Cluster Component Configuration Updates
After you have enabled Kerberos, some cluster components require additional configuration updates.
SAM Configuration Changes
Steps
From the Ambari UI, select Admin | Kerberos.
From Ambari Principals, set the SAM principal name:
streamline_principal_name : memo the principal without @${realm} – (1)From Ambari Infra | Configs | Advanced | Advanced infra-solr-security-json, add the following to the bottom text box. Replace <<streamline>> (bolded) to streamline principal (1) before pasting.
{ "authentication": { "class": "org.apache.solr.security.KerberosPlugin" }, "authorization": { "class": "org.apache.ambari.infra.security.InfraRuleBasedAuthorizationPlugin", "user-role": { "{{infra_solr_kerberos_service_user}}@{{kerberos_realm}}": "admin", "{{logsearch_kerberos_service_user}}@{{kerberos_realm}}": ["{{infra_solr_role_logsearch}}", "{{infra_solr_role_ranger_admin}}", "{{infra_solr_role_dev}}"], "<<streamline>>@{{kerberos_realm}}": ["{{infra_solr_role_logsearch}}", "{{infra_solr_role_ranger_admin}}", "{{infra_solr_role_dev}}"], "{{logfeeder_kerberos_service_user}}@{{kerberos_realm}}": ["{{infra_solr_role_logfeeder}}", "{{infra_solr_role_dev}}"], "{{atlas_kerberos_service_user}}@{{kerberos_realm}}": ["{{infra_solr_role_atlas}}", "{{infra_solr_role_ranger_audit}}", "{{infra_solr_role_dev}}"], {% if infra_solr_ranger_audit_service_users %} {% for ranger_audit_service_user in infra_solr_ranger_audit_service_users %} "{{ranger_audit_service_user}}@{{kerberos_realm}}": ["{{infra_solr_role_ranger_audit}}", "{{infra_solr_role_dev}}"], {% endfor %} {% endif %} "{{ranger_admin_kerberos_service_user}}@{{kerberos_realm}}": ["{{infra_solr_role_ranger_admin}}", "{{infra_solr_role_ranger_audit}}", "{{infra_solr_role_dev}}"] }, "permissions": [ { "name" : "collection-admin-read", "role" :null }, { "name" : "collection-admin-edit", "role" : ["admin", "{{infra_solr_role_logsearch}}", "{{infra_solr_role_logfeeder}}", "{{infra_solr_role_atlas}}", "{{infra_solr_role_ranger_admin}}"] }, { "name":"read", "role": "{{infra_solr_role_dev}}" }, { "collection": ["{{logsearch_service_logs_collection}}", "{{logsearch_audit_logs_collection}}", "history"], "role": ["admin", "{{infra_solr_role_logsearch}}", "{{infra_solr_role_logfeeder}}"], "name": "logsearch-manager", "path": "/*" }, { "collection": ["vertex_index", "edge_index", "fulltext_index"], "role": ["admin", "{{infra_solr_role_atlas}}"], "name": "atlas-manager", "path": "/*" }, { "collection": "{{ranger_solr_collection_name}}", "role": ["admin", "{{infra_solr_role_ranger_admin}}", "{{infra_solr_role_ranger_audit}}"], "name": "ranger-manager", "path": "/*" } ] } }Restart Ambari Infra.
Druid Configuration Changes
Update the Druid property druid.hadoop.security.spnego.excludedPaths to the following value:
["/status", "/druid/worker/v1", "/druid/indexer/v1"]
HDFS Configuration Changes
If you are going to use the HDFS processor in your
application in secure mode, add the following properties in the HDFS service under
custom core-site.xml.
| Property Name | Value |
|---|---|
| hadoop.proxyuser.$principal_you_configured_in_sam_app_settings.groups | * |
| hadoop.proxyuser.$principal_you_configured_in_sam_app_settings.hosts | * |
Example
In SAM, you have configured the following principal and keytab under Application Settings:
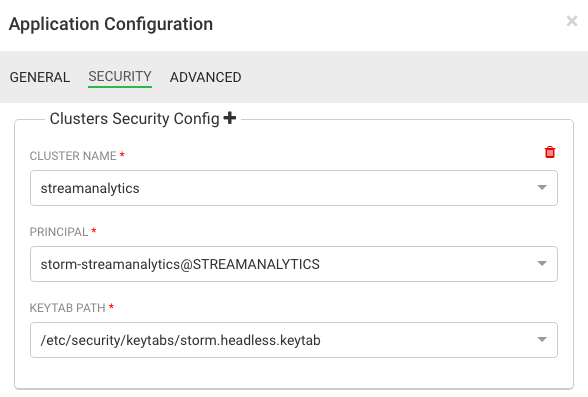
The configuration for the 2 HDF properties is:
hadoop.proxyuser.storm-streamanalytics.hosts=* hadoop.proxyuser.storm-streamanalytics.groups=*
HBase Configuration
In the HBase service, under custom hbase-site.xml add the
following properties
hbase.thrift.support.proxyuser=true
hbase.regionserver.thrift.http=true
In HDFS service, add the following under custom core-site.xm
hadoop.proxyuser.streamline-streamanalytics.hosts=*
hadoop.proxyuser.streamline-streamanalytics.groups=*