Start the Hive shell in a secure cluster
You start the Hive shell using a Beeline command to query Hive. The recommended way to start Hive securely is as an end user authorized by Apache Ranger. As administrator, you set up the end user in the operating system, and configure Ranger policies.
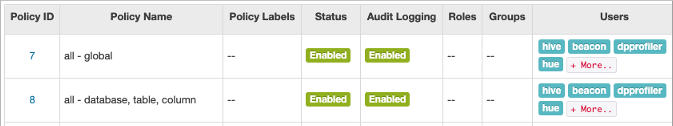
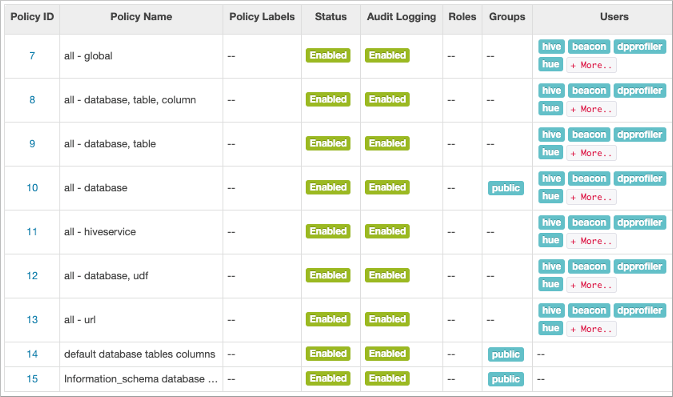
Before starting Hive for the first time, you might want to check that you are covered
by Ranger policies required for basic operations as shown in step 5. All users need
to use the default database, perform operations such as listing
database names, and query the information schema. The preloaded default database
tables columns and information_schema database Ranger policies cover group public
(all users). If these policies are disabled, you cannot use the default database,
perform basic operations such as listing database names, or query the information
schema. For example, if the default database tables columns policy is disabled, the
following error appears if you try to use the default database:
hive> USE default;
Error: Error while compiling statement: FAILED: HiveAccessControlException
Permission denied: user [hive] does not have [USE] privilege on [default]hive -hConnect using simple authentication to HiveServer2 on localhost:10000
beeline -u jdbc:hive2://localhost:10000 username password
Connect using simple authentication to HiveServer2 on hs.local:10000 using -n for username and -p for password
beeline -n username -p password -u jdbc:hive2://hs2.local:10012
Connect using Kerberos authentication with hive/localhost@mydomain.com as HiveServer2 principal
beeline -u "jdbc:hive2://hs2.local:10013/default;principal=hive/localhost@mydomain.com"
Connect using SSL connection to HiveServer2 on localhost at 10000
beeline "jdbc:hive2://localhost:10000/default;ssl=true;sslTrustStore=/usr/local/truststore;trustStorePassword=mytruststorepassword"
Connect using LDAP authentication
beeline -u jdbc:hive2://hs2.local:10013/default <ldap-username> <ldap-password>- HiveServer
- Hive Metastore