Preloaded resource-based services and policies
Apache Ranger includes preloaded resource-based services and policies.
-
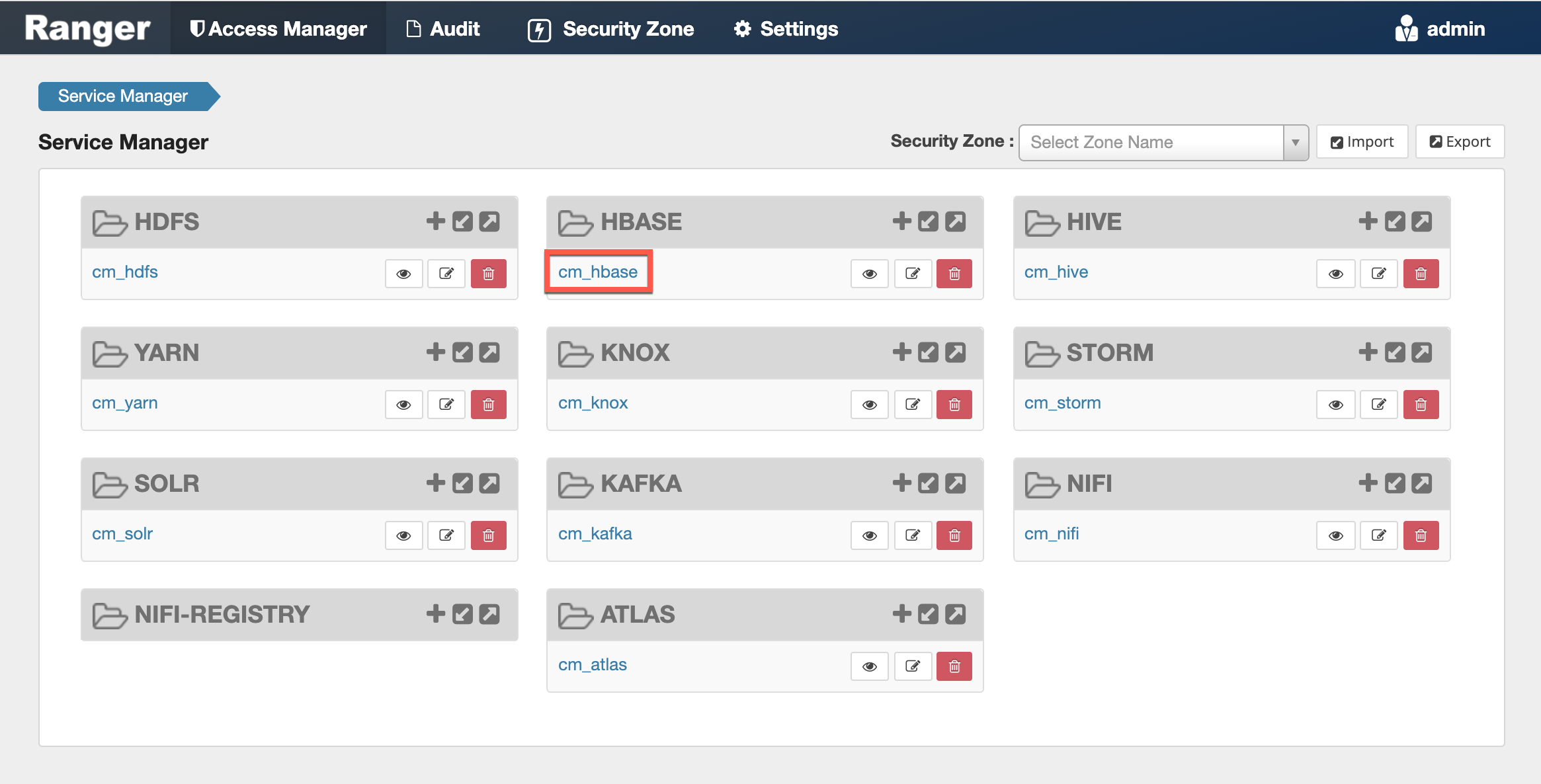
The preloaded resource-based services appear on the Service Manager page for resource-based policies, and are prefixed with "cm_".
-
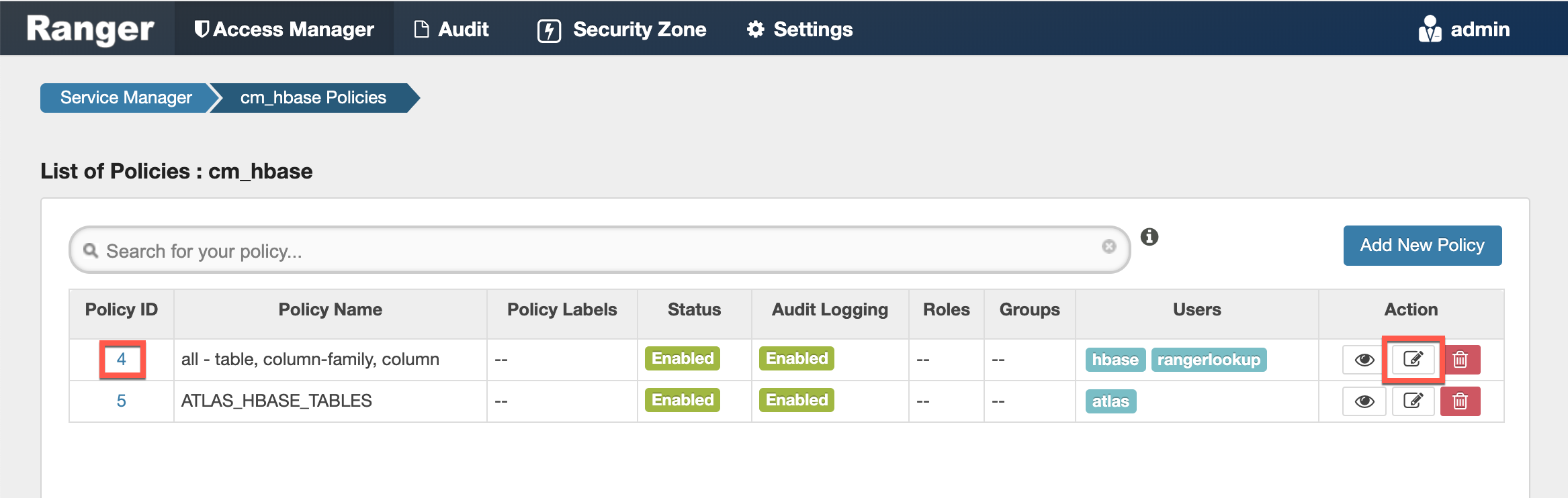
To view the policies for each preloaded service, click the service name. To view policy details, click the applicable edit icon or policy ID number.
cm_atlas
- all - entity-type, entity-classification, entity
-
This is a default policy of type "entity" that gives access to all entities and their classifications for the following users and groups, with the specified permissions:
-
admin, rangerlookup – Read, Create, Update, Delete entity & Add, Update, Remove classification
-
rangertagsync – Read entity
-
public group – Read entity
-
- all - relationship-type, end-one-entity-type, end-one-entity-classification, end-one-entity, end-two-entity-type, end-two-entity-classification, end-two-entity
-
This is a default policy of type "relationship" that gives access to all to all Entity-Relationships between End1-Entity-Type, End1-Entity-Classification, End1-Entity-ID and End2-Entity-Type, End2-Entity-Classification, End2-Entity-ID for the following users and groups, with the specified permissions:
-
admin, rangerlookup – Add, Update, and Remove relationship
-
public group – Add, Update, and Remove relationship
-
- all - atlas-service
-
This is a default policy of type "atlas-service" that gives access to all atlas-services [export, import, server] for the following users, with the specified permissions:
-
admin, rangerlookup – Admin Export & Admin Import
-
- all - type-category, type
-
This is a default policy of type "type-category" that gives access to all type categories [ENUM, ENTITY, CLASSIFICATION, RELATIOSHIP, STRUCT] and type names for the following users, with the specified permissions:
-
admin, rangerlookup – Create, Update, and Delete type
-
- Allow users to manage favorite searches
-
This is a default policy of type "entity-type" that gives access to __AtlasUserProfile & __AtlasUserSavedSearch resources which are internal types for favorite search. This policy provides Read, Create, Update, and Delete Entity permissions to users who create a favorite search.
cm_hbase
- all - table, column-family, column
-
Provides access to all HBase tables, column-families, and columns to the following users, with the specified permissions:
-
hbase, rangerlookup – Read, Write, Create, Admin
-
- ATLAS_HBASE_TABLES
-
Provides access to all HBase column-families and columns in the atlas_janus and ATLAS_ENTITY_AUDIT_EVENTS HBase tables, to the following user, with the specified permissions:
-
atlas – Read, Write, Create, Admin
-
cm_hdfs
- all - path
-
Provides access to all HDFS resource paths to the following users, with the specified permissions:
-
hdfs, rangerlookup – Read, Write, Execute
-
- kms-audit-path
-
Provides access to the
/ranger/audit/kmsresource path to the following user, with the specified permissions:-
keyadmin – Read, Write, Execute
-
cm_hive
- all - global
-
Provides global access to the following users, with the specified permissions:
-
hive, rangerlookup, impala – Select, Update, Create, Drop, Alter, Index, Lock, All, Read, Write, ReplAdmin, Service Admin, Temporary UDF Admin, Refresh
-
- all - database, table, column
-
Provides access to all databases, tables, and columns to the following users, with the specified permissions:
-
hive, rangerlookup, impala – Select, Update, Create, Drop, Alter, Index, Lock, All, Read, Write, ReplAdmin, Service Admin, Temporary UDF Admin, Refresh
- {OWNER} – All
-
- all - database, table
-
Provides access to all databases and tables to the following users, with the specified permissions:
-
hive, rangerlookup, impala – Select, Update, Create, Drop, Alter, Index, Lock, All, Read, Write, ReplAdmin, Service Admin, Temporary UDF Admin, Refresh
- {OWNER} – All
-
- all - database
-
Provides access to all databases to the following users, with the specified permissions:
-
hive, rangerlookup, impala – Select, Update, Create, Drop, Alter, Index, Lock, All, Read, Write, ReplAdmin, Service Admin, Temporary UDF Admin, Refresh
- {OWNER} – All
Also provides access to all databases to the following group, with the specified permissions:
- public – Create
-
- all - hiveservice
-
Provides hiveservice access to the following users, with the specified permissions:
-
hive, rangerlookup, impala – Select, Update, Create, Drop, Alter, Index, Lock, All, Read, Write, ReplAdmin, Service Admin, Temporary UDF Admin, Refresh
-
- all - database, udf
-
Provides database and udf access to the following users, with the specified permissions:
-
hive, rangerlookup, impala – Select, Update, Create, Drop, Alter, Index, Lock, All, Read, Write, ReplAdmin, Service Admin, Temporary UDF Admin, Refresh
- {OWNER} – All
-
- all - url
-
Provides url access to the following users, with the specified permissions:
-
hive, rangerlookup, impala – Select, Update, Create, Drop, Alter, Index, Lock, All, Read, Write, ReplAdmin, Service Admin, Temporary UDF Admin, Refresh
-
- default database tables columns
-
Provides access to all tables and columns in the default database to the following user, with the specified permissions:
-
impala – Create
Also provides access to all tables and columns in the default database to the following group, with the specified permissions:
- public – Create
-
- information_schema database tables columns
-
Provides access to all tables and columns in the information_schema database to the following user, with the specified permissions:
-
impala – Select
Also provides access to all tables and columns in the information_schema database to the following group, with the specified permissions:
- public – Select
-
cm_kafka
- all - topic
-
Provides access to all topics to the following users, with the specified permissions:
-
kafka, rangerlookup – Publish, Consume, Configure, Describe, Create, Delete, Describe Configs, Alter Configs
-
- all - cluster
-
Provides access to all clusters to the following users, with the specified permissions:
-
kafka, rangerlookup – Configure, Describe, Create, Kafka Admin, Idempotent Write, Describe Configs, Alter Configs
-
- all - transactionalid
-
Provides transactionalid access to the following users, with the specified permissions:
-
kafka, rangerlookup – Publish, Describe
-
- all - delegationtoken
-
Provides delegationtoken access to the following users, with the specified permissions:
-
kafka, rangerlookup – Describe
-
- ATLAS_HOOK
-
Provides ATLAS_HOOK topic access to the following users, with the specified permissions:
-
hbase, hive, impala – Publish
-
atlas – Create, Configure, and Consume
-
- ATLAS_ENTITIES
-
Provides ATLAS_ENTITIES topic access to the following users, with the specified permissions:
-
atlas – Create, Configure, and Publish
-
rangertagsync – Consume
-
- ATLAS_SPARK_HOOK
-
Provides ATLAS_SPARK_HOOK topic access to the following user, with the specified permissions:
-
atlas – Create, Configure, and Consume
-
cm_knox
- all - topology, service
-
Provides access to all Knox topologies and services to the following users, with the specified permissions:
-
admin, rangerlookup – Allow
-
cm_nifi
- all - nifi-resource
-
Provides access to all NiFi resource identifiers to the following user, with the specified permissions:
-
rangerlookup – Read, Write
-
cm_solr
- all - collection
-
Provides access to all Solr collections to the following users, with the specified permissions:
-
solr, rangerlookup, ranger, atlas – Query, Update, Others, Solr Admin
-
- RANGER_AUDITS_COLLECTION
-
Provides access to the RANGER_AUDITS_COLLECTION Solr collection to the following users, with the specified permissions:
-
atlas, hbase, hdfs, hive, impala, kafka, knox, nifi, ranger, storm, yarn – Query, Update, Others
-
ranger – Query, Update, Others, Solr Admin
-
cm_storm
- all - topology
-
Provides access to all Storm topologies to the following users, with the specified permissions:
-
storm, rangerlookup – Submit Topology, File Upload, File Download, Kill Topology, Rebalance, Activate, Deactivate, Get Topology Conf, Get Topology, Get User Topology, Get Topology Info, Upload New Credential
-
cm_yarn
- all - queue
-
Provides access to all YARN queues to the following users, with the specified permissions:
-
yarn, rangerlookup – submit-app, admin-queue
-
