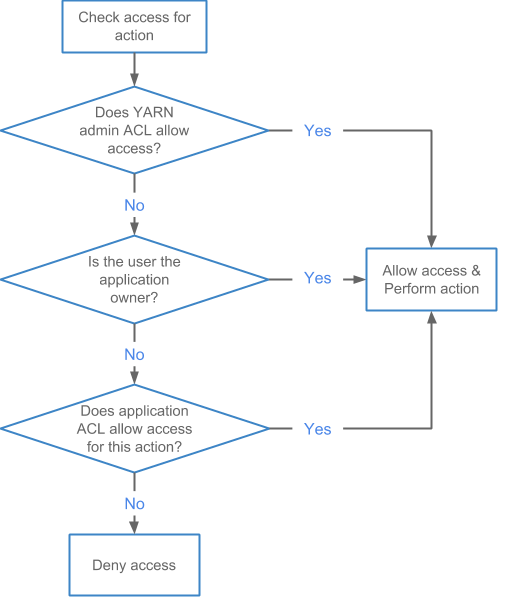
Application ACL evaluation
The better you understand how YARN ACLs are evaluated, the more prepared you will be to define and configure the various YARN ACLs available to you.
For example, if you enable user access in Administrator ACLs, then you must be aware that user may have access to/see sensitive data, and should plan accordingly. So if you are the administrator for an entire cluster, you also have access to the logs for running applications, which means you can view sensitive information in those logs associated with running the application.
Best Practice: A best practice for securing an environment is to set the YARN Admin ACL to include a limited set of users and or groups.
The following diagram shows the evaluation flow for Application ACLs: