Configure Atlas Authorization using Ranger
Use the Ranger Admin UI to add or update policies to control Atlas access.
You can use Ranger policies to control user-access to Atlas metadata and to actions that users can perform in Atlas. The following policies are defined by default:
rangertagsync: the TagSync service users has read access to entity metadata, specifically to entity classifications to be used in Ranger tag-based policies.beacon: the Data Plane service user has full access to entity metadata, classification and relationship creation, and the ability to import and export metadata from Atlas. These privileges allow integration between the Data Catalog (Data Steward Studio) and Atlas.admin: the initial Cloudera Manager superuser has full access to all Atlas actions, including full access to entity metadata, classification and relationship creation, the ability to import and export metadata from Atlas, and the ability to save searches.public: all users are granted access to read Atlas entity metadata and relationships (such as lineage).{USER}: any user who successfully logs in to Atlas can save searches so they are available in subsequent Atlas sessions.
The following video summarizes the steps in Ranger.


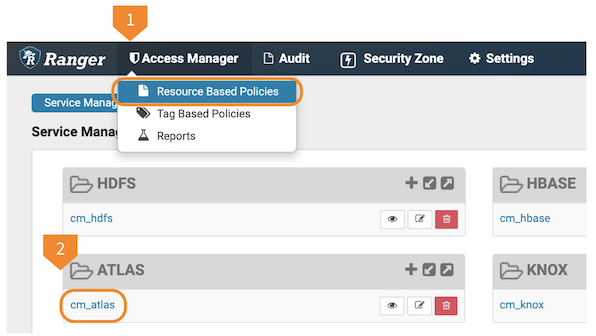
To change Ranger policies for Atlas, your user needs privileges in Ranger to change Resource Based Policies.