Configure Zeppelin for a Kerberos-Enabled Cluster
Use the following steps to configure Apache Zepellin for a Kerberos-enabled cluster.
The Zeppelin daemon needs a Kerberos account and keytab to run in a Kerberized cluster.
-
When you enable Kerberos on an Ambari-managed cluster, Ambari configures Kerberos for Zeppelin and automatically creates a Kerberos account and keytab for it. For more information, see "Configuring Ambari and Hadoop for Kerberos" in the HDP Apache Ambari Security guide.
-
If your cluster is not managed with Ambari and you plan to enable Kerberos for the Zeppelin server, see "Creating Service Principals and Keytab Files for HDP" in the HDP Security guide.
After configuring Kerberos for Zeppelin in Ambari, you can find all related settings on
the Zeppelin Interpreter settings page, as shown in the following image for the
%spark interpreter. If you configured Kerberos from Ambari, no
further action is needed. Changes in values for keytabs and principals are managed by
Ambari, and if Kerberos is disabled, Ambari deletes keytab and principal values.
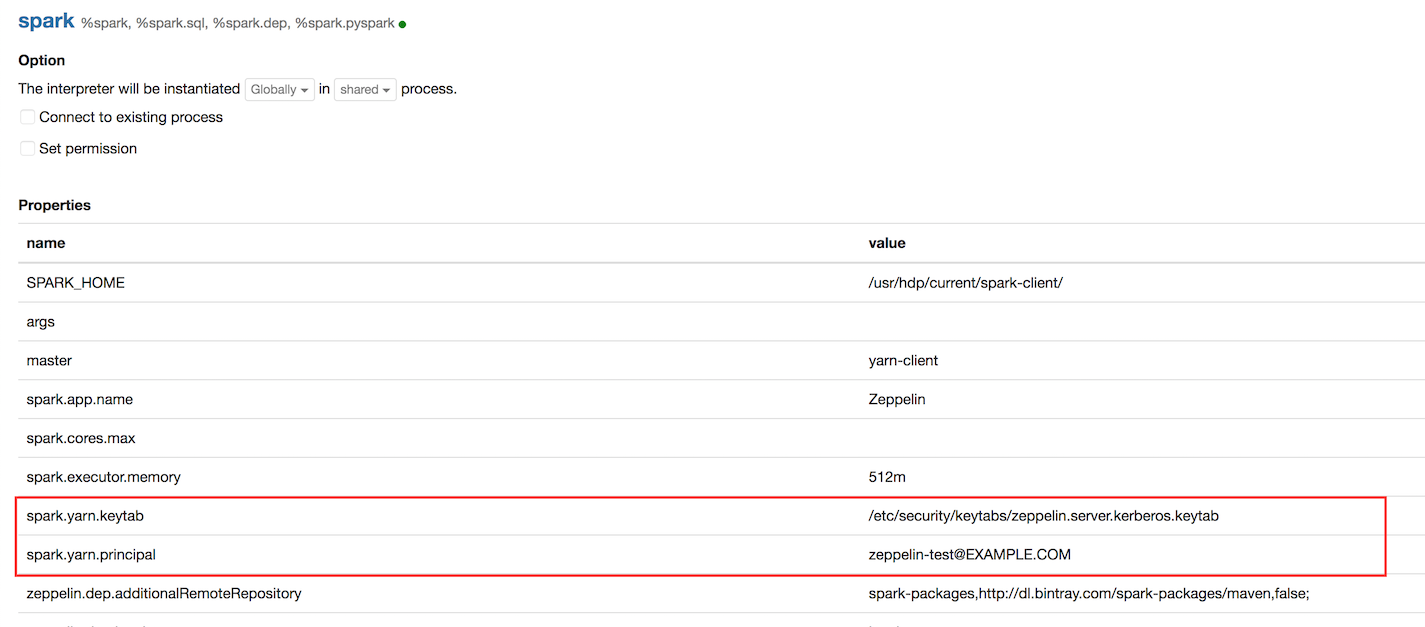
For clusters not managed by Ambari, note that every interpreter that supports Kerberos
has two configuration properties: keytab and principal. In addition, the Shell
interpreter (%sh) has a property for specifying authentication method:
zeppelin.shell.auth.type. Set authentication method to
KERBEROS for a Kerberos-enabled cluster; otherwise the value should
be empty.
The following table lists properties used for keytabs and principals for each associated interpreter.
| Interpreter | Keytab Property | Principal Property |
|---|---|---|
| %jdbc | zeppelin.jdbc.keytab.location | zeppelin.jdbc.principal |
| %livy | zeppelin.livy.keytab | zeppelin.livy.principal |
| %sh | zeppelin.shell.keytab.location | zeppelin.shell.principal |
| %spark | spark.yarn.keytab | spark.yarn.principal |

