Creating Compute Restricted IAM policy
Complete the steps to attach the Compute Restricted IAM policy with the cross-account role associated with your environment.
-
Go to the Environments page.
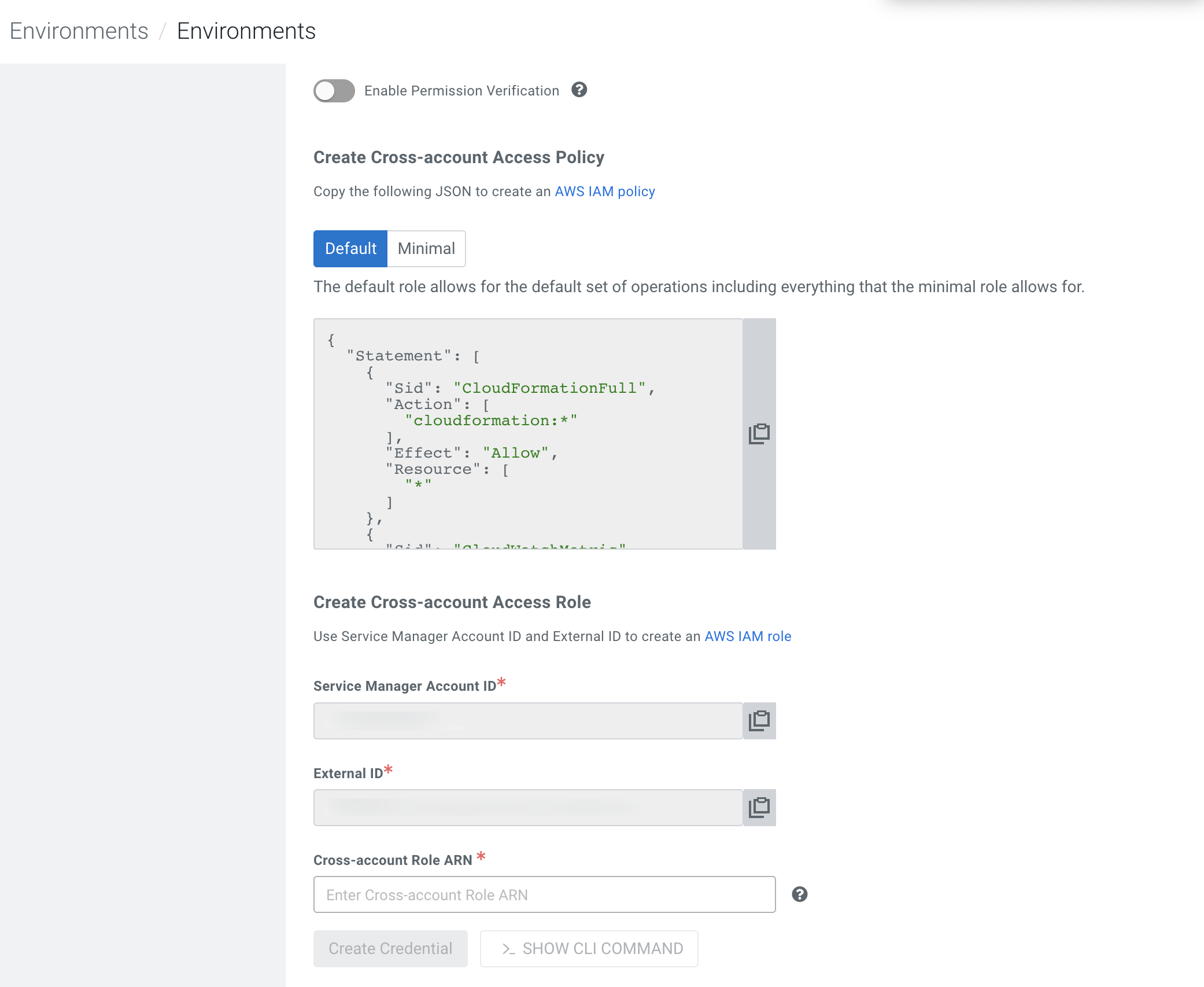
-
In the Create Cross-account Access Policy field, attach the
Compute Restricted IAM policy:
Replace the following placeholders in the JSON file:
- [YOUR-ACCOUNT-ID] with your account ID in use.
- [YOUR-IAM-ROLE-NAME] with the IAM restricted role associated with this policy.
- [YOUR-SUBNET-ARN-*] supplied during the Cloudera Environment(s) creation.
- [YOUR-IDBROKER-ROLE-NAME] with the ID Broker Role name in use.
- [YOUR-LOG-ROLE-NAME] with the Log Role name in use.
- [YOUR-KMS-CUSTOMER-MANAGED-KEY-ARN] with KMS key ARN.
{ "Version": "2012-10-17", "Id": "ComputePolicy_v12", "Statement": [ { "Sid": "SimulatePrincipalPolicy", "Effect": "Allow", "Action": [ "iam:SimulatePrincipalPolicy" ], "Resource": [ "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/[YOUR-IAM-ROLE-NAME]" ] }, { "Sid": "RestrictedPermissionsViaClouderaRequestTag", "Effect": "Allow", "Action": [ "cloudformation:CreateStack", "cloudformation:CreateChangeSet", "ec2:createTags", "eks:TagResource" ], "Resource": "*", "Condition": { "StringLike": { "aws:RequestTag/Cloudera-Resource-Name": [ "crn:cdp:*" ] } } }, { "Sid": "RestrictedPermissionsViaClouderaResourceTag", "Effect": "Allow", "Action": [ "autoscaling:DeleteTags", "autoscaling:DetachInstances", "autoscaling:ResumeProcesses", "autoscaling:SetDesiredCapacity", "autoscaling:SuspendProcesses", "autoscaling:TerminateInstanceInAutoScalingGroup", "autoscaling:UpdateAutoScalingGroup", "cloudformation:DeleteChangeSet", "cloudformation:DeleteStack", "cloudformation:DescribeChangeSet", "cloudformation:DescribeStacks", "cloudformation:CancelUpdateStack", "cloudformation:ContinueUpdateRollback", "cloudformation:DescribeStackEvents", "cloudformation:DescribeStackResource", "cloudformation:DescribeStackResources", "cloudformation:ExecuteChangeSet", "cloudformation:ListStacks", "cloudwatch:deleteAlarms", "cloudwatch:putMetricAlarm", "ec2:AttachVolume", "ec2:CreateNetworkInterface", "ec2:CreateVolume", "ec2:DeleteVolume", "ec2:RunInstances", "eks:DescribeUpdate", "eks:ListUpdates", "eks:UpdateClusterConfig", "eks:UpdateClusterVersion", "iam:GetRolePolicy", "iam:ListInstanceProfiles", "iam:ListRoleTags", "iam:RemoveRoleFromInstanceProfile", "iam:TagRole", "iam:UntagRole", "logs:DescribeLogStreams", "logs:FilterLogEvents" ], "Resource": "*", "Condition": { "StringLike": { "aws:ResourceTag/Cloudera-Resource-Name": [ "crn:cdp:*" ] } } }, { "Sid": "RestrictedPermissionsViaCloudFormation", "Effect": "Allow", "Action": [ "autoscaling:CreateAutoScalingGroup", "autoscaling:CreateLaunchConfiguration", "autoscaling:CreateOrUpdateTags", "autoscaling:DeleteAutoScalingGroup", "autoscaling:DeleteLaunchConfiguration", "autoscaling:DescribeAutoScalingInstances", "autoscaling:DescribeLaunchConfigurations", "autoscaling:DescribeScalingActivities", "autoscaling:DescribeScheduledActions", "autoscaling:DescribeTags", "dynamodb:DescribeTable", "ec2:AuthorizeSecurityGroupEgress", "ec2:CreateLaunchTemplate", "ec2:CreateSecurityGroup", "ec2:DeleteLaunchTemplate", "ec2:DeletePlacementGroup", "ec2:DeleteSecurityGroup", "ec2:DescribeAccountAttributes", "ec2:DescribeImages", "ec2:DescribeInstanceStatus", "ec2:DescribeInstances", "ec2:DescribeKeyPairs", "ec2:DescribeLaunchTemplateVersions", "ec2:DescribeLaunchTemplates", "ec2:DescribePlacementGroups", "ec2:DescribeRegions", "ec2:DescribeRouteTables", "ec2:DescribeSecurityGroups", "ec2:DescribeVolumes", "ec2:RevokeSecurityGroupEgress", "ec2:RevokeSecurityGroupIngress", "eks:CreateCluster", "eks:DeleteCluster" ], "Resource": "*", "Condition": { "ForAnyValue:StringEquals": { "aws:CalledVia": [ "cloudformation.amazonaws.com" ] } } }, { "Sid": "RestrictedEC2PermissionsViaClouderaResourceTag", "Effect": "Allow", "Action": [ "ec2:RebootInstances", "ec2:StartInstances", "ec2:StopInstances", "ec2:TerminateInstances" ], "Resource": [ "*" ], "Condition": { "ForAnyValue:StringLike": { "ec2:ResourceTag/Cloudera-Resource-Name": [ "crn:cdp:*" ] } } }, { "Sid": "RestrictedIamPermissionsToClouderaResources", "Effect": "Allow", "Action": [ "iam:PassRole" ], "Resource": [ "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/[YOUR-IDBROKER-ROLE-NAME]", "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/[YOUR-LOG-ROLE-NAME]", "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/liftie-*-eks-service-role", "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/liftie-*-eks-worker-nodes", "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/cdp-eks-master-role", "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/cdp-liftie-instance-profile" ] }, { "Sid": "RestrictedKMSPermissionsUsingCustomerProvidedKey", "Effect": "Allow", "Action": [ "kms:CreateGrant", "kms:DescribeKey", "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*" ], "Resource": [ "[YOUR-KMS-CUSTOMER-MANAGED-KEY-ARN]" ] }, { "Sid": "AllowCreateDeleteTagsForSubnets", "Effect": "Allow", "Action": [ "ec2:CreateTags", "ec2:DeleteTags" ], "Resource": [ "arn:aws:ec2:[YOUR-SUBNET-REGION]:[YOUR-ACCOUNT-ID]:subnet/*" ] }, { "Sid": "ModifyInstanceAttribute", "Effect": "Allow", "Action": [ "ec2:ModifyInstanceAttribute" ], "Resource": [ "*" ], "Condition": { "StringEquals": { "ec2:Attribute": "SourceDestCheck" } } }, { "Sid": "OtherPermissions", "Effect": "Allow", "Action": [ "autoscaling:DescribeAutoScalingGroups", "ec2:AuthorizeSecurityGroupIngress", "ec2:CreateLaunchTemplateVersion", "ec2:CreatePlacementGroup", "ec2:DeleteKeyPair", "ec2:DeleteNetworkInterface", "ec2:DescribeAvailabilityZones", "ec2:DescribeInstanceTypes", "ec2:DescribeNetworkInterfaces", "ec2:DescribeSubnets", "ec2:DescribeVpcAttribute", "ec2:DescribeVpcs", "ec2:ImportKeyPair", "ec2:UpdateSecurityGroupRuleDescriptionsIngress", "ec2:GetInstanceTypesFromInstanceRequirements", "eks:DescribeCluster", "elasticloadbalancing:DescribeLoadBalancers", "iam:GetRole", "iam:ListRoles", "iam:GetInstanceProfile" ], "Resource": [ "*" ] }, { "Sid": "AllowSsmParams", "Effect": "Allow", "Action": [ "ssm:DescribeParameters", "ssm:GetParameter", "ssm:GetParameters", "ssm:GetParameterHistory", "ssm:GetParametersByPath" ], "Resource": [ "arn:aws:ssm:*:*:parameter/aws/service/eks/optimized-ami/*" ] }, { "Sid": "CfDeny", "Effect": "Deny", "Action": [ "cloudformation:*" ], "Resource": [ "*" ], "Condition": { "ForAnyValue:StringLike": { "cloudformation:ImportResourceTypes": [ "*" ] } } }, { "Sid": "ForAutoscalingLinkedRole", "Effect": "Allow", "Action": [ "iam:CreateServiceLinkedRole" ], "Resource": [ "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/aws-service-role/autoscaling-plans.amazonaws.com/AWSServiceRoleForAutoScalingPlans_EC2AutoScaling" ], "Condition": { "StringLike": { "iam:AWSServiceName": "autoscaling-plans.amazonaws.com" } } }, { "Sid": "ForEksLinkedRole", "Effect": "Allow", "Action": [ "iam:CreateServiceLinkedRole" ], "Resource": [ "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/aws-service-role/eks.amazonaws.com/AWSServiceRoleForEKS" ], "Condition": { "StringLike": { "iam:AWSServiceName": "eks.amazonaws.com" } } } ] } -
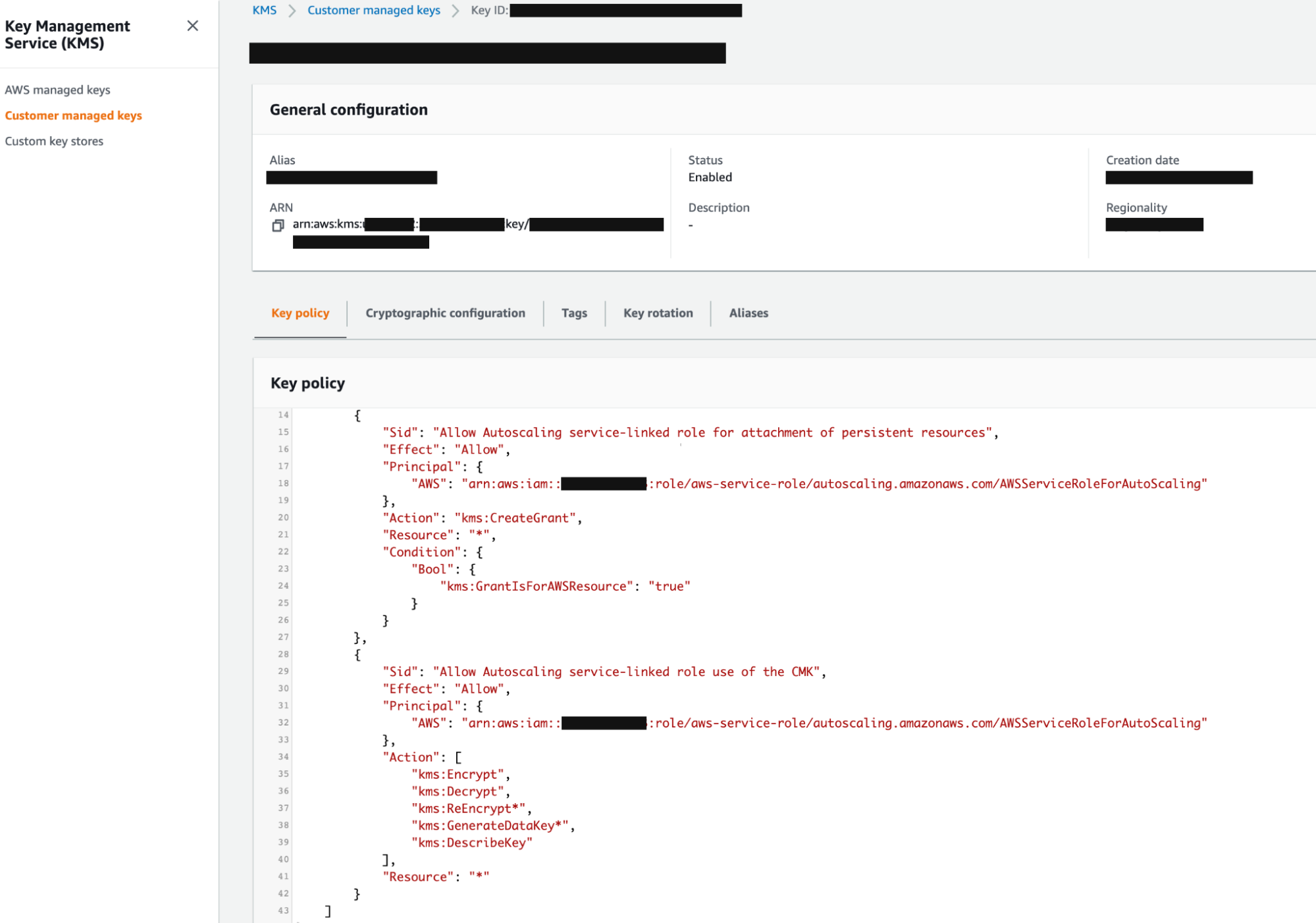
Provide and verify your Customer Managed Key (CMK) to be used for EBS encryption.
Along with providing the KMS Customer Managed Key (CMK) for volume encryption in the policy section with
Sid: RestrictedKMSPermissionsUsingCustomerProvidedKey, you need to verify that the policy for the Customer Managed Key (CMK) at KMS (this is not an IAM policy) has the following three permission blocks defined forAWSServiceRoleForAutoScaling.{ "Statement": [ { "Sid": "AllowAutoscalingServiceLinkedRoleForAttachmentOfPersistentResources", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling" }, "Action": "kms:CreateGrant", "Resource": "*", "Condition": { "Bool": { "kms:GrantIsForAWSResource": "true" } } }, { "Sid": "AllowAutoscalingServiceLinkedRoleUseOfTheCMK", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::[YOUR-ACCOUNT-ID]:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling" }, "Action": [ "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "*" }, { "Sid": "Allow EKS access to EBS.", "Effect": "Allow", "Principal": { "AWS": "*" }, "Action": [ "kms:CreateGrant", "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "*", "Condition": { "StringEquals": { "kms:CallerAccount": "[YOUR-ACCOUNT-ID]", "kms:viaService": "ec2.[YOUR-ACCOUNT-REGION].amazonaws.com" } } } ] }After the policy is attached, the KMS service page will show the CMS as having the policy attached as shown in the following example: