Validate TLS configurations
If you are upgrading to from CDH to Cloudera Manager 7.4.4 or earlier, you need to validate TLS configurations. By validating TLS, you can avoid upgrade failure by properly configuring Cloudera Manager properties if your clusters are TLS-enabled.
- HDFS NameNode TLS/SSL Trust Store File (namenode_truststore_file)
- HDFS NameNode TLS/SSL Trust Store Password (namenode_truststore_password)
- Hive Metastore TLS/SSL Trust Store File (hive.metastore.dbaccess.ssl.truststore.path)
- Hive Metastore TLS/SSL Trust Store Password (hive.metastore.dbaccess.ssl.truststore.password)
HiveStrictManagedMigration: [main]: Found 0 databases
HiveStrictManagedMigration: [main]: Done processing databasesYou must configure the HDFS and HMS truststore file and password properties after upgrading Cloudera Manager to 7.3.1 or later.
- You completed the upgrade to Cloudera Manager 7.4.4 or earlier.
- Your CDP cluster will be TLS-enabled.
- In Cloudera Manager, to configure HDFS properties click .
- Search for namenode_truststore.
-
Set HDFS NameNode TLS/SSL Trust Store File to
{{CM_AUTO_TLS}}.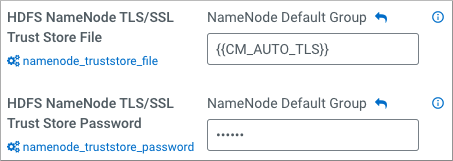
- Set HDFS TLS/SSL Trust Store Password.
- In Cloudera Manager, to configure Hive Metastore properties click .
- Search for hive.metastore.dbaccess.
-
Set Hive Metastore TLS/SSL Trust Store File to
{{CM_AUTO_TLS}}.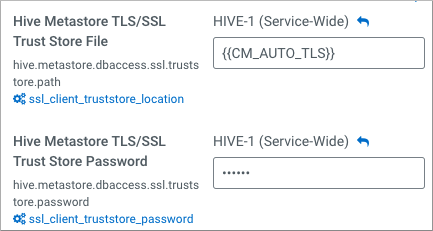
- Set Hive Metastore TLS/SSL Trust Store Password.
- Save changes.
