Known Issues
Summary of known issues for this release.
-
Issue:
A known issue in Chrome 92.x causes significant slowness in the NiFi UI and may lead to high CPU consumption. For more information, see the Chrome Known Issues documentation at 1235045.
Workaround:
Use another version of Chrome or a different browser.
-
Issue:
Configuration parameter
registry.sso.enabledwas not found in configurations dictionary.Workaround:
Run the following command on the Ambari server node:/var/lib/ambari-server/resources/scripts/configs.py -a set -l <ambari-server-hostname> -n <cluster_name> -u admin -p {admin_user_password} -c registry-sso-config -k registry.sso.enabled -v <either true or false> -
Issue:
JDK 8u271, JDK 8u281, and JDK 8u291 may cause socket leak issues in NiFi due to JDK-8245417 and JDK-8256818. Pay attention to the build version of your JDK because some later builds are fixed as described in JDK-8256818.
Workaround:
Consider using a more recent version of the JDK like 8u282, or builds of the JDK where the issue is fixed.
-
Issue:
SAM app with storm-druid sink throws exception.
Workaround:
There is no workaround for this issue.
-
Issue:
When you upgrade HDF from an older version (pre 3.5.0.0) on HDP, Nifi Registry might fail during the start with the following error message:
Caused by: org.xml.sax.SAXParseException: cvc-complex-type.2.4.b: The content of element 'providers' is not complete. One of '{eventHookProvider, extensionBundlePersistenceProvider}' is expected.Workaround
To resolve this issue, add the following configuration toAdvanced nifi-registry-providers-envin Ambari:<extensionBundlePersistenceProvider> <class>org.apache.nifi.registry.provider.extension.FileSystemBundlePersistenceProvider</class> <property name="Extension Bundle Storage Directory">{{nifi_registry_internal_dir}}/extension_bundles</property> </extensionBundlePersistenceProvider> -
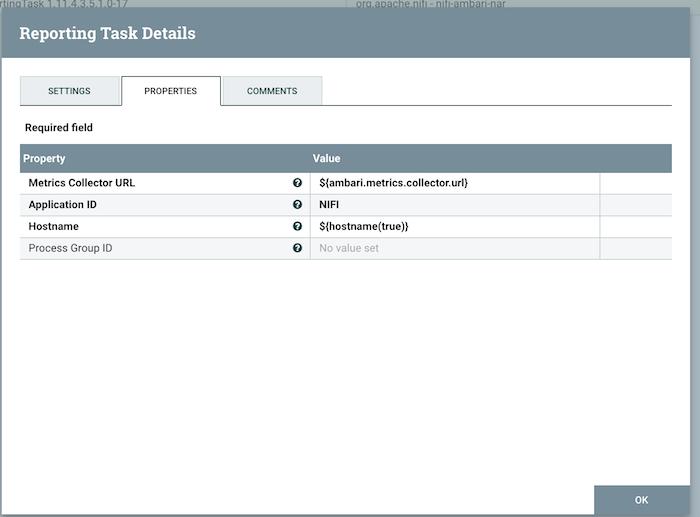
Issue:
The default Ambari reporting task in NiFi is not configured correctly and the NiFi metrics are not properly displayed in Ambari even though there is no reported error.
Workaround:
In the reporting task configuration, change the Application ID property to an uppercase value: NIFI. For example:
- TSB-497: CVE-2021-27905: Apache Solr SSRF vulnerability with the Replication
handler
The Apache Solr ReplicationHandler (normally registered at "/replication" under a Solr core) has a "masterUrl" (also "leaderUrl" alias) parameter. The “masterUrl” parameter is used to designate another ReplicationHandler on another Solr core to replicate index data into the local core. To help prevent the CVE-2021-27905 SSRF vulnerability, Solr should check these parameters against a similar configuration used for the "shards" parameter.
For the latest update on this issue, see the corresponding Knowledge article: TSB 2021-497: CVE-2021-27905: Apache Solr SSRF vulnerability with the Replication handler

