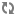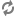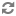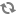Encryption over the HTTP protocol is implemented with the support for SSL in various HTTP listeners across Hadoop cluster.
To enable WebHDFS to listen for HTTP over SSL, you must configure SSL on the NameNode
and all DataNodes by setting dfs.https.enable=true in the
hdfs-site.xml file.
Most commonly SSL is configured to authenticate only the Server, a mode called 1-way
SSL. For 1-way SSL you only need to configure the keystore on the NameNode and each
DataNode, using the properties shown in the table below. These parameters are set in the
ssl-server.xml file on the NameNode and each DataNodes.
SSL can also be configured to authenticate the client, a m ode called mutual
authentication or 2-way SSL. To configure 2-way SSL also set
dfs.client.https.need-auth=true in the
hdfs-site.xml file on the NameNode and each DataNode.
| Property | Default Value | Description | 1-way | 2-way |
|---|---|---|---|---|
| ssl.server.keystore.type | JKS | The type of the keystore, JKS = Java Keystore, the de-facto standard in Java | Y | Y |
| ssl.server.keystore.location | None | The location of the keystore file | Y | Y |
| ssl.server.keystore.password | None | The password to open the keystore file | Y | Y |
| ssl.server truststore.type | JKS | The type of the trust store | N | Y |
| ssl.server.truststore.location | None | The location of the truststore file | N | Y |
| ssl server.truststore.password | None | The password to open the trustsore | N | Y |
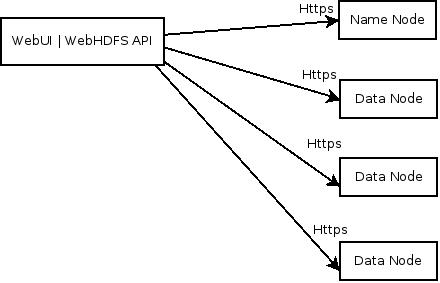
The following diagram shows an HTTP or REST client's interaction with the NameNode and the DataNodes over HTTPS.