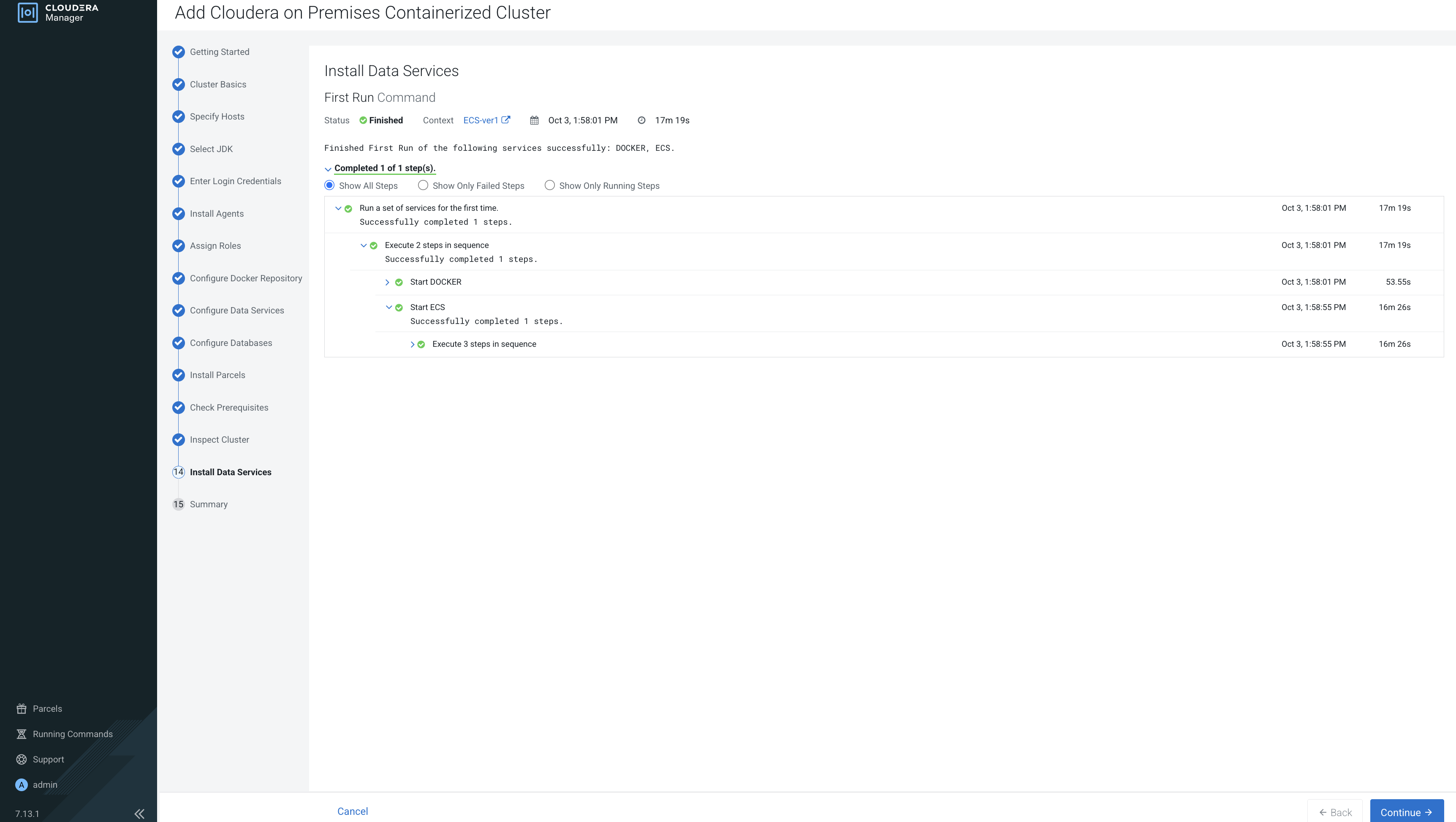
Installing Cloudera Data Services on premises using Cloudera Embedded Container Service
Learn about installing Cloudera Data Services on premises with the Cloudera Embedded Container Service.
If the installation fails, and you see the following error message in the
stderr output during the Install Longhorn
UI step, retry the installation by clicking the
Resume button:
++ openssl passwd -stdin -apr1 + echo 'cm-longhorn:$apr1$gp2nrbtq$1KYPGI0QNlFJ2lo5sV62l0' + kubectl -n longhorn-system create secret generic basic-auth --from-file=auth + rm -f auth + kubectl -n longhorn-system apply -f /opt/cloudera/cm-agent/service/ecs/longhorn-ingress.yaml Error from server (InternalError): error when creating "/opt/cloudera/cm-agent/service/ecs/longhorn-ingress.yaml":
Internal error occurred: failed calling webhook "validate.nginx.ingress.kubernetes.io": Post "https://rke2-ingress-nginx-controller-admission.kube-system.svc:443/networking/v1/ingresses?timeout=10s": x509: certificate signed by unknown authority
In Cloudera Data Services on premises deployments using RKE2,
container life cycle events, such as container mounts, start, or stop, are
logged to the /var/log/messages file through
systemd.
Since, Cloudera Data Services on premises installation is not
OS-integrated, no systemd, rsyslogd, or logrotate configurations are delivered.
As a result, these verbose messages are flooding
/var/log/messages, risking disk pressure on
/var, which may lead to stability or availability
issues.
/var/log/messages
file:- Product packaging for Cloudera Data Services on premises (especially for Cloudera Embedded Container Service on RKE2) must
include:
-
The sample
rsyslog.dconfiguration orjournaldfilters to redirect container lifecycle logs to a separate file. For example, to/var/log/rancher-container-events.log. -
Safety valve-based injection method, if feasible, or post-install script guidance for such OS-level logging configurations.
-
- Alternatively, consider filtering or rate-limiting verbose lifecycle logs at the container runtime layer if possible.
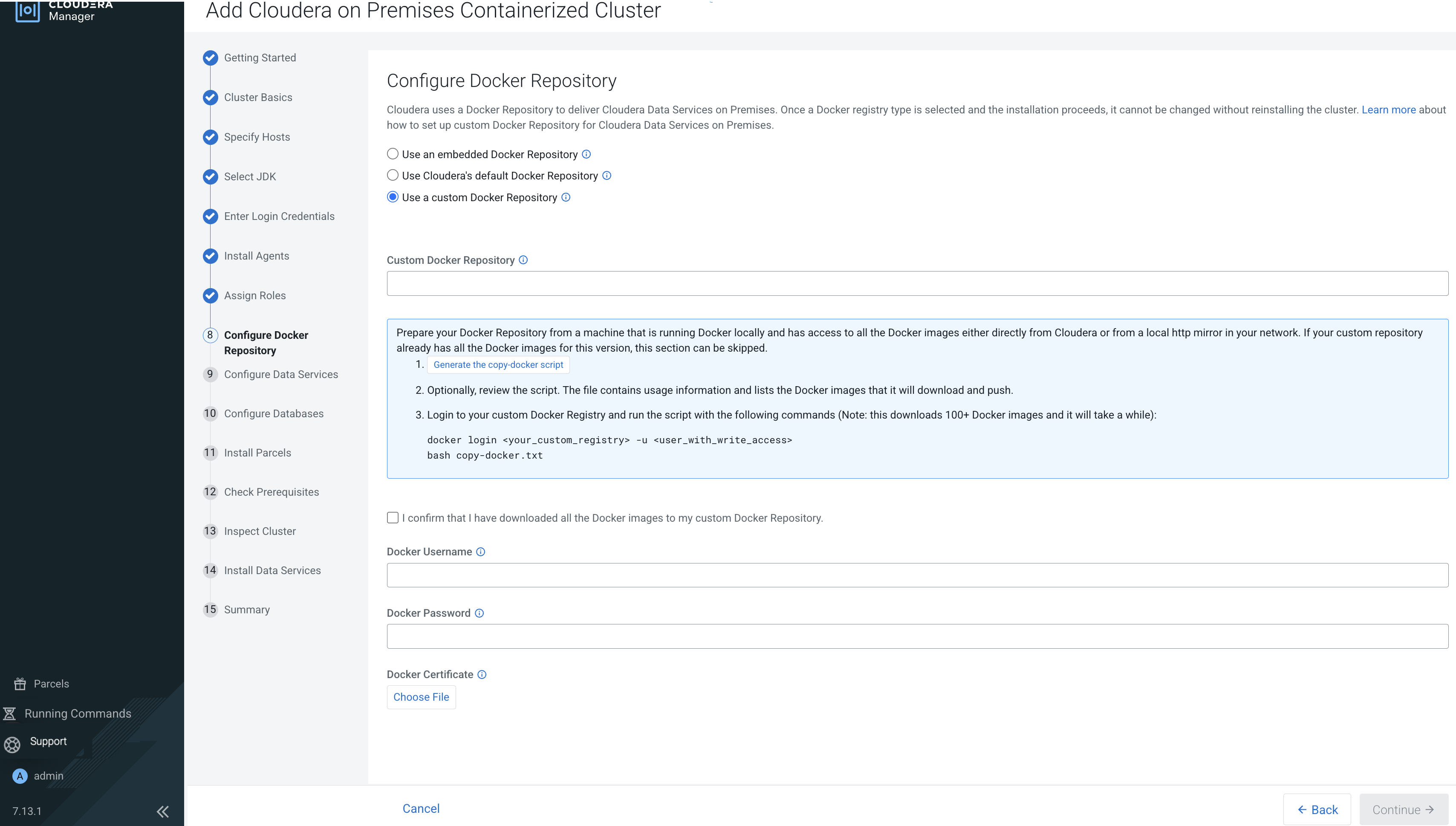
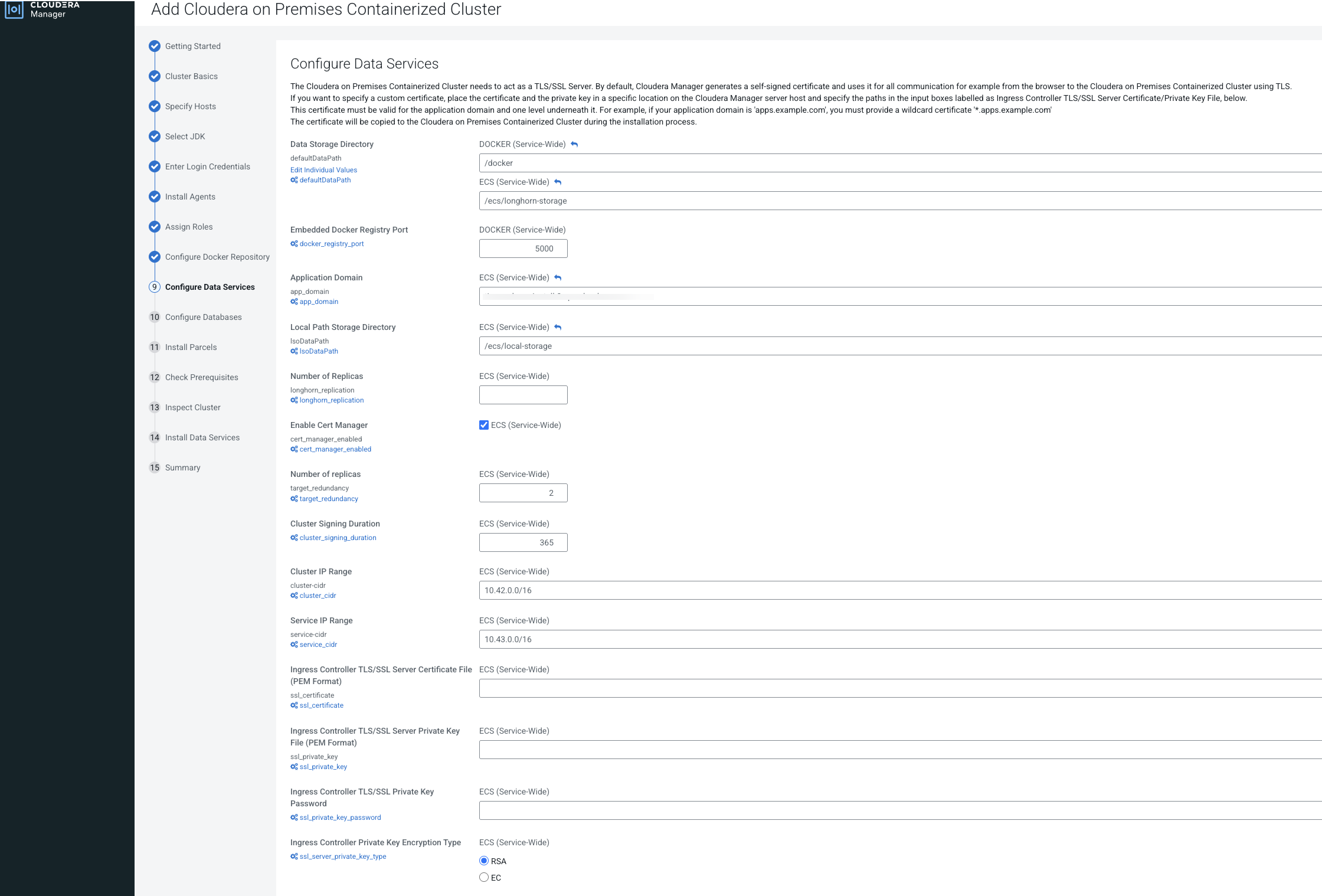
- If you specified a custom certificate, select the Cloudera Embedded Container Service cluster in Cloudera Manager, then select Actions > Update
Ingress Controller. This command copies the
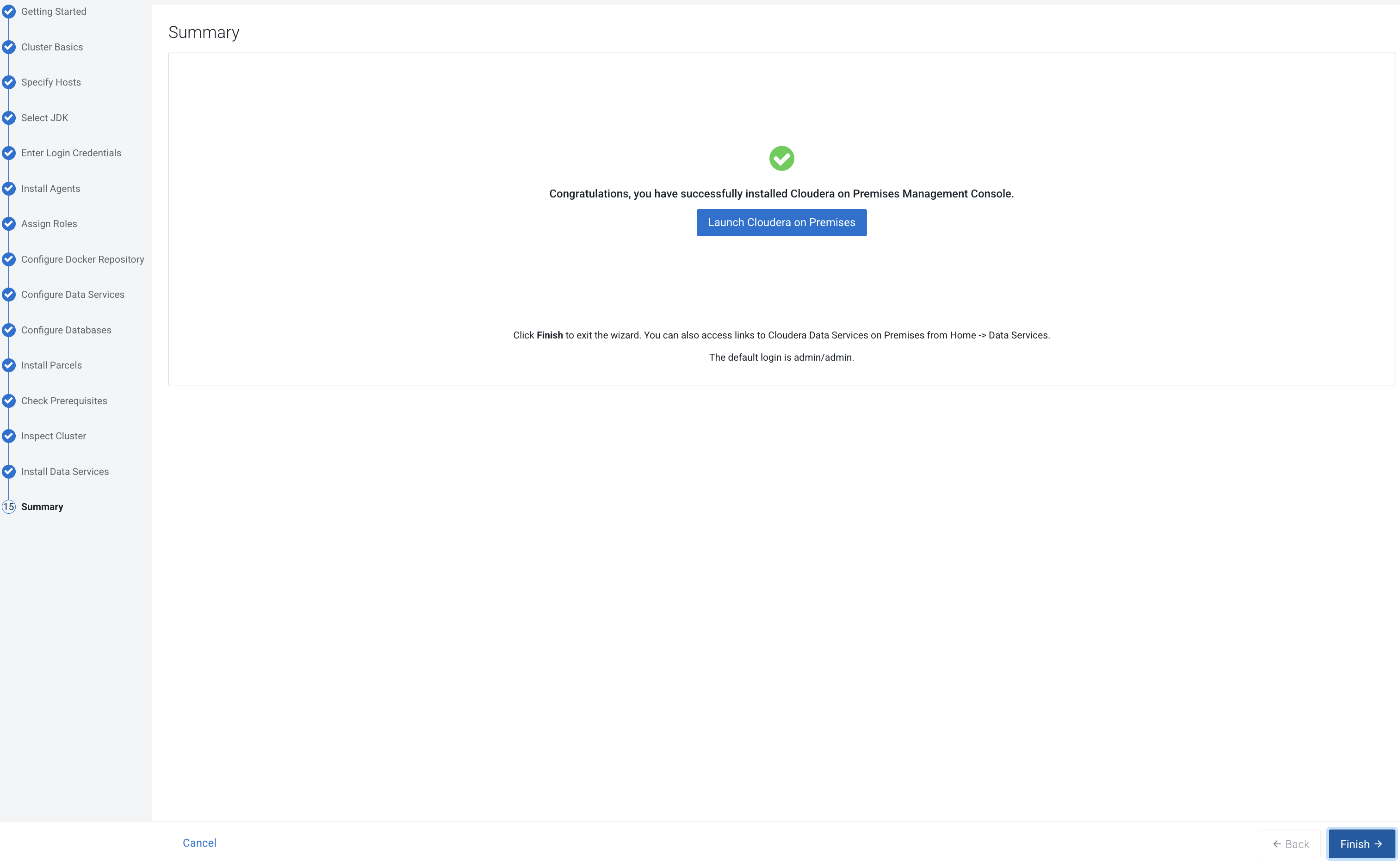
cert.pemandkey.pemfiles from the Cloudera Manager server host to the Cloudera Embedded Container Service Management Console host. - Click Open Cloudera on premises to launch your Cloudera Data Services on premises instance.
- Log in using the default username and password admin.
- On the Welcome to Cloudera on premises page, click Reset Admin Password to change the Local Administrator Account password.
- Set up external authentication using the URL of the LDAP server and a CA certificate of your secure LDAP. Set up external authentication using the URL of the SAML and uplolad SAML Identity Provider Metadata file. Follow the instructions on the Welcome to Cloudera on premises page to complete this step.
- Click Test Connection to ensure that you are able to connect to the configured LDAP server.
- Create your first Virtual Warehouse in the Cloudera Data Warehouse Data Service
- Provision an Cloudera AI Workbench in the Cloudera AI Data Service
- Add a Cloudera Data Engineering service in the Cloudera Data Engineering Data Service