Wildcards and macros in resource-based policies
Learn about wildcards and macros in resource-based policies.
Wildcard characters in Ranger authorization resource policy
-
*indicates zero or more occurrences of characters -
?indicates a single character
Macros in Ranger policy authoring
In many enterprises, it is customary to create user-accessible data resources (HDFS files/directories, Hive databases/tables, and so on) encoded with the username or some other user-specific attribute value in their names. In such cases, a Ranger administrator needs to author multiple policies addressing these distinct resource names.
USER macro in Ranger provides a generic way to author Ranger policies addressing such relationships between resource names and access permissions for its users to achieve an equivalent access control regime with a single policy or a small number of policies.
Similarly, the OWNER macro in Ranger provides a way to define an access policy for the resources that are owned by the user, thereby restricting others who are not the owner from accessing them unless given specific access.
These two macro definitions make Ranger policy authoring robust and add clarity to the mapping of enterprise-wide and high-level access control regimes to Ranger policy specifications. Fewer policies, in general, lead to significant improvement in capacity and performance in Ranger administration as well as Ranger-enabled components.
USER and OWNER macros in Ranger policy authoring
Learn about USER and OWNER macros and how to use them in Ranger policies to create user-accessible data resources.
USER macro
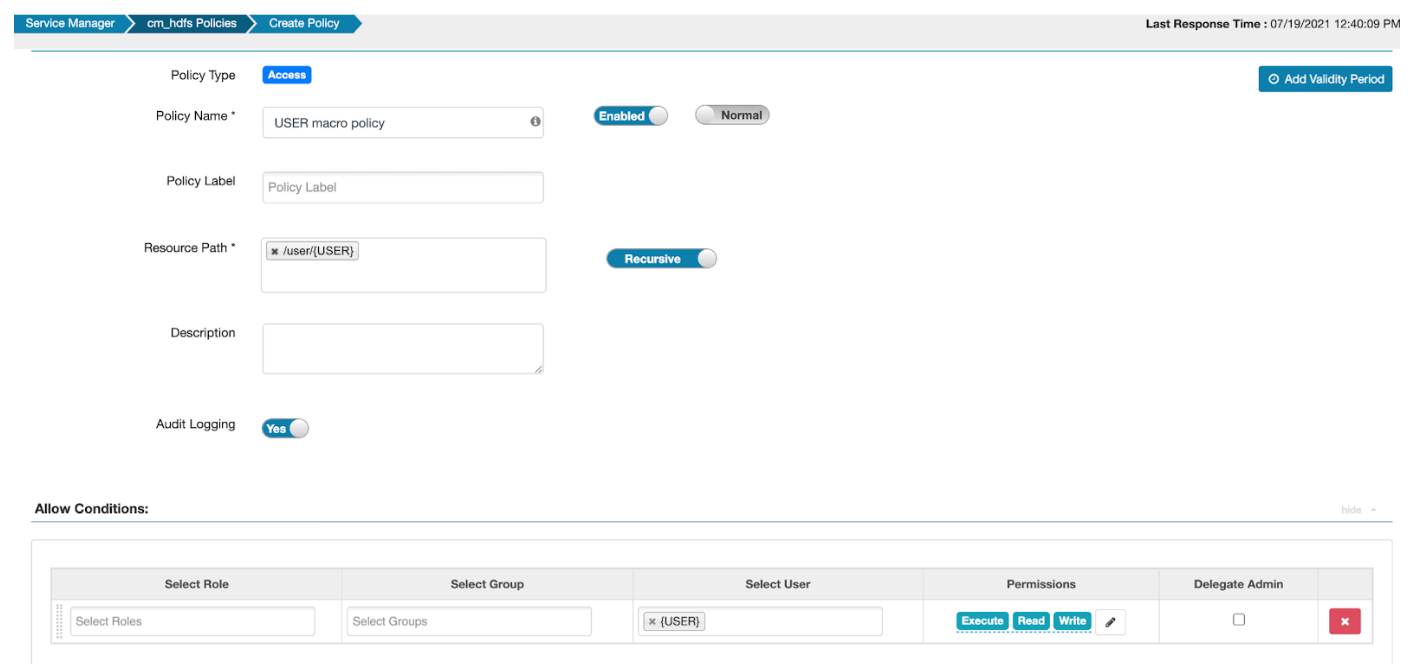
For example, if the user systest is reading data from
/user/systest, this USER macro policy will allow read access. If the user
systest tries to read data from /user/hive, access will
be denied.
By defining this single policy, enterprises can take advantage of controlling access to the user data.
Customizability of USER macro in Ranger
Ranger requires that the {USER} string be used to represent an
accessing user as the user in the policy item in a Ranger policy. However, Ranger provides a
flexible way of customizing the string that is used as shorthand to represent the accessing
user's name in the policy resource specification. By default, Ranger policy resource
specification expects the '{' and '}' characters as delimiters for the string
USER; however, Ranger supports a customizable way of specifying delimiter
characters, escaping those delimiters, and the string USER itself by prefixing
it with another user-specified string on a per resource-level basis in the service definition of
each component supported by Ranger.
"resources": [
{
"itemId": 1,
"name": "path",
"type": "path",
"level": 10,
"parent": "",
"mandatory": true,
"lookupSupported": true,
"recursiveSupported": true,
"excludesSupported": false,
"matcher": "org.apache.ranger.plugin.resourcematcher.RangerPathResourceMatcher",
"matcherOptions": {"wildcard": true, "ignoreCase": false}, "replaceTokens":true, "tokenDelimiterStart":"%", "tokenDelimiterEnd":"%", "tokenDelimiterPrefix":"rangerToken:"}
"validationRegEx":"",
"validationMessage": "",
"uiHint":"",
"label": "Resource Path",
"description": "HDFS file or directory
path"
}
] resource: path=/home/%rangerToken:USER%
user: {USER}
permissions: all, delegateAdmin=trueThe following customizable matcherOptions are available for this feature.
replaceTokens: "true" if shorthand for the user in the resource specification needs to be replaced at runtime with the current-user's name; "false" if the resource specification needs to be interpreted as it is. Default value is "true".tokenDelimiterStart: Identifies the start character of shorthand for the current user in the resource specification. Default value is "{".tokenDelimiterEnd: Identifies the end character of shorthand for the current user in the resource specification. Default value is "}".tokenDelimiterEscape: Identifies escape characters for escapingtokenDelimiterStart/tokenDelimiterEndvalues in the resource specification. Default value is "\".tokenDelimiterPrefix: Identifies a special prefix which, together with the stringUSER, makes up shorthand for the current user's name in the resource specification. Default value is "".
Advanced use of USER macro
This feature, at its core, supports general-purpose identification of special
patterns in the resource specification and their replacement at runtime with other strings to
derive the name of the resource, before matching it with the resource being accessed by the
user. Therefore, it is not limited to the replacement of string USER with the
current user's name; it is just something that is offered out of the box.
In order for Ranger users to use the underlying core functionality, they need to be familiar with interfaces provided by Ranger for customizing Ranger, such as RangerContextEnricher, RangerAccessRequest, and RangerConditionEvaluator.
The following methods are provided to populate and reference context in the RangerAccessRequest object that represents access requests in the policy evaluation engine:
- RangerAccessRequestUtil.setTokenInContext(Map<String, Object> context, String tokenName, Object tokenValue);
- Object RangerAccessRequestUtil.getTokenFromContext(Map<String, Object> context, String tokenName);
An advanced Ranger user needs to provide the following to use the core functionality offered by this feature:
- Provide an implementation of
RangerContextEnricherand include it in the service definition. The implementation ofRangerContextEnricher.enrich()method needs to get the context of theRangerAccessRequestprovided to it and use theRangerAccessRequestUtil.setTokenInContext()API to populate it with a specifictokenName(such asUSER) and its value, derived based on some runtime information and enricher's configuration parameters. - Customize the component's service definition with appropriate
matcherOptionsfor each resource definition supported by it as described above in the customizability section. - Provide an implementation of
RangerConditionEvaluatorand include it in the service definition. The implementation of theRangerConditionEvaluator.isMatched()API needs to retrieve the value of thetokenNamefrom the request’s context using theRangerAccessRequestUtil.getTokenFromContext()API, and return the appropriate result. - Author a Ranger policy with the resource specification containing the
tokenNameto implement appropriate access control for the resource name built at runtime by Ranger.
OWNER macro
Let us use the following example to understand the usage of OWNER macro.
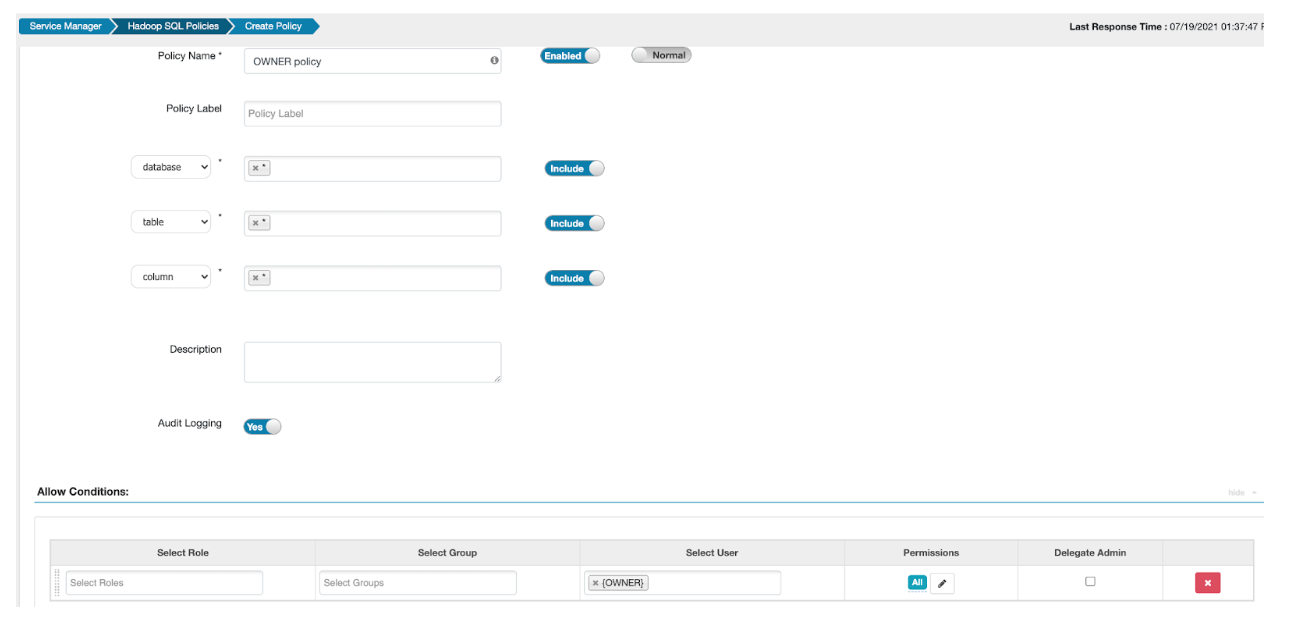
- In the Allow Conditions Ranger policy, for the user entry, the
{OWNER}macro is used with the permissionAll.
- This Owner policy gives the necessary permission to the resources (database/table/column) that the user owns.
- Other resources which are not owned by the user are not allowed to be accessed.
- This single policy gives the flexibility to provide access to the owner of the resources.
