Rotating Data Lake secrets
To strengthen the security of your deployments, you can rotate sensitive secrets, such as database passwords or admin credentials for the Data Lake cluster. These secrets are managed and created by either Cloudera or users.
Secret rotation can be performed using the Cloudera Management Console or CLI commands. By rotating secrets, you reduce the risk of unauthorized access and enhance the overall security of your environment. A single secret rotation typically takes no longer than five minutes, minimizing downtime and disruption.
| Secret name | Secret description | Downtime |
|---|---|---|
| Cloudera Admin password ( |
Used by the Cloudera Control Plane to manage Cloudera Manager, issue commands and poll info. | No |
| External Database Root Password ( |
Initializing and managing External Databases created by the Cloudera Control Plane. Creates initial users and databases through this credential. | No |
| Cloudera Manager Database Password ( |
Credentials Cloudera Manager uses to connect to External Database. | Minimal as the Cloudera Manager service might not be available temporarily |
| Cloudera Manager Shared Services Database Password ( |
Used by shared services (such as Hive Metastore) managed by Cloudera Manager to connect to the External Database. When initiated on the Data Lake cluster, this rotation will update all affected (using Hive Metastore) and corresponding Cloudera Data Hub cluster. | Minimal as the Cloudera Manager server and agent are restarted during secret update. Operations, such as scaling and repair, are blocked. |
| Cloudbreak user root SSH public key ( |
Public SSH key specified during the environment creation. Before rotating the SSH public key, you need to change keys on the Environment summary page, then rotate the secret for the Data Lake. |
No |
| Cloudera Manager Services Database Password ( |
Used by LOCAL services managed by Cloudera Manager to connect to the External Database.This could include multiple services, such as Hue, Atlas, Ranger and so on. | Minimal |
| LDAP Bind Password ( |
Password used to connect and fetch user and group context from LDAP located on the FreeIPA nodes. | No |
| SSSD password ( |
Used to manage the SSSD service, which provides unified management of authentication methods on the cluster such as ssh, keytab generation and so on. | No |
| Databus access key ( |
Machine user service credential, used for communicating with Cloudera Control Plane through the DBUS interface by services such as the metering agent, diagnostic bundle collection and telemetry publisher. | Minimal due to TelemetryAgent restart. |
| Salt boot secrets ( |
Used for bootstrapping new Virtual Machine to the cluster during cluster creation, upscale operation, OS upgrade and repair. | No |
| Salt sign key pair ( |
Used to sign and verify files or data distributed to Salt minions. Ensures integrity and authenticity of data managed by the Salt system. | No |
| Salt master key pair ( |
Used to establish secure communication between the Salt master and minions. The public key is shared with the minions to verify the identity of the master. | No |
| Salt password ( |
Salt user's password used to communicate with the Salt cluster. | No |
| Nginx server side private key ( |
Private key of server side NGINX SSL certificate used for communication with internal services like salt-bootstrap | Minimal, NGINX restart can cause small downtime, which is covered by retries |
| Compute monitoring credentials ( |
Credentials used for compute monitoring components (prometheus, request-signer, etc.). | Minimal |
| Embedded DB SSL certificate ( |
Private key of embedded postgres database SSL certificate. | Minimal |
| IDBroker Certificate ( |
Used by IDBroker service to sign token for accessing Cloud storage. | Minimal, due to IDBroker restart. |
| Cloudera Manager Intermediate Certificate Authority ( |
Used by Cloudera Manager and Cloudera Manager agents to serve HTTPS apis on the cluster nodes. Root CA is located and signed by FreeIPA. | Minimal due to Cloudera Manager server and agent restart during secret update. Scaling and repair is blocked. |
cdp datalake list-datalake-secret-types --datalake {crn}You can use the following steps in Cloudera Management Console or CLI commands to rotate the Data Lake secrets:
-
- Navigate to your environment in Cloudera Management Console.
- Click Data Lake on the environment details page.
- Click Security.Under Secret Management, the list of secrets that can be rotated will be displayed:
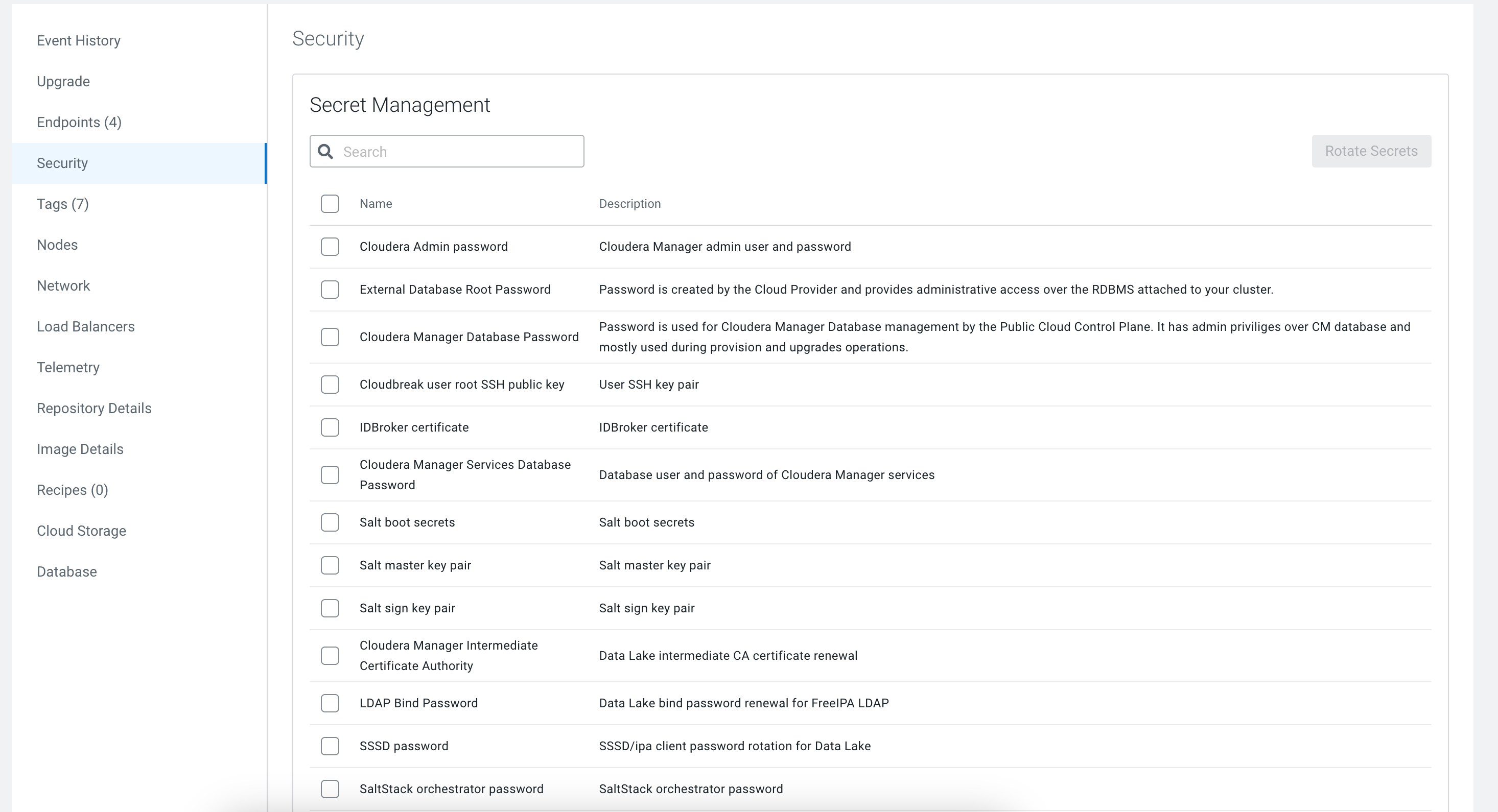
- Select the secrets that you want to rotate.
- Click Rotate Secrets.
- Use the following command to rotate the specific secret
types:
cdp datalake rotate-secrets --datalake {datalakeCrn} --secret-types {SECRETENUM1,SECRETENUM2}
