Connecting to a Secure Service that Supports Delegation Tokens
About This Task
SAM uses delegation tokens when possible, when talking to secure streaming services. The concept of delegation token is introduced to avoid frequent authentication checks against Kerberos(AD/MIT). After the initial authentication against Namenode using Kerberos, subsequent authentication are done without a Kerberos service ticket(TGT). Once the client authentication with Kerberos for Namenode is successful, the client receives a delegation token from the Namenode.This token has an expiration and max issue date but can be reviewed.
A delegation token is secret key shared with the Storm/NameNode/HBase which provides a mechanism for Storm/NameNode/HBase to impersonate a user to perform an operation. Delegation tokens are supported for the following services: Storm, HDFS, Hive, HBase.
You can use Storm’s Nimbus service to get delegation tokens on behalf of the topology submitter user. Nimbus can get HDFS, HBase and other delegation tokens associated with the user who submitted the topology and can push it to the users stream application. This decreases operational/deployment complexity because you do not have to distribute keytabs to all possible key tabs.
Example
If your application is going to interact with secure HBase, your bolts/states needs to be
authenticated by HBase. Typically, you are required to have storm.keytab.file on
all the potential worker hosts. If you have multiple topologies on a cluster, each with
different user, you will have to create multiple keytabs and distribute it to all
workers.
With SAM, you can configure Nimbus to automatically get delegation tokens on behalf of the topology submitter user. To do this in SAM, you can configure a single principal and keytab in SAM for a given application and this principal is used by Nimbus to impersonate the user/app. The only requirement is that the keytab for this principal must reside on the host where Nimbus is located. To configure this single principal that will be used by Nimbus to impersonate the user/app when connecing to secure big data services like HBase, HDFS, Hive, do the following:
Steps
Click into your stream application, and then click .
Click the icon (
 ) located on top right of the stream application.
) located on top right of the stream application.Select the Security tab.
Select the principal and and Keytab path. SAM automatically populates all the principal and key tabs located on the Nimbus Host to make this easier. Then click Ok.
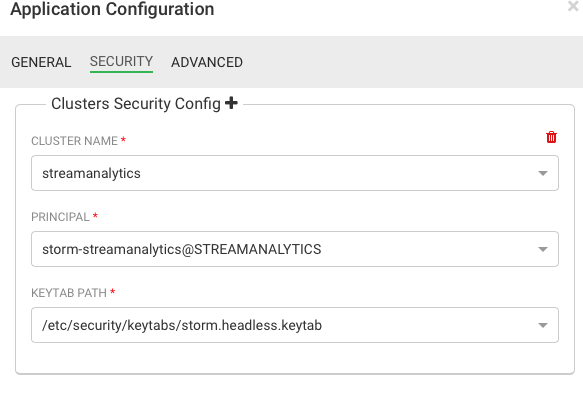
Result
When user X deploys the application, Nimbus uses the principal and the keytab configured above to impersonate user X when interacting with the big data services in the application.