Using reduced permissions mode, you must manually update the AWS CloudFormation
template and update the stack before upgrading to EKS 1.23.
The CloudFormation stack consists of AWS resources, such
as the S3 object store, and IAM access controls that you manage using a template. The
template defines the configuration of AWS resources.
You use AWS Management Console to edit the cluster cloud formation template to add
the ebs policy to the NodeInstanceRole policies.
-
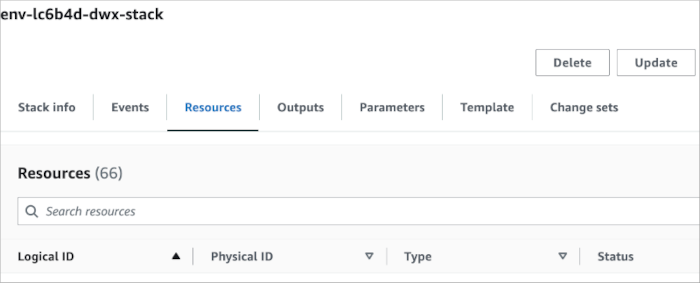
Navigate to .
-
Locate the stack corresponding to the cluster ID.
This stack name is the one in this format: <cluster-ID>-dwx-stack. For example,
if the cluster ID is env-ic6b4d-dwx, the CloudFormation stack name for this cluster is
env-ic6b4d-dwx-stack.
-
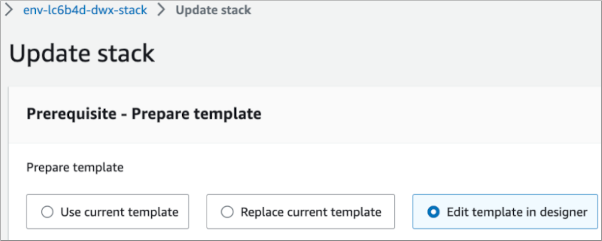
In Resources, click Update.
-
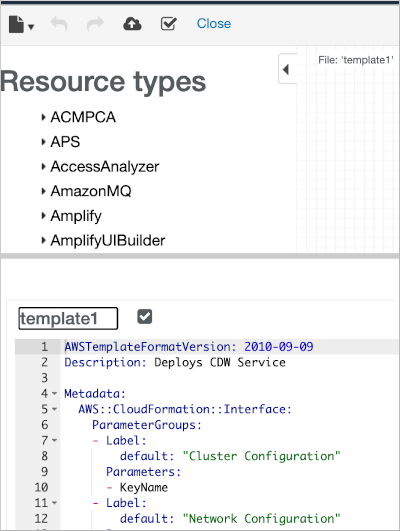
Click Edit template in designer.
-
Click View in designer.
-
Edit the CloudFormation template to add the following
ebs policy.
- PolicyName: 'ebs'
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Action:
- ec2:CreateSnapshot
- ec2:AttachVolume
- ec2:DetachVolume
- ec2:ModifyVolume
- ec2:DescribeAvailabilityZones
- ec2:DescribeInstances
- ec2:DescribeSnapshots
- ec2:DescribeTags
- ec2:DescribeVolumes
- ec2:DescribeVolumesModifications
Resource: "*"
- Effect: Allow
Action:
- ec2:CreateTags
Resource:
- arn:aws:ec2:*:*:volume/*
- arn:aws:ec2:*:*:snapshot/*
Condition:
StringEquals:
ec2:CreateAction:
- CreateVolume
- CreateSnapshot
- Effect: Allow
Action:
- ec2:DeleteTags
Resource:
- arn:aws:ec2:*:*:volume/*
- arn:aws:ec2:*:*:snapshot/*
- Effect: Allow
Action:
- ec2:CreateVolume
Resource: "*"
Condition:
StringLike:
aws:RequestTag/ebs.csi.aws.com/cluster: 'true'
- Effect: Allow
Action:
- ec2:CreateVolume
Resource: "*"
Condition:
StringLike:
aws:RequestTag/CSIVolumeName: "*"
- Effect: Allow
Action:
- ec2:CreateVolume
Resource: "*"
Condition:
StringLike:
aws:RequestTag/kubernetes.io/cluster/*: owned
- Effect: Allow
Action:
- ec2:DeleteVolume
Resource: "*"
Condition:
StringLike:
ec2:ResourceTag/ebs.csi.aws.com/cluster: 'true'
- Effect: Allow
Action:
- ec2:DeleteVolume
Resource: "*"
Condition:
StringLike:
ec2:ResourceTag/CSIVolumeName: "*"
- Effect: Allow
Action:
- ec2:DeleteVolume
Resource: "*"
Condition:
StringLike:
ec2:ResourceTag/kubernetes.io/cluster/*: owned
- Effect: Allow
Action:
- ec2:DeleteSnapshot
Resource: "*"
Condition:
StringLike:
ec2:ResourceTag/CSIVolumeSnapshotName: "*"
- Effect: Allow
Action:
- ec2:DeleteSnapshot
Resource: "*"
Condition:
StringLike:
ec2:ResourceTag/ebs.csi.aws.com/cluster: 'true'
- Effect: Allow
Action:
- kms:Decrypt
- kms:GenerateDataKeyWithoutPlaintext
- kms:CreateGrant
Resource: "*"