User authorization
The user authorization model used by Cloudbreak allows resource sharing between users.
When a Cloudbreak instance is configured with an LDAP or Active Directory, the LDAP/AD users can share Cloudbreak resources with other users via workspaces. Any user can create a workspace and invite other users to that workspace, granting them specific access rights. Once a workspace is created, users who are part of it share all resources, such as clusters, blueprints, recipes, and so on, created as part of that workspace.
This user authorization model is summarized in the following diagram:
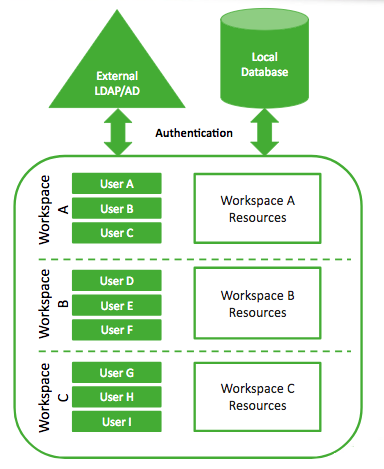
As the diagram illustrates:
-
Users can be members of multiple workspaces and access any resources created within these workspaces (shared).
-
Resource sharing allows users to access resources created by other users within the same workspace (credentials, clusters, blueprints, recipes, images, and external sources) but resources cannot be shared or moved between workspaces.
Example scenario
Consider the following example: Mark, Sarah, and Jeff work on the same project and instead of accessing Cloudbreak independently, they would like to share the same HDP clusters to run their workloads. Therefore, Mark creates a workspace called “Marketing-analytics” and invites Sarah and Jeff, granting them the read and write access. Now the three of them, in addition to accessing their private Cloudbreak accounts, can access the “Marketing-analytics” account and have read and write all the resources. Mark is still the only one who can manage the workspace. Once he receives the invite, Jeff accesses the “Marketing-analytics” workspace, registers a blueprint and a few recipes, and then creates a cluster. Now all three of them can access these resources as part of the “Marketing-analytics” workspace.
At the same time, Sarah is involved in another project, which requires her to work with a separate group of people. Therefore, she decides to create a separate workspace called “Finance-reports” and share it with Richard and Monica, granting them read and write access to all the resources. Now in addition to having her own Cloudbreak account, Sarah is part of two workspaces “Marketing-analytics” and “Finance-reports”.
Workspace permissions
| User type | Permission | Access |
|---|---|---|
| Workspace owner | All: Read | Create/edit/delete resources |
| Workspace user | All: Write | View resources |
| Workspace user | Workspace: Manage |
|
Access permissions can be assigned per workspace, without the ability to restrict them per specific resource type (clusters, blueprints, and so on). This means that all members of a given workspace have access to all resources.
The user who creates a workspace is automatically assigned the "All: Read", "All: Write", and "Workspace: Manage" access permission.

