Using resource-based authorization policies for Trino
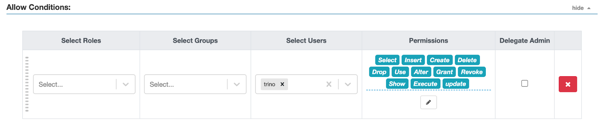
The Apache Ranger access policy model consists of two major components: the specification of the resources a policy is applied to, such as Catalog, Schema, tables, columns, and so on; and the specification of access conditions for specific users and groups.
The following table lists the allowed permissions and the actions that they support
in Trino:
| Permission | Action |
|---|---|
| Select | Provides read access to an object (table, view, and materialized view) |
| Insert | Provides the ability to insert records into a table |
| Update | Provides the permission to modify column values in existing rows of a table |
| Delete | Provides the ability to remove records from a table |
| Create | Provides the permission to create an object (schema, table, view, and materialized view) |
| Alter | Provides the ability to:
|
| Drop | Provides the permission to drop an object (schema, table, view, and materialized view) |
| Use | Update the session to use the specified catalog and schema |
| Grant | Assign privileges to users on an object |
| Revoke | Deny privileges to users on an object |
| Show | Provides the ability to:
|
| Excute | Provides the permission to run a SQL statement |
Perform the following steps to set up the required authorization policies for Trino:

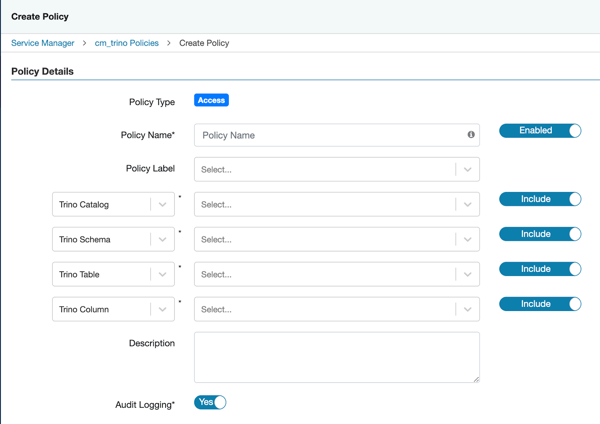
 to
choose the necessary permissions.
to
choose the necessary permissions.