Enabling IP-based access control in Ranger
Learn how to extend Apache Ranger to support authorization based on the location, for example, country/state/city from which the resource is accessed.
- Prepare a location data file containing IP address-to-location detail mappings.
- Register a context-enricher hook that adds the location details to the request.
- Register a policy condition to verify that the client location matches the locations specified in the policy.
- Create or update Apache Ranger policies to specify the locations to allow or deny the access.
IP location data file
IP location data file is a text file containing comma-separated fields. Each line in the file contains the location details for a range of IP addresses. The format of the IP location data file is as follows:
- Each line consists of comma-separated fields.
- The first line is treated as a header, containing names for each field.
- Subsequent lines have location details for a range of IP addresses.
- The first field is the start IP address of the range.
- The second field is the end IP address of the range.
- Other fields have the location data for the IP range specified in first two fields (inclusive)
- IP addresses should be specified as long integers, but the context-enricher can read
addresses in dot-notation when IPInDotFormat for the client IP address is
true.Example:
IP_FROM,IP_TO,COUNTRY_CODE,COUNTRY_NAME,REGION,CITY 10.0.0.255,10.0.3.0,US,United States,California,Santa Clara 20.0.100.80,20.0.100.89,US,United States,Colorado,Broomfield 20.0.100.110,20.0.100.119,US,United States,Texas,Irving
This data format is similar to commercially available data from providers like IP2Location. Depending on the requirements, the data file can either be sourced from a commercial data provider (like IP2Location) or created with deployment-specific details.
Register context enricher
When the Apache Ranger plugin receives an authorization request, the request is passed through registered context enrichers. The context enrichers have access to various request details, including the user, resource accessed, access type, IP address of the accessor, and so on. The context enrichers can update the request context with additional information that can be used while evaluating Ranger policies.
RangerFileBasedGeolocationProvider adds geolocation data to
the request context based on the location details available in a data file. To register the
context enricher for a component (like HDFS/Hive/HBase/..), you need to update the
component’s service-def by including the
following: "contextEnrichers": [
{
"enricher": "org.apache.ranger.plugin.contextenricher.RangerFileBasedGeolocationProvider",
"enricherOptions": {
"FilePath": "/etc/ranger/geo/geo.txt",
"IPInDotFormat": "true"
}
}
]Ensure that the data file is available to the components at the location specified in the above registration (/etc/ranger/geo/geo.txt in this example).
When RangerFileBasedGeolocationProvider receives an authorization request, it
locates the record in the IP location data for the client IP address specified in the request.
If a record is found, each field in the record will be added to the request context.
The following example describes the details of context data being added by the enricher:
- Client IP address: 20.0.100.85
- Matching record in IP location data:
- 20.0.100.80,20.0.100.89,”US”,”United States”,”Colorado”,”Broomfield”
- IP location data header:
- IP_FROM,IP_TO,COUNTRY_CODE,COUNTRY_NAME,REGION,CITY
- Entries added to the request context:
- LOCATION_COUNTRY_CODE=US
- LOCATION_COUNTRY_NAME=United States
- LOCATION_REGION=Colorado
- LOCATION_CITY=Broomfield
Note that the name of context entries are the field names, prefixed with
LOCATION_.
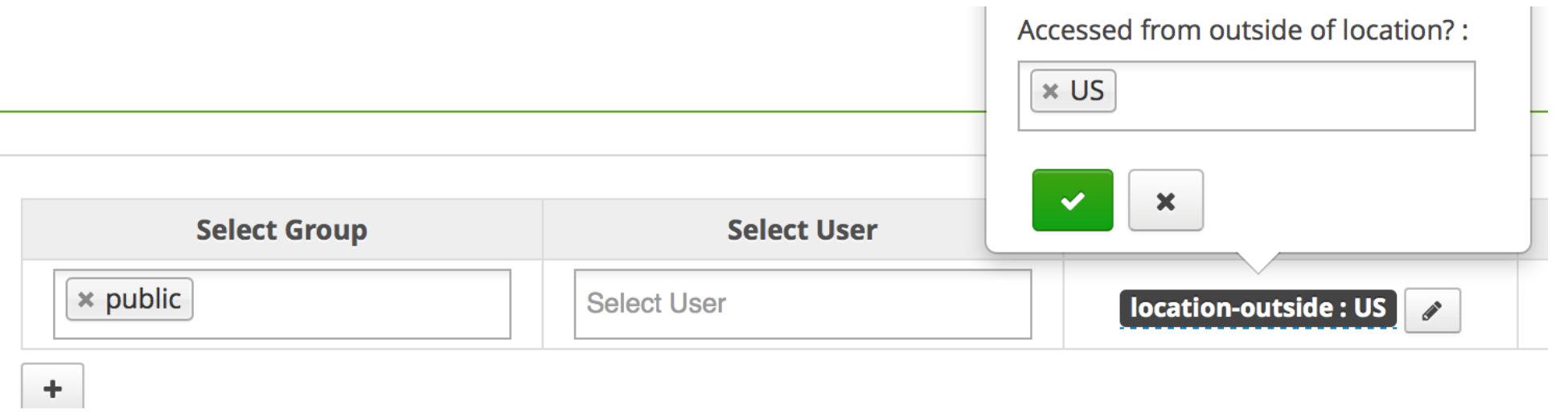
Register policy condition
Apache Ranger provides policy-condition hooks to execute custom conditions while evaluating authorization requests. To determine the authorization result, the Apache Ranger policy engine evaluates the policies that are applicable to the accessed resource. Only when various criteria like user/group, access-type, and policy conditions specified in the policy match the request, the policy engine uses the policy to determine the result.
RangerContextAttributeValueNotInCondition returns true only
when the specified request context value does not match the values specified in the policy.
This can be used to check if the location in request context (which is populated by the
context enricher detailed earlier) is outside the values specified in the policy, for
example, to deny access to requests that originate outside of specified countries. To
register the policy condition for a component (like HDFS/Hive/HBase/..), please update the
component’s service-def by including the
following: "policyConditions": [
{
"itemId": 3,
"name": "location-outside",
"label": "Accessed from outside of location?",
"description": "Accessed from outside of location?",
"evaluator": "org.apache.ranger.plugin.conditionevaluator.RangerContextAttributeValueNotInCondition",
"evaluatorOptions": {
"attributeName": "LOCATION_COUNTRY_CODE"
}
}
]