Gateway configuration
The Gateway Configuration options allow you to change the settings of the gateway, which Cloudbreak installs and configures by default.
When creating a cluster, Cloudbreak installs and configures a gateway, powered by Apache Knox, to protect access to the cluster resources:
- This gateway is installed on the same host as the Ambari server.
-
By default, transport layer security on the gateway endpoint is via a self-signed SSL certificate on port 8443. This is illustrated on the following diagram:
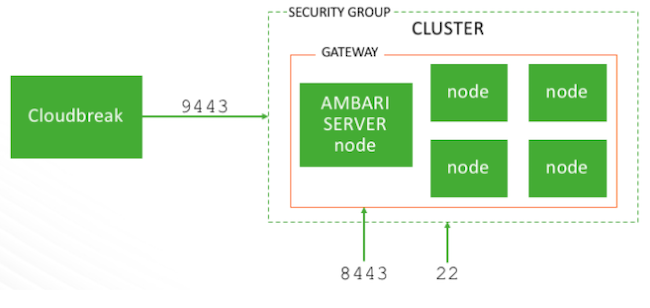
- The cluster resources that are accessible through the gateway are determined by the settings provided on the Gateway Configuration page of the basic create cluster wizard.
- By default, the gateway is deployed and Ambari is proxied through the gateway.
- The choice of cluster services to expose and proxy through the gateway depends on your blueprint. Cloudbreak analyzes your blueprint and provides a list of services that can be exposed through the gateway. You should review this list and select the services that should be proxied through the gateway.
- If you do not enable the gateway, or you do not expose Ambari (or any other service) through the gateway, you must configure access to those services on the security group on your own.
- Once a cluster is running, the gateway configuration selected during cluster create cannot be altered or reversed.

