Knox SSO Cookie Invalidation
This feature allows a list of pre-configured superusers to invalidate previously issued Knox SSO tokens for (a) particular user(s) in case there is a malicious attack where one (or more) of those users’ SSO tokens get compromised.
Enabling the feature
By default, the feature is disabled. There are 2 separate steps to enable it:
- Go to and enable Knox SSO - Cookie Management Enabled.
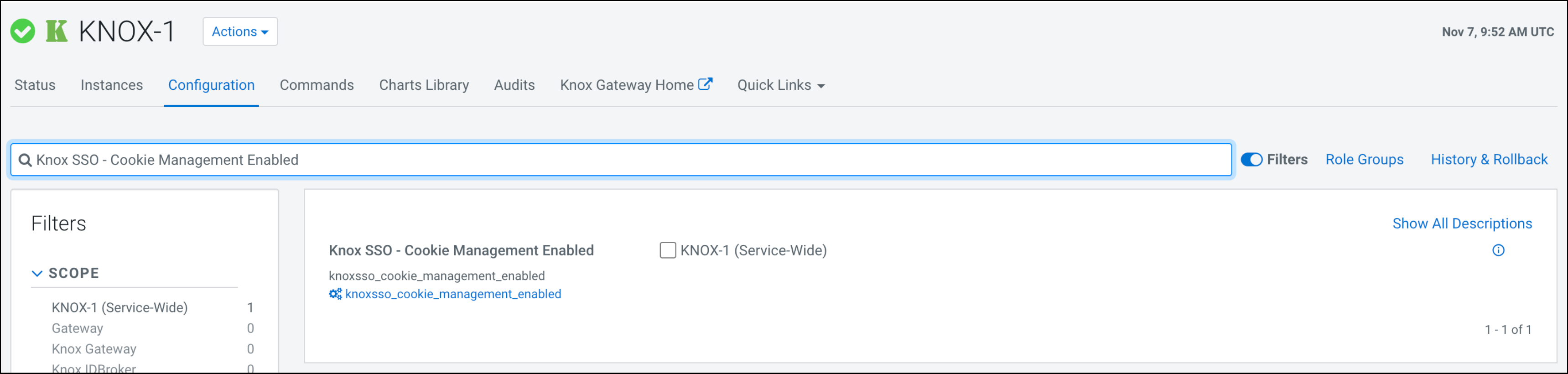
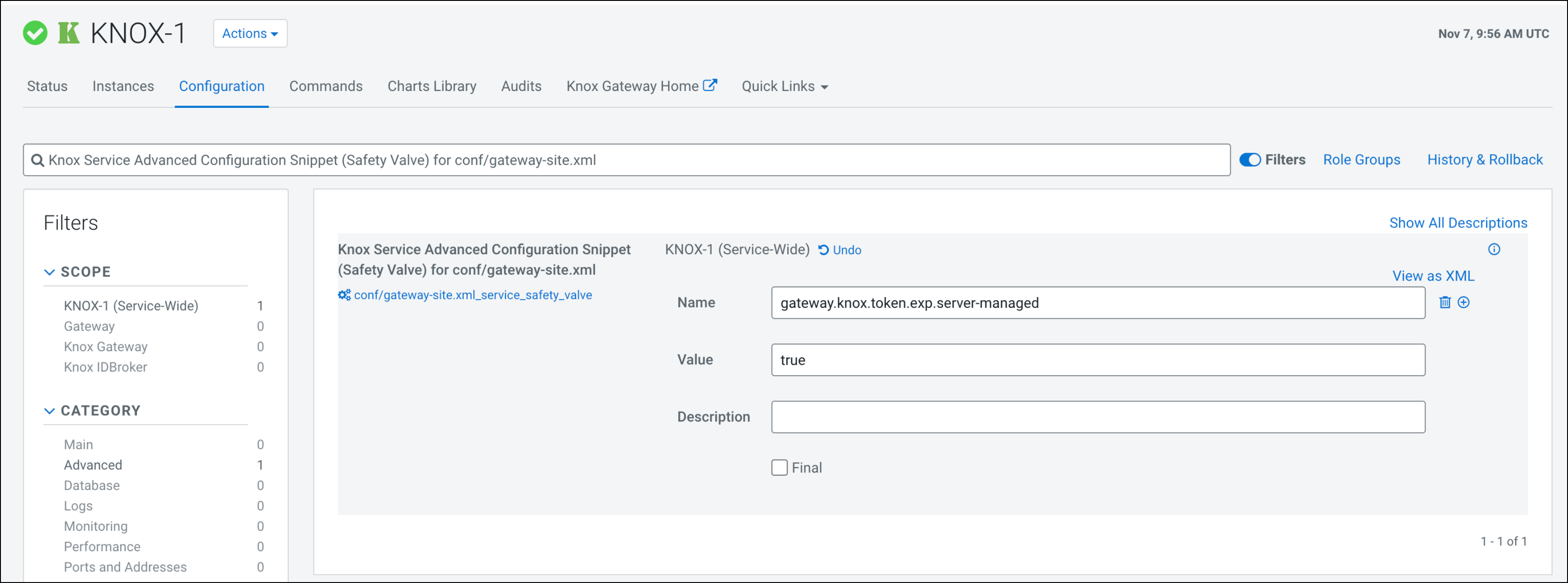
- In Knox Service Advanced Configuration Snippet (Safety Valve) for conf/gateway-site.xml, press
+.
- In Name, type gateway.knox.token.exp.server-managed.
- In Value, type true.
- Click Save Changes(CTRL+S)
Additional configuration
In addition to enabling the feature, you should review and update the following configuration,if needed:
- Knox Home Page - Global Logout Page URL - when the
knoxssotopology is configured to use the Pac4J federation filter (the default configuration in CDP Public Cloud), this configuration is an essential parameter and must not be left empty. This usually points to the logout endpoint of the pre-configured SAML/OIDC callback.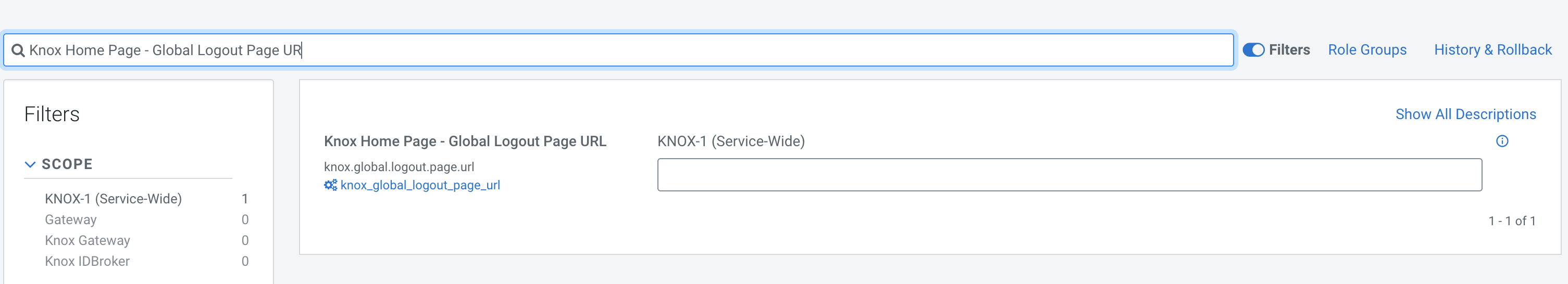
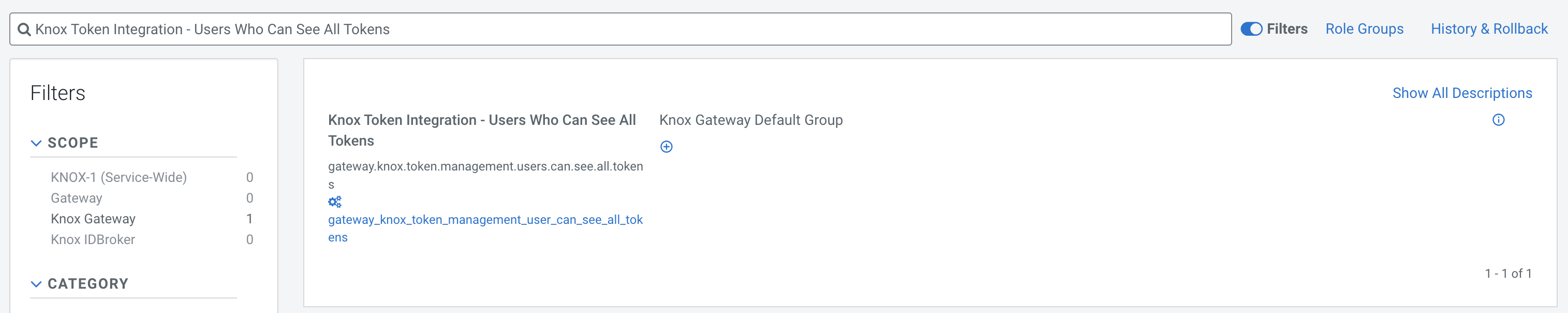
- Knox Token Integration - Users Who Can See All Tokens - A
comma-separated list of usernames that can view all tokens on the Token Management page. By
default, this is an empty list. Each organization should configure this property to a narrowed
set of users, such as security officers, who are authorized to disable SSO cookies in the event
of a security breach.
Resolving access issues after global logout
In certain scenarios, users can still access a service through Knox after performing a global logout. This issue occurs when multiple tabs of the same service are open in the browser, and the global logout is performed in one of the tabs. The issue is caused by cookies that are not invalidated across all tabs, allowing some tabs to retain access to a service or services.
To resolve this issue, add the following configuration parameters to Knox Service Advanced Configuration Snippet (Safety Valve) for conf/gateway-site.xml in Cloudera Manager:
ranger.service.inactivity.timeout=40
atlas.session.timeout.secs=40
knox.global.logout.page.url=<your-idp-logout-url>
After adding the configuration parameters:
- Restart the Knox, Ranger, and Atlas services to apply the changes.
- Test if the global logout now redirects all tabs to the login page instead of the service home page.
How it works
After enabling the feature, every SSO cookie, the result of a login event through the Knox SSO service, will be recorded in the same database that Knox uses for token management purposes. These SSO cookies are included on the Token Management page. If the logged-in user is a configured "superuser" (added in the above-referenced Users Who Can See All Tokens list), that user is capable of narrowing down user tokens, for whom they suspect are the subject of malicious activities, and disabling the active tokens on the UI (either individually or in batches).
Once a Knox SSO cookie is disabled, it cannot be re-enabled or revoked. Knox has its own cleanup strategy to remove expired tokens from the underlying token state repository (a database in CDP Public Cloud) periodically, on a pre-configured schedule.
It is also important to emphasize that the default Time To Live (TTL) value of Knox SSO cookies is set to 1 day by default. It is highly recommended that organizations overview their own UI jobs and reduce this value to as short as possible to reduce the security risk involved here.
