Managing Auditing in Ranger: Access
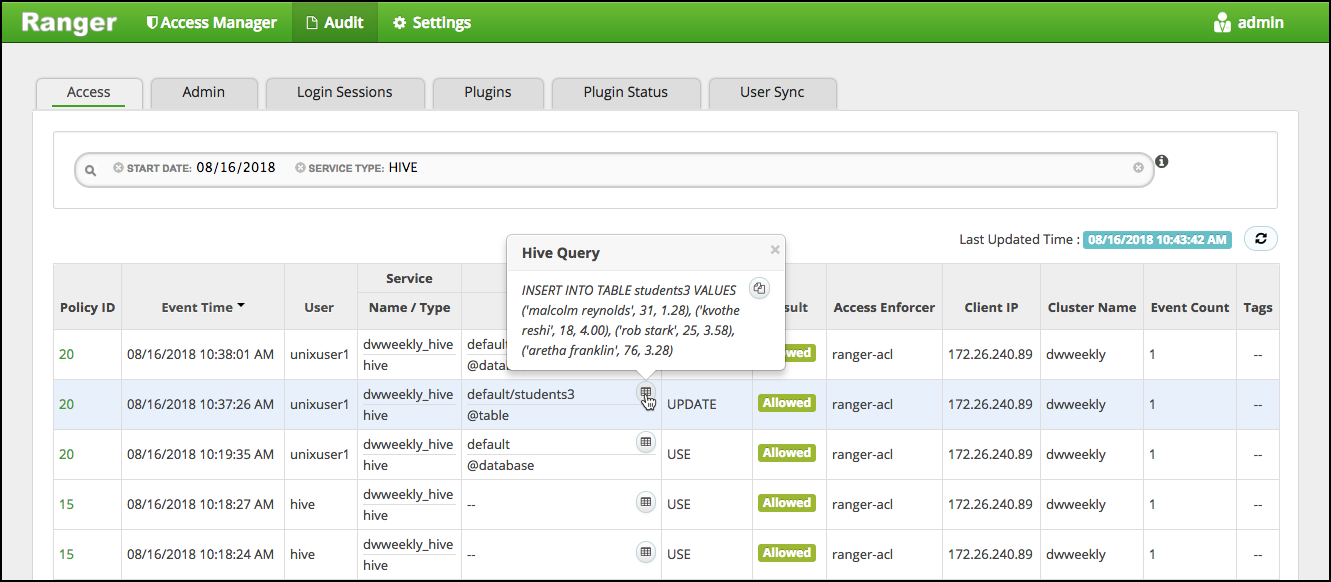
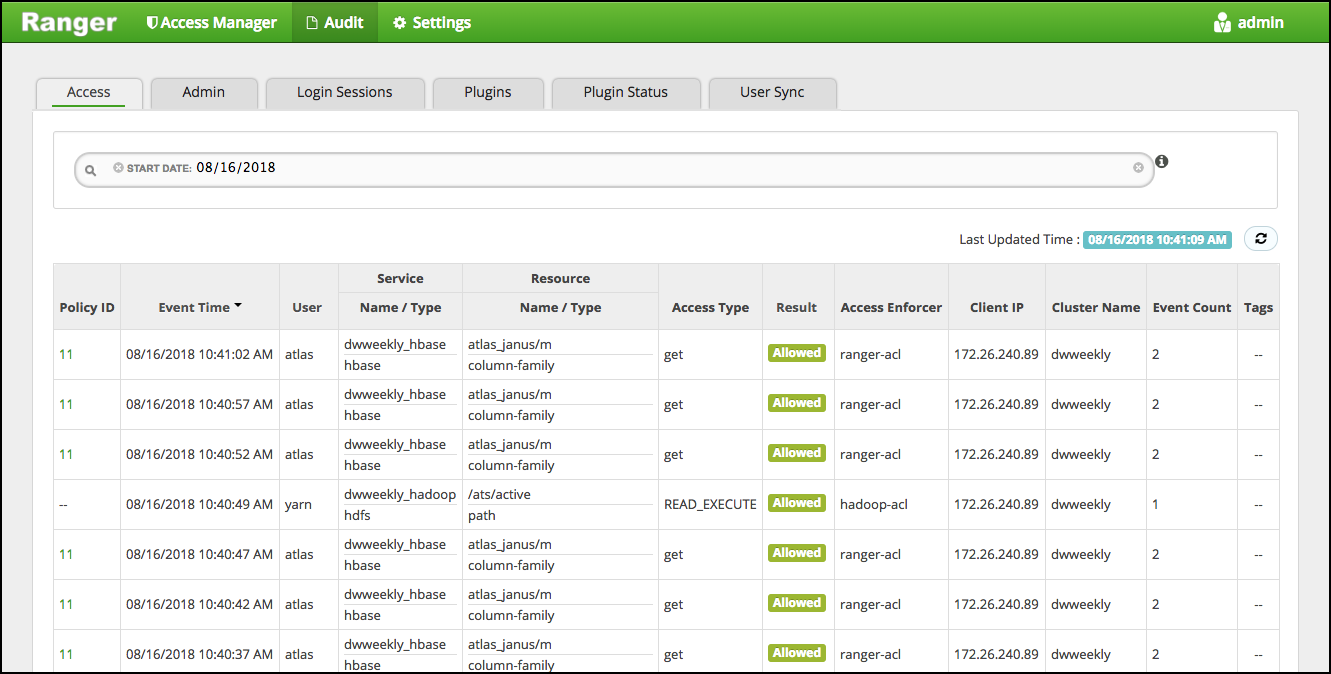
In Ranger, the Access page provides service activity data for all Policies that have Audit set to On. The default service Policy is configured to log all user activity within the Service. This default policy does not contain user and group access rules.
You can filter the data based on the following criteria:
| Search Criteria | Description |
|---|---|
| Access Enforcer | Ranger (ranger-acl) or Hadoop (hadoop-acl) |
| Access Type | Type of access user attempted (E.G., REVOKE, GRANT, OPEN, USE). |
| Client IP | IP address of the user system that tried to access the resource. |
| Result | Shows whether the operation was successful or not. |
| Service Name / Type | The name and type of the service that the user tried to access. |
| Resource Name / Type |
The resource name and type of the service that the user tried to access. For Hive events, this field will display the Hive query the user ran. |
| Start Date, End Date | Filters results for a particular date range. |
| User | Name of the user which tried to access the resource. |
| Cluster Name | Cluster name. Can be defined under
Ambari>component>Configs>Advanced>ranger-component-audit
file, using
ranger.plugin.component.ambari.cluster.name=cluster_name
. |
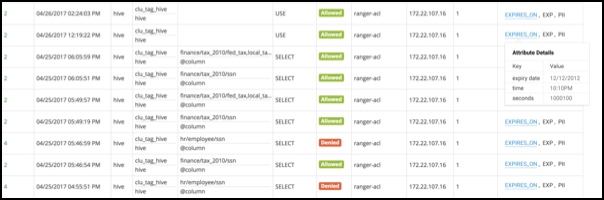
Ranger Access showing tag attribute details:
Ranger Access showing user 'unixuser1' running a Hive query: