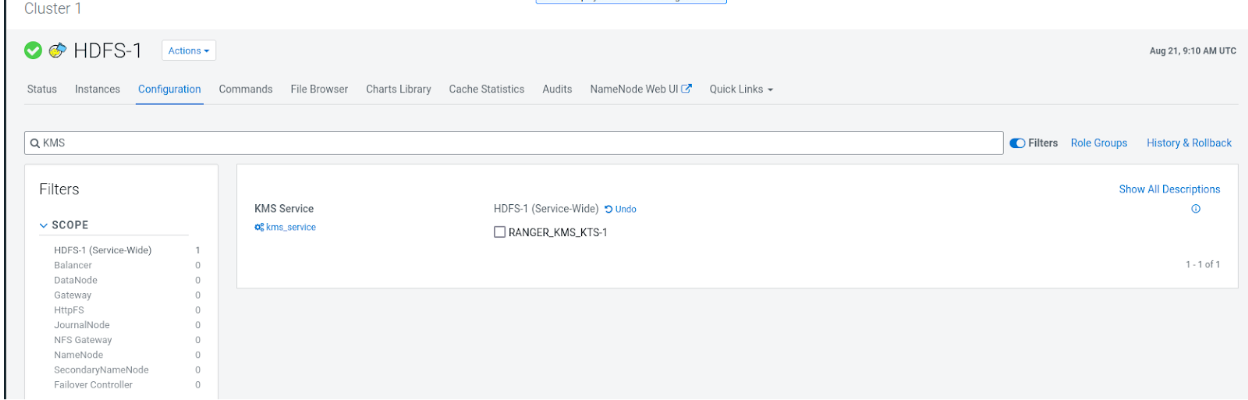
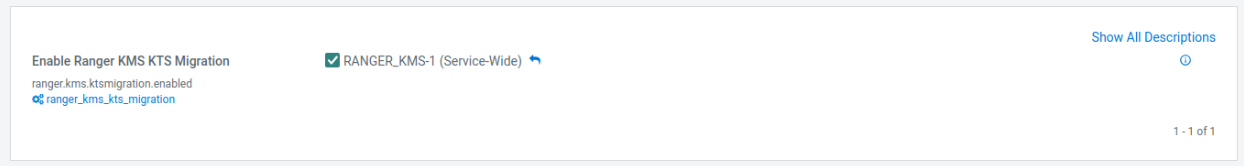
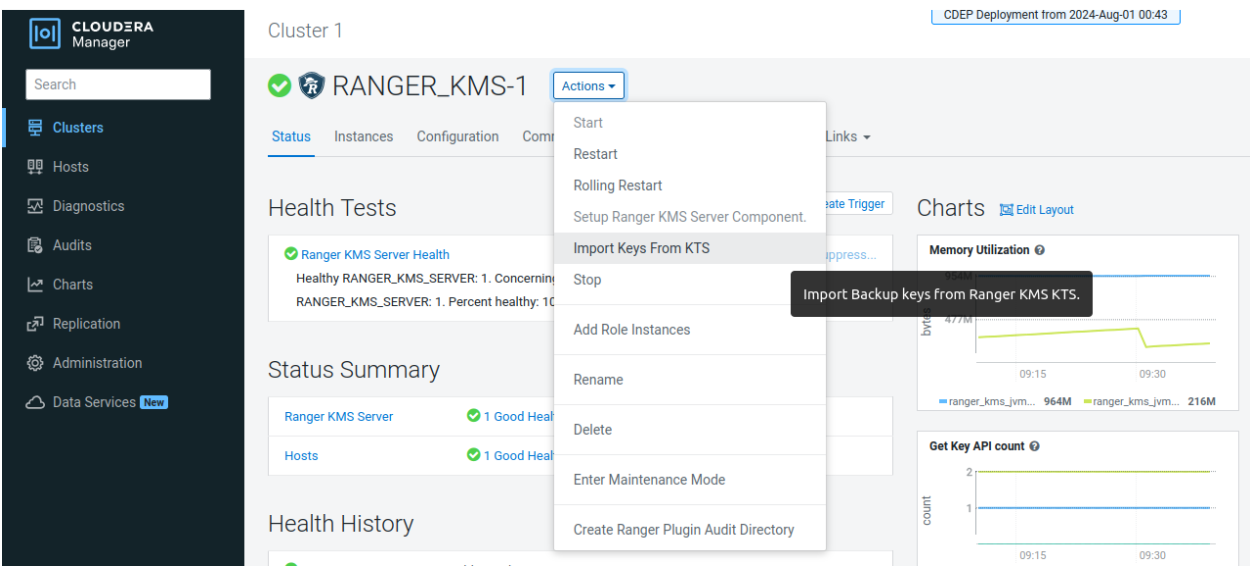
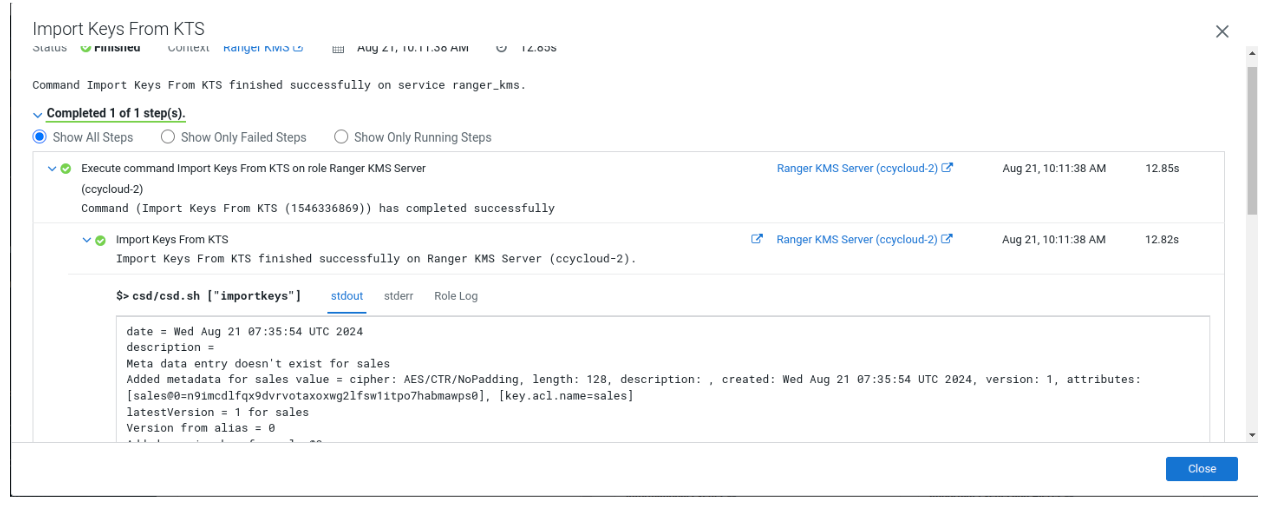
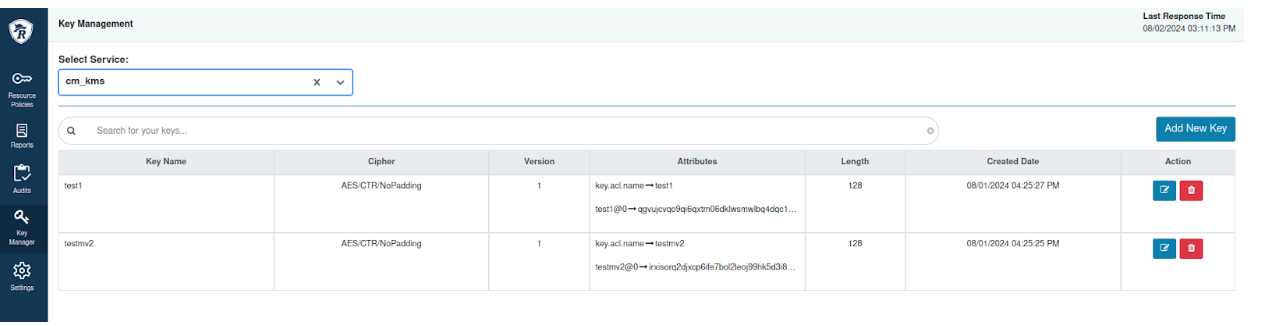
Key migration in 7.3.x
Learn how to migrate keys from Key Trustee Server (KTS) to Ranger KMS if you have already upgraded the Cloudera Manager version and want to upgrade the Cloudera version to 7.3.1 and above.
To upgrade your Cloudera version to 7.3.1 and above, you first need to upgrade to Cloudera Runtime 7.1.9. After you upgrade to Cloudera Runtime 7.1.9, you need to migrate your keys from KTS to Ranger KMS. After you migrate your keys, you can upgrade the Cloudera version to 7.3.1 and above from Cloudera Manager.
If you have upgraded your Cloudera Manager version, and
proceed to upgrade your Cloudera version to 7.3.1
and above without migrating your keys from KTS to Ranger KMS, the following
validation appears on the upgrade wizard
page:
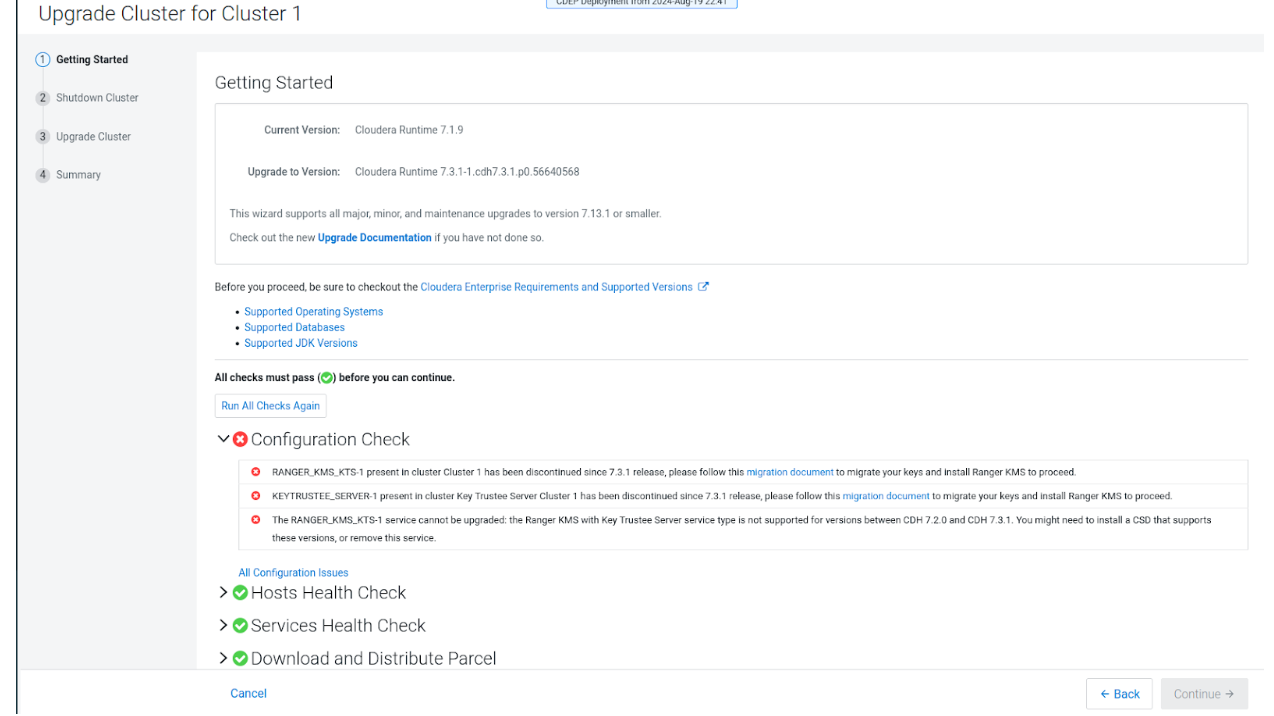
<service_name> in cluster <cluster_name> has been discontinued since 7.3.1 release, please follow this Migration doc to migrate your keys and install Ranger KMS to proceed. Note that if you are using an HSM, you cannot proceed with an upgrade at this time.Please read through and understand the root cause.
- Root Cause
- Services mentioned in the cluster are no longer supported in Cloudera 7.3.1 and have to be
uninstalled before upgrading to the new version. Before uninstalling any
services, you must be diligent to migrate any necessary data and keys
stored in the respective services. If KTS service is installed in a
separate cluster other than the one you intend to upgrade, it is
recommended but not compulsory to uninstall this service.
Confirm the presence for keys in HDFS and Navigator Encrypt. Perform the following
steps to locate the keys in KTS:
- Login to Ranger UI with key admin credentials.
- Go to to view the HDFS encryption zone keys with service Ranger KMS KTS.
- If you have setup Navigator Encrypt, locate its keys:
- SSH into the active KTS node.
- Login to Postgres 14.2 database.
- Update the keytrustee user in /etc/passwd
before accessing the database by running the following
command:
sed -i "/keytrustee:x:$( id -u keytrustee ):$( id -g keytrustee ):Keytrustee User:\/var\/lib\/keytrustee:\/sbin\/nologin/c\keytrustee:x:$( id -u keytrustee ):$( id -g keytrustee ):Keytrustee User:\/var\/lib\/keytrustee:\/bin\/bash" /etc/passwd - Run the following commands to locate the
keys:
sudo -u keytrustee LD_LIBRARY_PATH=/opt/cloudera/parcels/KEYTRUSTEE_SERVER/PG_DB/opt/postgres/14.2/lib /opt/cloudera/parcels/KEYTRUSTEE_SERVER/PG_DB/opt/postgres/14.2/bin/psql -p 11381 keytrustee select handle from deposit; handle --------- mykey1 mykey2 control control (6 rows)
After successful verification, proceed to upgrade the Cloudera version from Cloudera Manager.