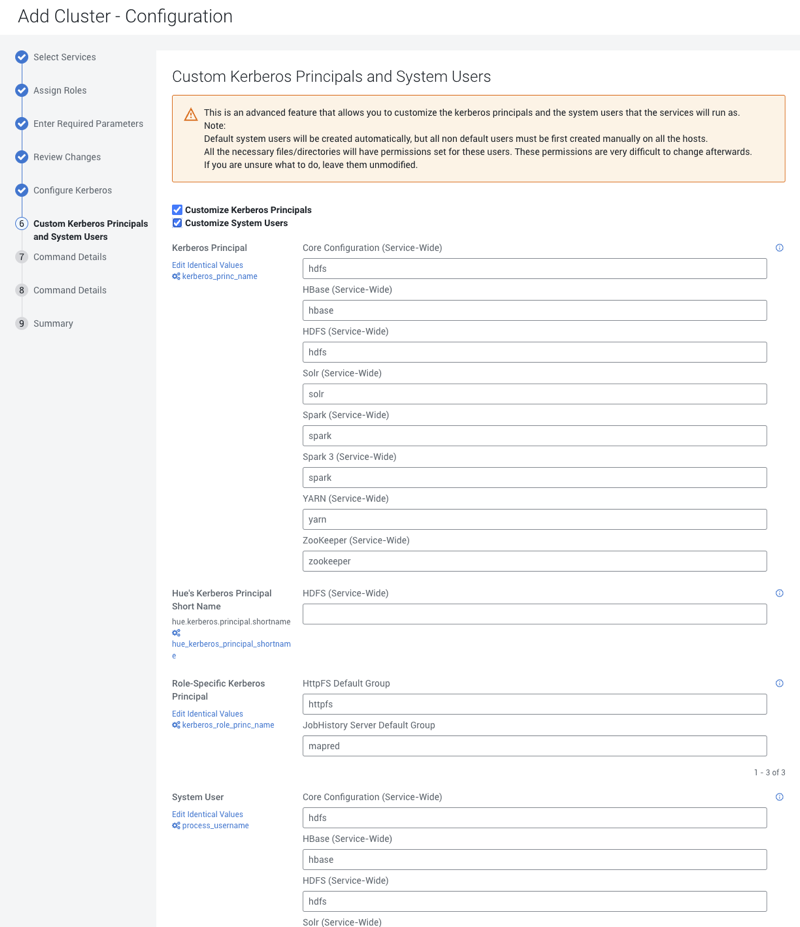
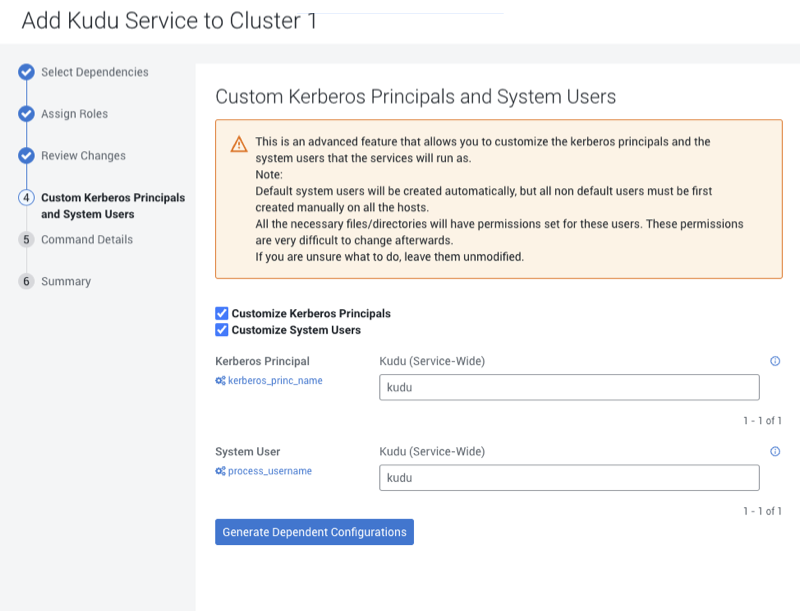
Customizing Kerberos Principals and System Users (Recommended)
The Custom Kerberos Principals and System Users is an advanced feature that allows you to customize the Kerberos Principals and System Users for the Cloudera Runtime services. The following steps explain how to customize the Kerberos Principals and System Users in the Cloudera Manager.
Currently, the supported combination for the new Private Cloud Base clusters is to use an equal name for kerberos principals and system users. Such as, in case of Kudu service, enter the name as “kudu” for both kerberos principal name and system username.
- Service Monitor (role of the Cloudera Management Service): When Hue service is present in the cluster, the principal name for Service Monitor must be equal to the principal name of the Hue service in the cluster.
- Ozone and HDFS: You can customize the principal names for Ozone role types, but the Ozone system username must match the HDFS system username.
- Kafka Mirror Maker: The system user for this role type must match the Kafka service-level system username (default is “kafka”).
- Ranger role types (such as Ranger Admin, Ranger Tagsync, and Ranger Usersync) have a role-specific principal name, but the system user must match the Ranger service-level system username.
Perform the following steps to customize the Kerberos Principals and System Users for the Cloudera Runtime services: