Client connectivity information for compiling your application for Cloudera Operational Database
When compiling your application for your Cloudera Operational Database you need information about the connectivity options that helps your applications interact with Cloudera Operational Database. You can get that information either using the CLI or the Cloudera Operational Database user interface.
The following is a graphical representation of the necessary steps to compile an application against Cloudera Operational Database.

- HBase: Apache HBase Maven URL, Apache HBase client version, and the Apache HBase client configuration URL used to download a file containing the Apache HBase client configuration
- HBase REST: Apache HBase REST Server version and Apache HBase REST Server URL
- HBase Client Tarball: Apache HBase version, download URL of the client tarball, and the Apache HBase client configuration URL used to download a file containing the Apache HBase client configuration
- Phoenix (Thick): Phoenix thick JDBC driver URL and version number of the client artifacts
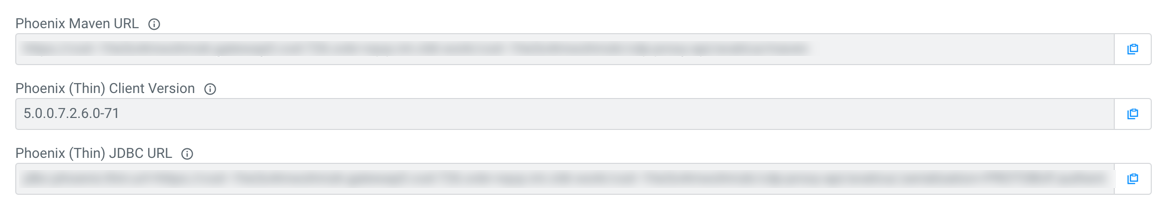
- Phoenix (Thin): Phoenix thin JDBC driver URL and version number of the client artifacts
- Phoenix (ODBC): Phoenix ODBC driver URL. You need to authenticate again to access this driver
You can also download the YARN and Kerberos configuration from these tabs where applicable.
Maven repository containing the HBase client artifacts
Maven repository containing HBase client artifacts is provided in the HBase tab. You can get the following information from this tab:
- HBase Maven URL: Use this URL to access the Maven repository containing HBase client artifacts
- HBase Client Version: You can view the version of HBase client artifacts in the Maven repository
- HBase Client Configuration URL: You can get the endpoint which provides a ZIP file with HBase client configuration files
curl in the CLI to download the tarball. For example,
curl -O -u <username> "<download url>.tar.gz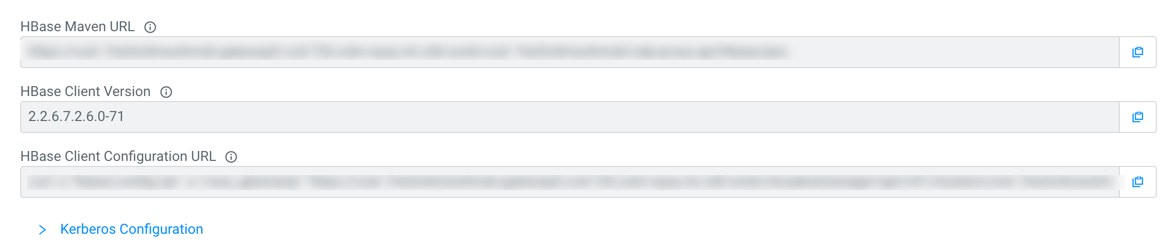
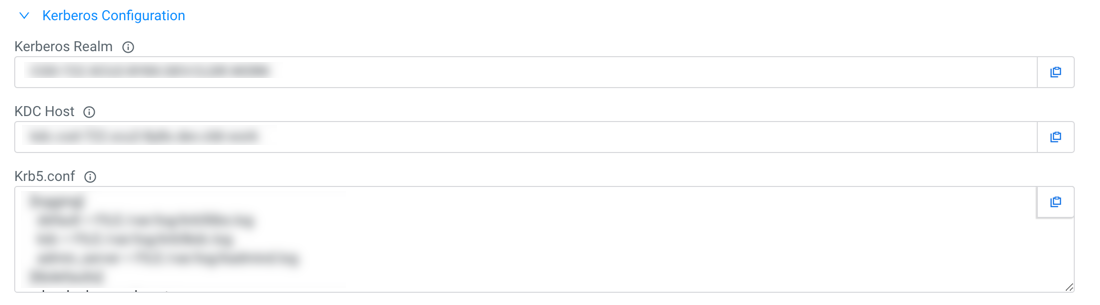
- Kerberos Realm: You need the Kerberos realm information for connecting your clients requiring Kerberos authentication
- KDC Host: You need the Kerberos Key Distribution Center (KDC) hostname for your clients requiring Kerberos authentication
- Krb5.conf: You can download a sample krb5.conf file for your clients requiring Kerberos authentication
The /etc/krb5.conf file is the configuration a client uses to access a
realm through its configured KDC. The krb5.conf maps the realm to the available servers
supporting those realms. It also defines the host-specific configuration rules for how
tickets are requested and granted. The krb5.conf file is used to determine the default
Kerberos realm and KDC. Add the contents into the /etc/krb5.conf file on your edge node. For
more infromation, see Configure Kerberos.
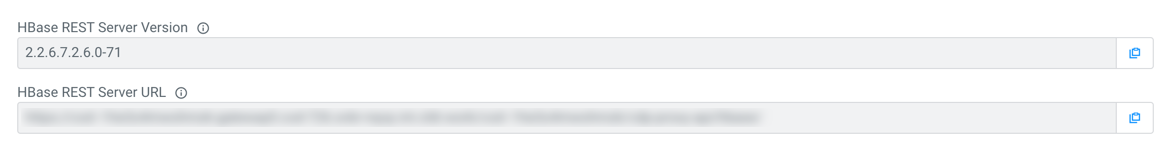
HBase REST
- HBase REST Server Version: You can see the version of HBase REST server
- HBase REST Server URL: You can get the URL to the HBase REST Server to connect to your Cloudera Operational Database
HBase Client Tarball
You can download the HBase client tarball that contains the JAR files used to connect to your database. The HBase client tarball contains the necessary scripts and JAR files that you need to connect your database when using interactive tools such as HBase Shell or SQLLine.
Click tab, and then use the Download URL to download the tarball.
curl in the CLI to download the tarball. For example,
curl -O -u <username> "<download url>.tar.gz"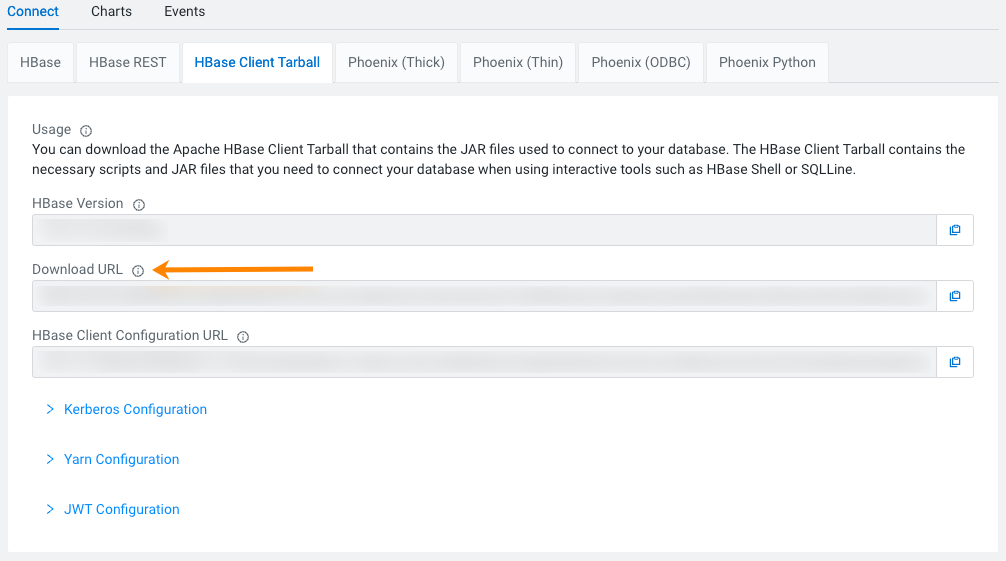
- Kerberos Realm: You need the Kerberos realm information for connecting your clients requiring Kerberos authentication
- KDC Host: You need the Kerberos Key Distribution Center (KDC) hostname for your clients requiring Kerberos authentication
- Krb5.conf: You can download a sample krb5.conf file for your clients requiring Kerberos authentication
YARN configuration information is provided in the HBase Client Tarball tab. You need this additional configuration information to submit YARN applications that access data stored in Cloudera Operational Database.
ssl-client.xml in the downloaded and unzipped YARN
Archive if it is not present in the archive folder. You need this file to run YARN workloads
against Cloudera Operational Database. <?xml version="1.0" encoding="UTF-8"?>
<configuration>
<property>
<name>ssl.client.truststore.type</name>
<value>jks</value>
</property>
<property>
<name>ssl.client.truststore.location</name>
<value>[[/path/to/truststore.jks]]</value>
</property>
<property>
<name>ssl.client.truststore.password</name>
<value>[[password]]</value>
</property>
<property>
<name>ssl.client.truststore.reload.interval</name>
<value>10000</value>
</property>
</configuration> - YARN Archive: You can use this URL to download a ZIP archive that contains the necessary YARN client configuration files
- TLS Truststore: You can use this command to download a Java KeyStore file that contains the certificate authority necessary to submit YARN jobs
- TLS Truststore Password: You can use this command to download the password for the TLS truststore

Phoenix JDBC thick and thin drivers
Apache Phoenix has two kinds of JDBC drivers, thick and thin. The thick driver communicates directly with Apache ZooKeeper and Apache HBase, and the thin driver does this through the Phoenix Query Server. You can connect your application to the Cloudera Operational Database instance using the provided connection and configuration URLs.
- Cloudera command-line interface: Use the
cdp opdb describe-client-connectivity --database-name [***YOUR DATABASE***] --environment-name [***YOUR ENVIRONMENT***]command - Cloudera Operational Database web user interface: Click tab, and then select the Phoenix (Thick) or
Phoenix (Thin) client

Phoenix ODBC driver
ODBC is one of the most established and widely supported API for connecting to and working with databases. Use the Database Open Database Connectivity (ODBC) interface to access the operational database. The ODBC driver is provided by Cloudera as an additional download, but you can also use ODBC drivers from third-party providers. You can download the ODBC driver for your operating system using the links in the Phoenix (ODBC) tab.
- Phoenix ODBC driver download URL: A URL where Phoenix ODBC driver is available. You may need to authenticate again to access this driver
- Phoenix ODBC URL: The basis of a ODBC URL for the Phoenix thin driver to connect to this database

