Create role and policy used to deploy Cloudera environments for Cloudera Data Engineering
The Cloudera Data Engineering control plane requires a role and policies to create Cloudera environments. In this step, you create a common policy for creating environments, as well as a policy that is specific to Cloudera Data Engineering environments.
The following two policies are created in this step:
- Compute infrastructure restricted IAM policy - A common policy for all data services deployed on Cloudera.
- Cloudera Data Engineering restricted IAM policy - A policy with additional permissions for Cloudera Data Engineering.
There are two options for the timing of attaching the role: during environment creation, or prior to enabling the Cloudera Data Engineering data service.
Option #1: During environment creation
The Cloudbreak environment creation UI should be set up as shown here:
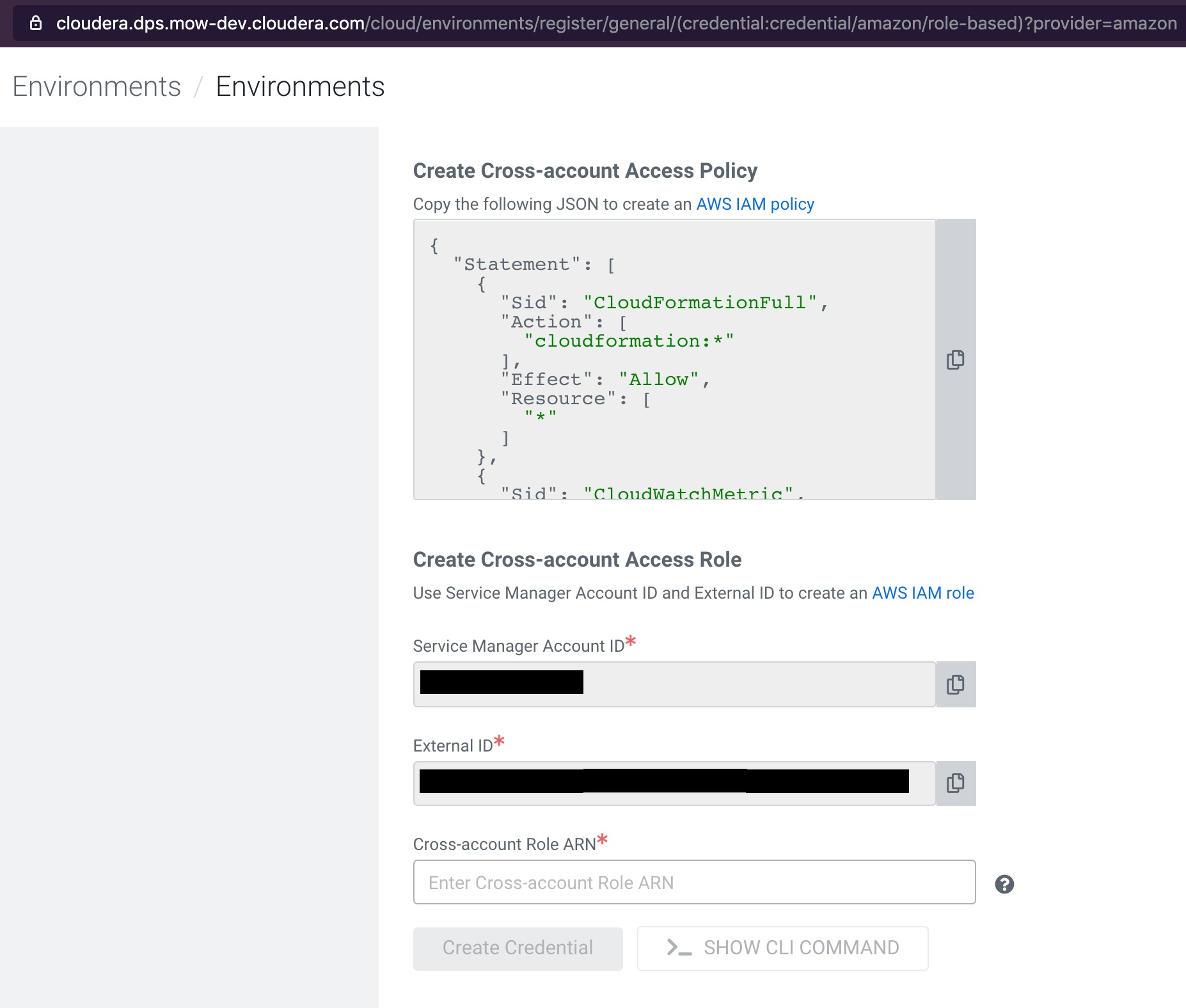
Option #2: Prior to enabling Cloudera Data Engineering data service
If the Cloudbreak environment has already been created, you can create and attach the Compute infrastructure Restricted IAM policy and Cloudera Data Engineering restricted IAM policy to the existing cross-account role associated with the environment.
To view the existing cross-account role, in the Environments section of the Cloudera Management Console, on the Summary tab, see Credentials.
Compute (Liftie) Restricted IAM policy
- [YOUR-ACCOUNT-ID] with your account ID in use.
- [YOUR-IAM-ROLE-NAME] with the IAM restricted role associated with this policy.
- [YOUR-SUBNET-ARN-*] supplied during the Cloudbreak Environment(s) creation. Note: Please provide all the subnets present in all the Cloudbreak Environment(s) that you intend to use it for the experience. If at any point a new Cloudbreak Environment is created or an existing one is updated for subnets, the same should be updated here.
- [YOUR-IDBROKER-ROLE-NAME] with the ID Broker Role name in use.
- [YOUR-LOG-ROLE-NAME] with the Log Role name in use.
- [YOUR-KMS-CUSTOMER-MANAGED-KEY-ARN] with KMS key ARN.
- [YOUR-ACCOUNT-REGION] with the AWS region.
{
"Version": "2012-10-17",
"Id": "ComputePolicy_v12",
"Statement": [
{
"Sid": "SimulatePrincipalPolicy",
"Effect": "Allow",
"Action": [
"iam:SimulatePrincipalPolicy"
],
"Resource": [
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/[YOUR-IAM-ROLE-NAME]"
]
},
{
"Sid": "RestrictedPermissionsViaClouderaRequestTag",
"Effect": "Allow",
"Action": [
"cloudformation:CreateStack",
"cloudformation:CreateChangeSet",
"ec2:createTags",
"eks:TagResource"
],
"Resource": "*",
"Condition": {
"StringLike": {
"aws:RequestTag/Cloudera-Resource-Name": [
"crn:{{ .CRNPartition }}:*"
]
}
}
},
{
"Sid": "RestrictedPermissionsViaClouderaResourceTag",
"Effect": "Allow",
"Action": [
"autoscaling:DeleteTags",
"autoscaling:DetachInstances",
"autoscaling:ResumeProcesses",
"autoscaling:SetDesiredCapacity",
"autoscaling:SuspendProcesses",
"autoscaling:TerminateInstanceInAutoScalingGroup",
"autoscaling:UpdateAutoScalingGroup",
"cloudformation:DeleteChangeSet",
"cloudformation:DeleteStack",
"cloudformation:DescribeChangeSet",
"cloudformation:DescribeStacks",
"cloudformation:CancelUpdateStack",
"cloudformation:ContinueUpdateRollback",
"cloudformation:DescribeStackEvents",
"cloudformation:DescribeStackResource",
"cloudformation:DescribeStackResources",
"cloudformation:ExecuteChangeSet",
"cloudformation:ListStacks",
"cloudwatch:deleteAlarms",
"cloudwatch:putMetricAlarm",
"ec2:AttachVolume",
"ec2:CreateNetworkInterface",
"ec2:CreateVolume",
"ec2:DeleteVolume",
"ec2:RunInstances",
"eks:DescribeUpdate",
"eks:ListUpdates",
"eks:UpdateClusterConfig",
"eks:UpdateClusterVersion",
"iam:GetRolePolicy",
"iam:ListInstanceProfiles",
"iam:ListRoleTags",
"iam:RemoveRoleFromInstanceProfile",
"iam:TagRole",
"iam:UntagRole",
"logs:DescribeLogStreams",
"logs:FilterLogEvents"
],
"Resource": "*",
"Condition": {
"StringLike": {
"aws:ResourceTag/Cloudera-Resource-Name": [
"crn:{{ .CRNPartition }}:*"
]
}
}
},
{
"Sid": "RestrictedPermissionsViaCloudFormation",
"Effect": "Allow",
"Action": [
"autoscaling:CreateAutoScalingGroup",
"autoscaling:CreateLaunchConfiguration",
"autoscaling:CreateOrUpdateTags",
"autoscaling:DeleteAutoScalingGroup",
"autoscaling:DeleteLaunchConfiguration",
"autoscaling:DescribeAutoScalingInstances",
"autoscaling:DescribeLaunchConfigurations",
"autoscaling:DescribeScalingActivities",
"autoscaling:DescribeScheduledActions",
"autoscaling:DescribeTags",
"dynamodb:DescribeTable",
"ec2:AuthorizeSecurityGroupEgress",
"ec2:CreateLaunchTemplate",
"ec2:CreateSecurityGroup",
"ec2:DeleteLaunchTemplate",
"ec2:DeletePlacementGroup",
"ec2:DeleteSecurityGroup",
"ec2:DescribeAccountAttributes",
"ec2:DescribeImages",
"ec2:DescribeInstanceStatus",
"ec2:DescribeInstances",
"ec2:DescribeKeyPairs",
"ec2:DescribeLaunchTemplateVersions",
"ec2:DescribeLaunchTemplates",
"ec2:DescribePlacementGroups",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeVolumes",
"ec2:RevokeSecurityGroupEgress",
"ec2:RevokeSecurityGroupIngress",
"eks:CreateCluster",
"eks:DeleteCluster"
],
"Resource": "*",
"Condition": {
"ForAnyValue:StringEquals": {
"aws:CalledVia": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "RestrictedEC2PermissionsViaClouderaResourceTag",
"Effect": "Allow",
"Action": [
"ec2:RebootInstances",
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:TerminateInstances"
],
"Resource": [
"*"
],
"Condition": {
"ForAnyValue:StringLike": {
"ec2:ResourceTag/Cloudera-Resource-Name": [
"crn:{{ .CRNPartition }}:*"
]
}
}
},
{
"Sid": "RestrictedIamPermissionsToClouderaResources",
"Effect": "Allow",
"Action": [
"iam:PassRole"
],
"Resource": [
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/[YOUR-IDBROKER-ROLE-NAME]",
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/[YOUR-LOG-ROLE-NAME]",
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/liftie-*-eks-service-role",
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/liftie-*-eks-worker-nodes",
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/cdp-eks-master-role",
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/cdp-liftie-instance-profile"
]
},
{
"Sid": "RestrictedKMSPermissionsUsingCustomerProvidedKey",
"Effect": "Allow",
"Action": [
"kms:CreateGrant",
"kms:DescribeKey",
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*"
],
"Resource": [
"[YOUR-KMS-CUSTOMER-MANAGED-KEY-ARN]"
]
},
{
"Sid": "AllowCreateDeleteTagsForSubnets",
"Effect": "Allow",
"Action": [
"ec2:CreateTags",
"ec2:DeleteTags"
],
"Resource": [
"arn:{{ .ARNPartition }}:ec2:[YOUR-SUBNET-REGION]:[YOUR-ACCOUNT-ID]:subnet/*"
]
},
{
"Sid": "ModifyInstanceAttribute",
"Effect": "Allow",
"Action": [
"ec2:ModifyInstanceAttribute"
],
"Resource": [
"*"
],
"Condition": {
"StringEquals": {
"ec2:Attribute": "SourceDestCheck"
}
}
},
{
"Sid": "OtherPermissions",
"Effect": "Allow",
"Action": [
"autoscaling:DescribeAutoScalingGroups",
"ec2:AuthorizeSecurityGroupIngress",
"ec2:CreateLaunchTemplateVersion",
"ec2:CreatePlacementGroup",
"ec2:DeleteKeyPair",
"ec2:DeleteNetworkInterface",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeInstanceTypes",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeSubnets",
"ec2:DescribeVpcAttribute",
"ec2:DescribeVpcs",
"ec2:ImportKeyPair",
"ec2:UpdateSecurityGroupRuleDescriptionsIngress",
"ec2:GetInstanceTypesFromInstanceRequirements",
"eks:DescribeCluster",
"eks:CreateAccessEntry",
"eks:DeleteAccessEntry",
"eks:ListAccessEntries",
"eks:DescribeAccessEntry",
"eks:AssociateAccessPolicy",
"eks:DisassociateAccessPolicy",
"eks:ListAssociatedAccessPolicies",
"elasticloadbalancing:DescribeLoadBalancers",
"iam:GetRole",
"iam:ListRoles",
"iam:GetInstanceProfile"
],
"Resource": [
"*"
]
},
{
"Sid": "AllowSsmParams",
"Effect": "Allow",
"Action": [
"ssm:DescribeParameters",
"ssm:GetParameter",
"ssm:GetParameters",
"ssm:GetParameterHistory",
"ssm:GetParametersByPath"
],
"Resource": [
"arn:aws:ssm:*:*:parameter/aws/service/eks/optimized-ami/*"
]
},
{
"Sid": "CfDeny",
"Effect": "Deny",
"Action": [
"cloudformation:*"
],
"Resource": [
"*"
],
"Condition": {
"ForAnyValue:StringLike": {
"cloudformation:ImportResourceTypes": [
"*"
]
}
}
},
{
"Sid": "ForAutoscalingLinkedRole",
"Effect": "Allow",
"Action": [
"iam:CreateServiceLinkedRole"
],
"Resource": [
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/aws-service-role/autoscaling-plans.amazonaws.com/AWSServiceRoleForAutoScalingPlans_EC2AutoScaling"
],
"Condition": {
"StringLike": {
"iam:AWSServiceName": "autoscaling-plans.amazonaws.com"
}
}
},
{
"Sid": "ForEksLinkedRole",
"Effect": "Allow",
"Action": [
"iam:CreateServiceLinkedRole"
],
"Resource": [
"arn:{{ .ARNPartition }}:iam::[YOUR-ACCOUNT-ID]:role/aws-service-role/eks.amazonaws.com/AWSServiceRoleForEKS"
],
"Condition": {
"StringLike": {
"iam:AWSServiceName": "eks.amazonaws.com"
}
}
}
]
}Supporting Customer Managed CMKs
Along with providing the KMS Customer Managed Customer Master Key (CMK) for volume encryption
in the policy section with Sid:
RestrictedKMSPermissionsUsingCustomerProvidedKey, you need to verify that the
policy for the Customer Managed Customer Master Key (CMK) at KMS (this is not an IAM policy)
has the following permission blocks defined for
AWSServiceRoleForAutoScaling:
{
"Sid": "AllowAutoscalingAndCDPCrossAccountRoleUseOfTheCMK",
"Effect": "Allow",
"Principal":
{
"AWS":
[
"arn:aws:iam::[YOUR-ACCOUNT-ID]:role/CDP-CROSSACCOUNT-ROLE",
"arn:aws:iam::[YOUR-ACCOUNT-ID]:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling"
]
},
"Action":
[
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
},
{
"Sid": "AllowAutoscalingAndCDPCrossAccountRoleToCreateGrantsOfTheCMK",
"Effect": "Allow",
"Principal":
{
"AWS":
[
"arn:aws:iam::[YOUR-ACCOUNT-ID]:role/CDP-CROSSACCOUNT-ROLE",
"arn:aws:iam::[YOUR-ACCOUNT-ID]:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling"
]
},
"Action":
[
"kms:CreateGrant"
],
"Resource": "*",
"Condition":
{
"Bool":
{
"kms:GrantIsForAWSResource": "true"
}
}
},
{
"Sid": "AllowCreateGrantToLiftieCluster",
"Effect": "Allow",
"Principal":
{
"AWS": "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/CDP-CROSSACCOUNT-ROLE"
},
"Action": "kms:CreateGrant",
"Resource": "*",
"Condition":
{
"StringEquals":
{
"aws:CalledViaFirst": "cloudformation.amazonaws.com"
},
"ForAllValues:StringEquals":
{
"kms:GrantOperations":
[
"Encrypt",
"Decrypt"
]
}
}
},
{
"Sid": "AllowEKSAccessToEBS",
"Effect": "Allow",
"Principal":
{
"AWS": "*"
},
"Action":
[
"kms:CreateGrant",
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*",
"Condition":
{
"StringEquals":
{
"kms:CallerAccount": "[YOUR-ACCOUNT-ID]",
"kms:viaService": "ec2.[YOUR-ACCOUNT-REGION].amazonaws.com"
}
}
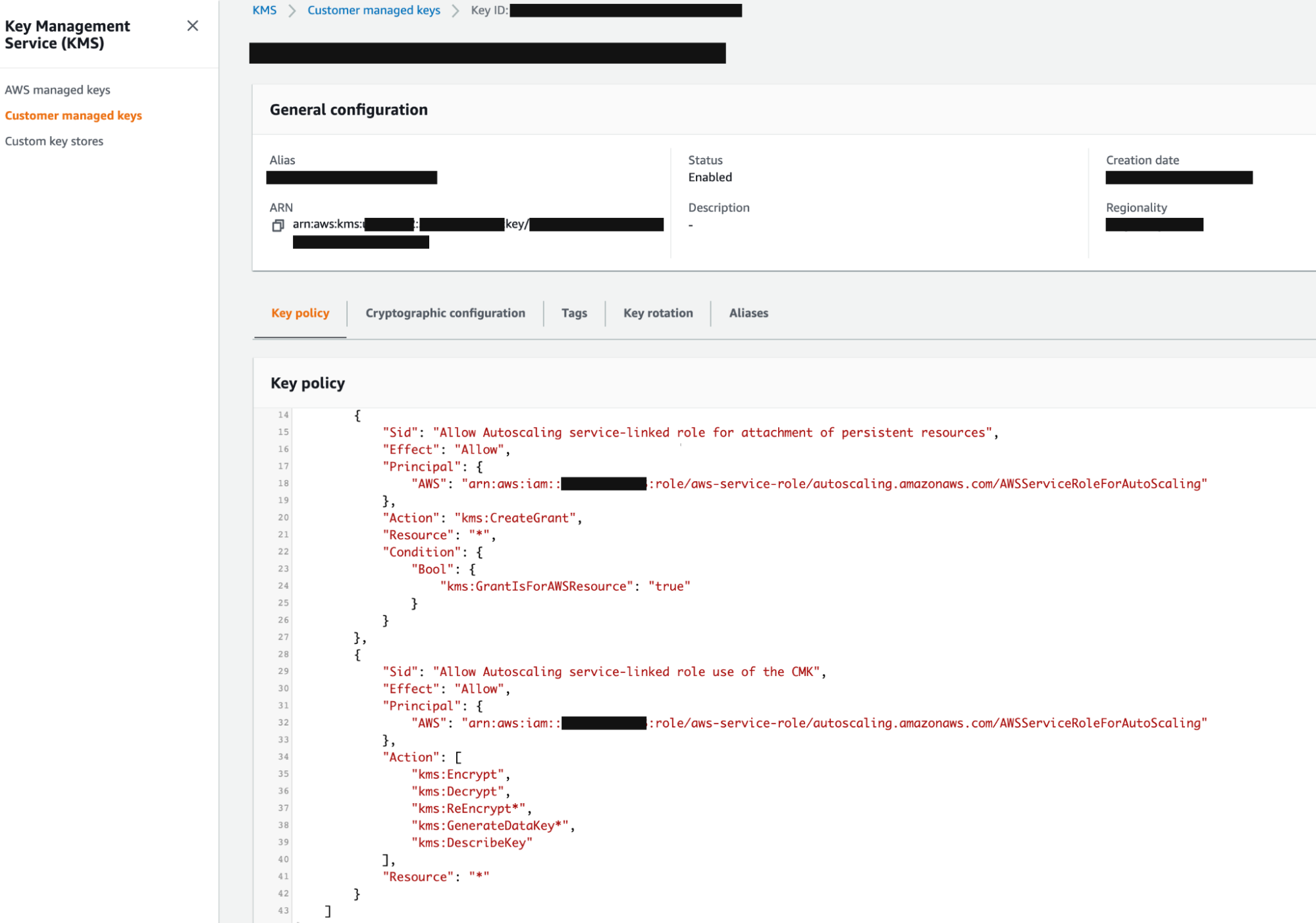
}After the policy is attached, the KMS service page will show the CMK as having the policy attached, similar to this screenshot:
Cloudera Data Engineering restricted IAM policy
{
"Id": "CDEPolicy_v2",
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ElasticFileSystem",
"Action": [
"elasticfilesystem:CreateMountTarget",
"elasticfilesystem:DescribeFileSystems",
"elasticfilesystem:TagResource",
"elasticfilesystem:ClientMount"
],
"Effect": "Allow",
"Resource": [
"*"
]
},
{
"Sid": "ElasticFileSystemRequest",
"Action": [
"elasticfilesystem:CreateFileSystem",
"elasticfilesystem:CreateTags"
],
"Effect": "Allow",
"Resource": [
"*"
],
"Condition": {
"StringLike": {
"aws:RequestTag/Cloudera-Resource-Name": [
"crn:cdp:de:*"
]
}
}
},
{
"Sid": "ElasticFileSystemResource",
"Action": [
"elasticfilesystem:DescribeFileSystemPolicy",
"elasticfilesystem:DeleteFileSystem",
"elasticfilesystem:DescribeMountTargets",
"elasticfilesystem:DeleteMountTarget",
"elasticfilesystem:PutFileSystemPolicy"
],
"Effect": "Allow",
"Resource": [
"*"
],
"Condition": {
"StringLike": {
"aws:ResourceTag/Cloudera-Resource-Name": [
"crn:cdp:de:*"
]
}
}
},
{
"Sid": "CloudWatch",
"Action": [
"cloudwatch:GetMetricData"
],
"Effect": "Allow",
"Resource": [
"*"
]
},
{
"Sid": "ElasticLoadBalancing",
"Action": [
"elasticloadbalancing:DescribeTags"
],
"Effect": "Allow",
"Resource": [
"*"
]
},
{
"Sid": "RelationalDatabaseServiceRequest",
"Action": [
"rds:CreateDBCluster",
"rds:CreateDBSubnetGroup",
"rds:AddTagsToResource",
"rds:CreateDBInstance"
],
"Effect": "Allow",
"Resource": [
"*"
],
"Condition": {
"StringLike": {
"aws:RequestTag/Cloudera-Resource-Name": [
"crn:cdp:de:*"
]
}
}
},
{
"Sid": "RelationalDatabaseServiceResource",
"Action": [
"rds:DeleteDBSubnetGroup",
"rds:DescribeDBInstances",
"rds:ModifyDBInstance",
"rds:DeleteDBInstance"
],
"Effect": "Allow",
"Resource": [
"*"
],
"Condition": {
"StringLike": {
"aws:ResourceTag/Cloudera-Resource-Name": [
"crn:cdp:de:*"
]
}
}
},
{
"Sid": "RelationalDatabaseService",
"Action": [
"rds:DescribeDBEngineVersions"
],
"Effect": "Allow",
"Resource": [
"*"
]
}
]
}
Cloudera Data Hub restricted policy
To add the Cloudera Data Hub restricted policy, copy the following data in the Create Cross-account Access Policy field:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:DeleteTags",
"ec2:AssociateAddress",
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:AttachVolume",
"ec2:DescribeAddresses",
"ec2:TerminateInstances",
"ec2:DeleteSecurityGroup"
],
"Resource": "*",
"Condition": {
"StringLike": {
"ec2:ResourceTag/Cloudera-Resource-Name": [
"crn:cdp:*"
]
}
}
},
{
"Effect": "Allow",
"Action": [
"cloudformation:DeleteStack",
"autoscaling:SuspendProcesses",
"autoscaling:UpdateAutoScalingGroup",
"autoscaling:ResumeProcesses",
"autoscaling:DetachInstances",
"autoscaling:DeleteAutoScalingGroup",
"rds:StopDBInstance",
"rds:StartDBInstance"
],
"Resource": "*",
"Condition": {
"StringLike": {
"aws:ResourceTag/Cloudera-Resource-Name": [
"crn:cdp:*"
]
}
}
},
{
"Effect": "Allow",
"Action": [
"cloudformation:CreateStack",
"cloudformation:GetTemplate",
"ec2:CreateTags"
],
"Resource": [
"*"
],
"Condition": {
"StringLike": {
"aws:RequestTag/Cloudera-Resource-Name": [
"crn:cdp:*"
]
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:DeleteVolume",
"ec2:CreateSecurityGroup",
"ec2:DeleteKeyPair",
"ec2:DescribeKeyPairs",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeImages",
"ec2:DeleteLaunchTemplate",
"ec2:DescribeVolumes",
"ec2:CreateVolume",
"ec2:DescribeInstances",
"ec2:DescribeRegions",
"ec2:DescribeInstanceTypeOfferings",
"ec2:DescribeInstanceTypes",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"ec2:DescribeVpcAttribute",
"ec2:DescribeVpcs",
"ec2:DescribeInternetGateways",
"ec2:DescribeVpcEndpoints",
"ec2:describeAddresses",
"ec2:DescribeNatGateways",
"ec2:DescribeVpcEndpointServices",
"ec2:ModifySubnetAttribute",
"ec2:ModifyVpcAttribute",
"ec2:CreatePlacementGroup",
"ec2:DescribePlacementGroups",
"ec2:ImportKeyPair",
"ec2:DescribeLaunchTemplates",
"ec2:CreateLaunchTemplate",
"ec2:RunInstances",
"ec2:DescribeAccountAttributes",
"sts:DecodeAuthorizationMessage",
"cloudformation:DescribeStacks",
"dynamodb:DeleteTable",
"dynamodb:DescribeTable",
"iam:ListInstanceProfiles",
"iam:ListRoles",
"dynamodb:ListTables",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeScalingActivities",
"autoscaling:CreateAutoScalingGroup",
"autoscaling:TerminateInstanceInAutoScalingGroup",
"cloudwatch:DeleteAlarms",
"cloudwatch:PutMetricAlarm",
"cloudwatch:DescribeAlarms",
"elasticloadbalancing:CreateLoadBalancer",
"elasticloadbalancing:CreateTargetGroup",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:AddTags",
"elasticloadbalancing:RegisterTargets",
"elasticloadbalancing:DescribeTargetHealth",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:CreateListener",
"elasticloadbalancing:DeleteListener",
"elasticloadbalancing:DeleteTargetGroup",
"elasticloadbalancing:DeleteLoadBalancer",
"elasticloadbalancing:DeregisterTargets",
"s3:GetBucketLocation",
"cloudformation:DescribeStackEvents",
"cloudformation:DescribeStackResources",
"cloudformation:DescribeStackResource",
"cloudformation:ListStackResources",
"cloudformation:UpdateStack",
"cloudformation:GetTemplate",
"iam:GetInstanceProfile",
"iam:SimulatePrincipalPolicy",
"iam:GetRole",
"rds:AddTagsToResource",
"rds:CreateDBInstance",
"rds:CreateDBSubnetGroup",
"rds:DeleteDBInstance",
"rds:DeleteDBSubnetGroup",
"rds:ListTagsForResource",
"rds:RemoveTagsFromResource",
"rds:CreateDBParameterGroup",
"rds:DeleteDBParameterGroup",
"rds:DescribeEngineDefaultParameters",
"rds:ModifyDBParameterGroup",
"rds:DescribeDBParameters",
"rds:DescribeDBParameterGroups",
"rds:DescribeDBSubnetGroups",
"rds:DescribeDBInstances",
"rds:ModifyDBInstance",
"rds:DescribeCertificates",
"kms:ListKeys",
"kms:ListAliases",
"ec2:ModifyInstanceAttribute",
"ec2:CreateLaunchTemplateVersion"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"iam:PassRole"
],
"Resource": [
"arn:aws:iam::[YOUR-ACCOUNT-ID]:role/[YOUR-IDBROKER-ROLE-NAME]"
]
},
{
"Sid": "IdentityAccessManagementLimited",
"Action": [
"iam:CreateServiceLinkedRole"
],
"Effect": "Allow",
"Resource": [
"arn:aws:iam::*:role/aws-service-role/*"
]
}
]
}