Adding Docker registry credentials
To enable Cloudera AI to fetch custom ML Runtimes from a secure repository, as an Administrator you need to add Docker registry credentials. If you want to use different credentials for different runtimes, you can add more docker credentials using the UI and API v2 and use that credentials to fetch custom ML Runtimes.
- In the Cloudera console, click the
Cloudera AI tile.
The Cloudera AI Workbenches page displays.
- Click on the name of the workbench.
The Workbenches Home page displays.
- Click Site Administration in the left navigation menu.
The Site Administration page displays.
- Click Runtimes, and click Add Credentials in
the Docker Credentials section. The Add Credentials dialog box is displayed.
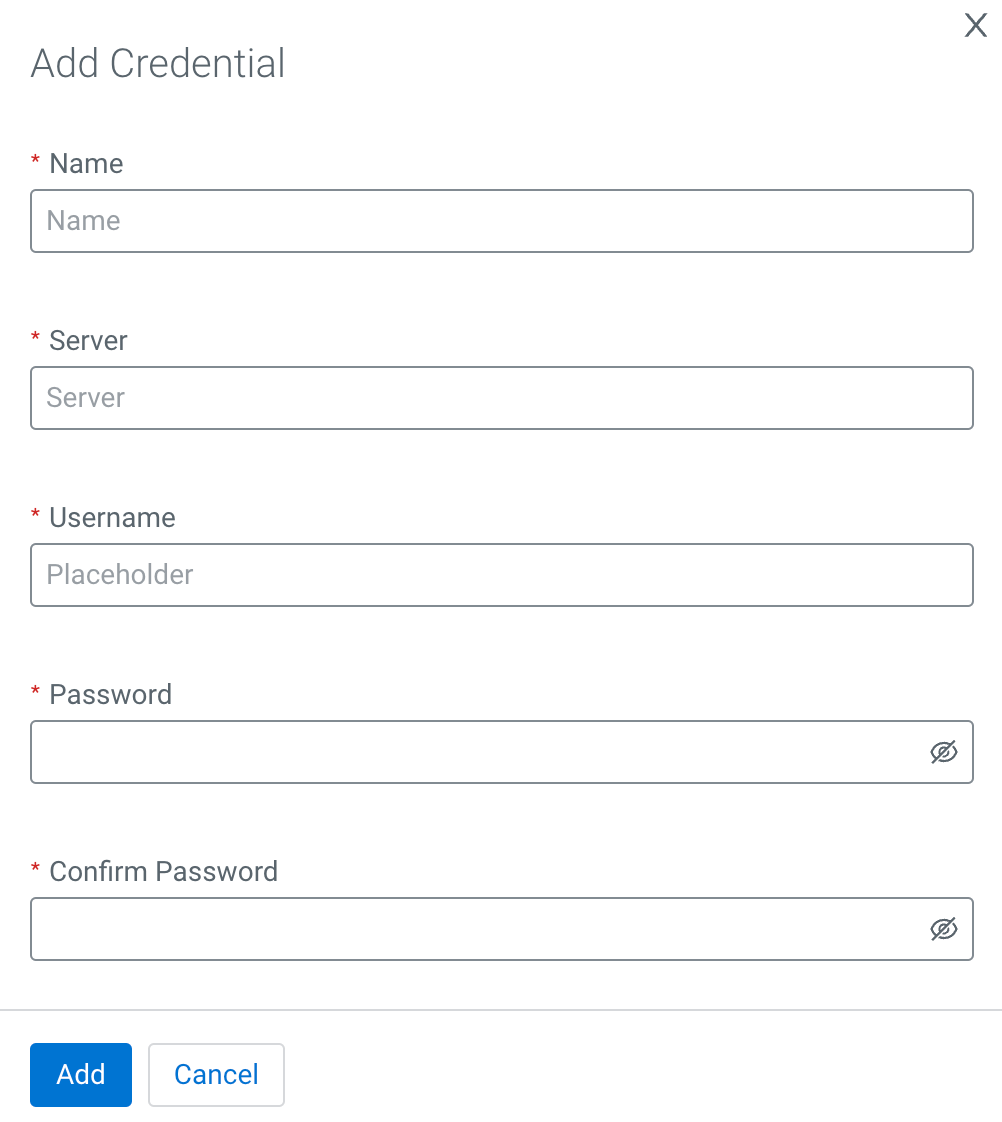
- In Name, provide a name for the credential. This name will be displayed to manage the credentials.
- In Server, provide the docker server address.
- In Username, provide the username of the credential.
- In Password, provide the password for the credential.
- In Confirm Password, repeat the same password given in the Password field.
- Click Add.
The credentials name and server name are displayed under the Docker Credentials section. The default credentials are used when ML Runtimes images are pulled, and non-default credentials are used when they are added to a Custom Runtime image in Runtime Catalog.
Click Add Credentials to add more docker credentials. You can use the
![]() toggle
button to set the default credential. The default credential is picked up automatically for
Custom Runtimes coming from the server stored in the default credential. To use your other
credentials, add them to Custom Runtimes in Runtime Catalog.
toggle
button to set the default credential. The default credential is picked up automatically for
Custom Runtimes coming from the server stored in the default credential. To use your other
credentials, add them to Custom Runtimes in Runtime Catalog.
For Legacy engines, the default credentials are used when Legacy Engine images are pulled. The default credential is picked up automatically for Custom Legacy Engines coming from the server stored in the default credential.
Click ![]() to edit the
Docker credential and click
to edit the
Docker credential and click ![]() to delete the Docker credential.
to delete the Docker credential.
Adding Docker Registry certificates to Cloudera AI
- Pull the existing certificates:
kubectl get configmap private-cloud-ca-certs-pem -n [***CML workspace namespace***] -o jsonpath="{4e.binaryData.cacerts}" | base64 -d > /tmp/oldcerts.pem - Append your docker registry certificates to the existing certificates and convert them to
base64:
cat /tmp/dockercerts.crt /tmp/oldcerts.pem > /tmp/newcerts.pem cat /tmp/newcerts.pem | base64 -w 0 > /tmp/newcerts.b64 - Pull the certificates' configuration map and update it with this new certificate
file:
kubectl get configmap private-cloud-ca-certs-pem -n [***CML workspace namespace***] -o yaml > /tmp/oldconfigmap.yaml cat /tmp/oldconfigmap.yaml | sed "s/cacerts.*/cacerts: $(cat /tmp/newcerts.b64)/" > /tmp/newconfigmap.yaml kubectl apply -f /tmp/newconfigmap.yaml - Delete the runtime-manager pod to restart it and see these new
certificates:
kubectl delete pod runtime-manager-xxxxxxx-xxxxx -n [***CML workspace namespace***]
Adding Docker registry certificates to Cloudera
If the Custom Runtime repository uses self-signed TLS certificates, those certificates must be trusted by Clouderaprior to creating the Cloudera AI Workbench. The certificates must be uploaded to Miscellaneous category, as uploading them to other categories might intervene into other processes. See the necessary steps to make Cloudera trust the self-signed certificates in Updating TLS certificates.
