Create the restricted policies and attach them to the Cloudera cross-account role
Update the environment role to use the Cloudera Data Hub and Compute restricted policies. You can do this during the environment-creation process or before you enable the environment.
To enable the Cloudera Data Flow experience after the environment has been created, an Administrator needs to attach the Compute Restricted IAM policy and the Cloudera Data Hub restricted policy with the Cloudera cross-account role associated with the environment.
To use Cloudera Data Flow with the most restrictive options available, you need to create a custom Customer Managed Key (CMK) defining it on Environment level. The Compute Restricted IAM policy provided here requires the existence of such a key. If you want to use Cloudera Data Flow with less restrictive options, you can modify the policy in a way that allows Cloudera to create and manage the key for you.
-
Go to the Environments page.
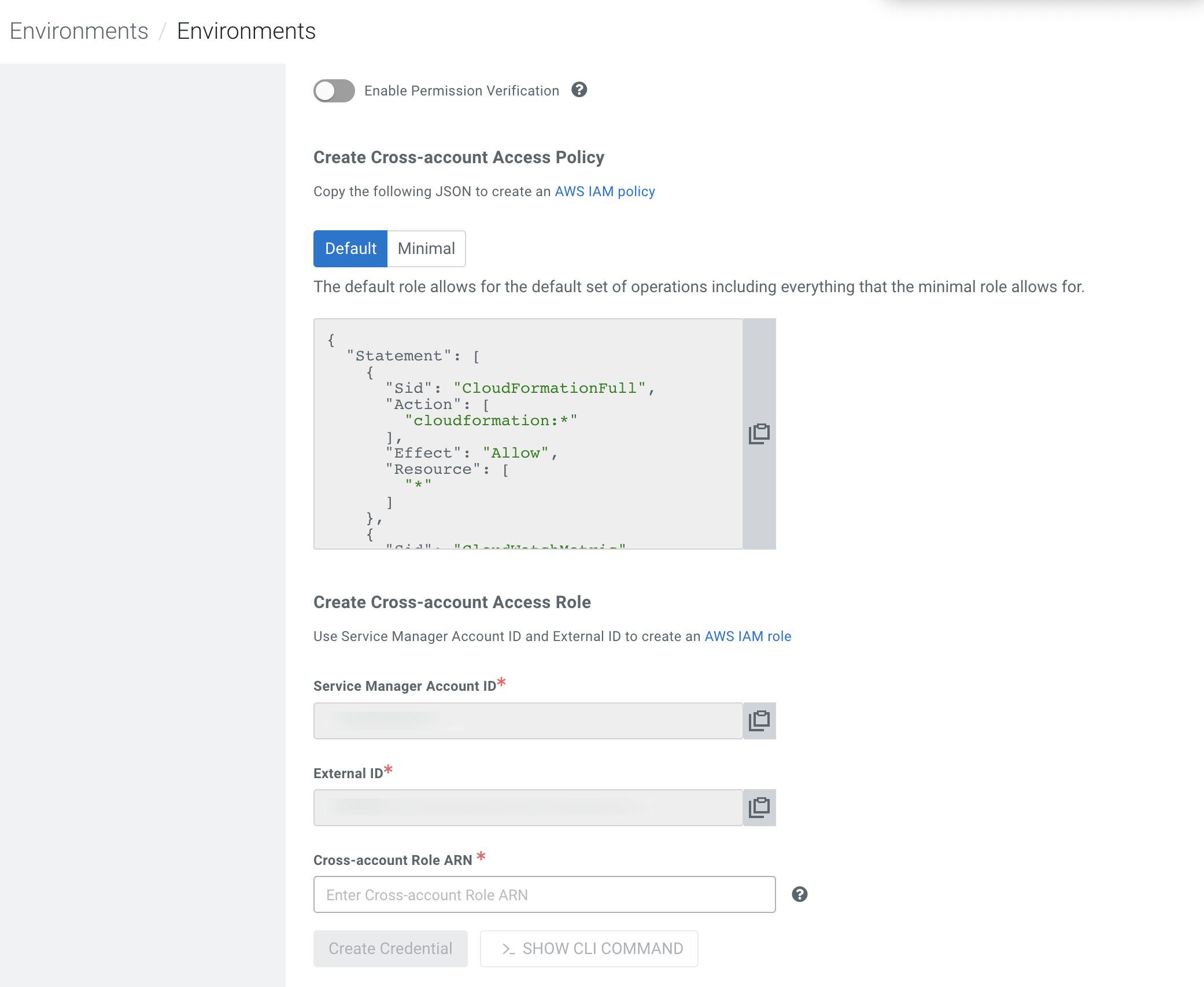
-
In the Create Cross-account Access Policy field, attach the
Compute Restricted IAM policy:
Replace the following placeholders in the JSON file:
- [***YOUR-ACCOUNT-ID***] with your account ID in use.
- [***YOUR-IAM-ROLE-NAME***] with the IAM restricted role associated with this policy.
- [***'YOUR-SUBNET-ARN-*'***] supplied during the Cloudera Environment(s) creation.
- [***YOUR-IDBROKER-ROLE-NAME***] with the ID Broker Role name in use.
- [***YOUR-LOG-ROLE-NAME***] with the Log Role name in use.
- [***YOUR-KMS-CUSTOMER-MANAGED-KEY-ARN***] with KMS key ARN.
{ "Version": "2012-10-17", "Id": "ComputePolicy_v12", "Statement": [ { "Sid": "SimulatePrincipalPolicy", "Effect": "Allow", "Action": [ "iam:SimulatePrincipalPolicy" ], "Resource": [ "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/[***YOUR-IAM-ROLE-NAME***]" ] }, { "Sid": "RestrictedPermissionsViaClouderaRequestTag", "Effect": "Allow", "Action": [ "cloudformation:CreateStack", "cloudformation:CreateChangeSet", "ec2:createTags", "eks:TagResource" ], "Resource": "*", "Condition": { "StringLike": { "aws:RequestTag/Cloudera-Resource-Name": [ "crn:{{ .CRNPartition }}:*" ] } } }, { "Sid": "RestrictedPermissionsViaClouderaResourceTag", "Effect": "Allow", "Action": [ "autoscaling:DeleteTags", "autoscaling:DetachInstances", "autoscaling:ResumeProcesses", "autoscaling:SetDesiredCapacity", "autoscaling:SuspendProcesses", "autoscaling:TerminateInstanceInAutoScalingGroup", "autoscaling:UpdateAutoScalingGroup", "cloudformation:DeleteChangeSet", "cloudformation:DeleteStack", "cloudformation:DescribeChangeSet", "cloudformation:DescribeStacks", "cloudformation:CancelUpdateStack", "cloudformation:ContinueUpdateRollback", "cloudformation:DescribeStackEvents", "cloudformation:DescribeStackResource", "cloudformation:DescribeStackResources", "cloudformation:ExecuteChangeSet", "cloudformation:ListStacks", "cloudwatch:deleteAlarms", "cloudwatch:putMetricAlarm", "ec2:AttachVolume", "ec2:CreateNetworkInterface", "ec2:CreateVolume", "ec2:DeleteVolume", "ec2:RunInstances", "eks:DescribeUpdate", "eks:ListUpdates", "eks:UpdateClusterConfig", "eks:UpdateClusterVersion", "iam:GetRolePolicy", "iam:ListInstanceProfiles", "iam:ListRoleTags", "iam:RemoveRoleFromInstanceProfile", "iam:TagRole", "iam:UntagRole", "logs:DescribeLogStreams", "logs:FilterLogEvents" ], "Resource": "*", "Condition": { "StringLike": { "aws:ResourceTag/Cloudera-Resource-Name": [ "crn:{{ .CRNPartition }}:*" ] } } }, { "Sid": "RestrictedPermissionsViaCloudFormation", "Effect": "Allow", "Action": [ "autoscaling:CreateAutoScalingGroup", "autoscaling:CreateLaunchConfiguration", "autoscaling:CreateOrUpdateTags", "autoscaling:DeleteAutoScalingGroup", "autoscaling:DeleteLaunchConfiguration", "autoscaling:DescribeAutoScalingInstances", "autoscaling:DescribeLaunchConfigurations", "autoscaling:DescribeScalingActivities", "autoscaling:DescribeScheduledActions", "autoscaling:DescribeTags", "dynamodb:DescribeTable", "ec2:AuthorizeSecurityGroupEgress", "ec2:CreateLaunchTemplate", "ec2:CreateSecurityGroup", "ec2:DeleteLaunchTemplate", "ec2:DeletePlacementGroup", "ec2:DeleteSecurityGroup", "ec2:DescribeAccountAttributes", "ec2:DescribeImages", "ec2:DescribeInstanceStatus", "ec2:DescribeInstances", "ec2:DescribeKeyPairs", "ec2:DescribeLaunchTemplateVersions", "ec2:DescribeLaunchTemplates", "ec2:DescribePlacementGroups", "ec2:DescribeRegions", "ec2:DescribeRouteTables", "ec2:DescribeSecurityGroups", "ec2:DescribeVolumes", "ec2:RevokeSecurityGroupEgress", "ec2:RevokeSecurityGroupIngress", "eks:CreateCluster", "eks:DeleteCluster" ], "Resource": "*", "Condition": { "ForAnyValue:StringEquals": { "aws:CalledVia": [ "cloudformation.amazonaws.com" ] } } }, { "Sid": "RestrictedEC2PermissionsViaClouderaResourceTag", "Effect": "Allow", "Action": [ "ec2:RebootInstances", "ec2:StartInstances", "ec2:StopInstances", "ec2:TerminateInstances" ], "Resource": [ "*" ], "Condition": { "ForAnyValue:StringLike": { "ec2:ResourceTag/Cloudera-Resource-Name": [ "crn:{{ .CRNPartition }}:*" ] } } }, { "Sid": "RestrictedIamPermissionsToClouderaResources", "Effect": "Allow", "Action": [ "iam:PassRole" ], "Resource": [ "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/[***YOUR-IDBROKER-ROLE-NAME***]", "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/[***YOUR-LOG-ROLE-NAME***]", "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/liftie-*-eks-service-role", "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/liftie-*-eks-worker-nodes", "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/cdp-eks-master-role", "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/cdp-liftie-instance-profile" ] }, { "Sid": "RestrictedKMSPermissionsUsingCustomerProvidedKey", "Effect": "Allow", "Action": [ "kms:CreateGrant", "kms:DescribeKey", "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*" ], "Resource": [ "[***YOUR-KMS-CUSTOMER-MANAGED-KEY-ARN***]" ] }, { "Sid": "AllowCreateDeleteTagsForSubnets", "Effect": "Allow", "Action": [ "ec2:CreateTags", "ec2:DeleteTags" ], "Resource": [ "arn:{{ .ARNPartition }}:ec2:[***YOUR-SUBNET-REGION***]:[***YOUR-ACCOUNT-ID***]:subnet/*" ] }, { "Sid": "ModifyInstanceAttribute", "Effect": "Allow", "Action": [ "ec2:ModifyInstanceAttribute" ], "Resource": [ "*" ], "Condition": { "StringEquals": { "ec2:Attribute": "SourceDestCheck" } } }, { "Sid": "OtherPermissions", "Effect": "Allow", "Action": [ "autoscaling:DescribeAutoScalingGroups", "ec2:AuthorizeSecurityGroupIngress", "ec2:CreateLaunchTemplateVersion", "ec2:CreatePlacementGroup", "ec2:DeleteKeyPair", "ec2:DeleteNetworkInterface", "ec2:DescribeAvailabilityZones", "ec2:DescribeInstanceTypes", "ec2:DescribeNetworkInterfaces", "ec2:DescribeSubnets", "ec2:DescribeVpcAttribute", "ec2:DescribeVpcs", "ec2:ImportKeyPair", "ec2:UpdateSecurityGroupRuleDescriptionsIngress", "ec2:GetInstanceTypesFromInstanceRequirements", "eks:DescribeCluster", "eks:CreateAccessEntry", "eks:DeleteAccessEntry", "eks:ListAccessEntries", "eks:DescribeAccessEntry", "eks:AssociateAccessPolicy", "eks:DisassociateAccessPolicy", "eks:ListAssociatedAccessPolicies", "elasticloadbalancing:DescribeLoadBalancers", "iam:GetRole", "iam:ListRoles", "iam:GetInstanceProfile" ], "Resource": [ "*" ] }, { "Sid": "AllowSsmParams", "Effect": "Allow", "Action": [ "ssm:DescribeParameters", "ssm:GetParameter", "ssm:GetParameters", "ssm:GetParameterHistory", "ssm:GetParametersByPath" ], "Resource": [ "arn:aws:ssm:*:*:parameter/aws/service/eks/optimized-ami/*" ] }, { "Sid": "CfDeny", "Effect": "Deny", "Action": [ "cloudformation:*" ], "Resource": [ "*" ], "Condition": { "ForAnyValue:StringLike": { "cloudformation:ImportResourceTypes": [ "*" ] } } }, { "Sid": "ForAutoscalingLinkedRole", "Effect": "Allow", "Action": [ "iam:CreateServiceLinkedRole" ], "Resource": [ "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/aws-service-role/autoscaling-plans.amazonaws.com/AWSServiceRoleForAutoScalingPlans_EC2AutoScaling" ], "Condition": { "StringLike": { "iam:AWSServiceName": "autoscaling-plans.amazonaws.com" } } }, { "Sid": "ForEksLinkedRole", "Effect": "Allow", "Action": [ "iam:CreateServiceLinkedRole" ], "Resource": [ "arn:{{ .ARNPartition }}:iam::[***YOUR-ACCOUNT-ID***]:role/aws-service-role/eks.amazonaws.com/AWSServiceRoleForEKS" ], "Condition": { "StringLike": { "iam:AWSServiceName": "eks.amazonaws.com" } } } ] } -
Depending on whether you created a custom Customer Managed Key (CMK) to be used for EBS
encryption or you want Cloudera to generate and
manage the CMK for you, select one of the following options:
- Provide own CMK - if you want to use your own custom CMK
- Let Cloudera generate CMK - if you want to allow Cloudera to generate and manage your CMK
- If you have not already created it, create a custom CMK. Verify that the policy
(this is different from the IAM policy) for CMK at KMS has the required additional
permissions blocks defined.
For more information, see Using CMKs with Cloudera Data Flow.
- Provide the KMS CMK for volume encryption in the policy section with
Sid:RestrictedKMSPermissionsUsingCustomerProvidedKey.
Replace theRestrictedKMSPermissionsUsingCustomerProvidedKeypolicy section with the following:{ "Sid": "AllCreateAndManageKMS", "Effect": "Allow", "Action": [ "kms:Create*", "kms:Describe*", "kms:Enable*", "kms:List*", "kms:Put*", "kms:Update*", "kms:Revoke*", "kms:Disable*", "kms:Get*", "kms:Delete*", "kms:ScheduleKeyDeletion", "kms:CancelKeyDeletion" ], "Resource": "*" } - In the Create Cross-account Access Role section, associate the cross-account access role with the Compute Restricted IAM policy.
- Click Create Credential.
-
Repeat the steps to add the Data Hub restricted policy.
Copy the following Cloudera Data Hub restricted policy in the Create Cross-account Access Policy field:Replace the following placeholders in the JSON file:
- [YOUR-ACCOUNT-ID] with your account ID in use.
- [YOUR-IDBROKER-ROLE-NAME] with your IDBroker role name.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "ec2:DeleteTags", "ec2:AssociateAddress", "ec2:StartInstances", "ec2:StopInstances", "ec2:AttachVolume", "ec2:DescribeAddresses", "ec2:TerminateInstances", "ec2:DeleteSecurityGroup" ], "Resource": "*", "Condition": { "StringLike": { "ec2:ResourceTag/Cloudera-Resource-Name": [ "crn:cdp:*" ] } } }, { "Effect": "Allow", "Action": [ "cloudformation:DeleteStack", "autoscaling:SuspendProcesses", "autoscaling:UpdateAutoScalingGroup", "autoscaling:ResumeProcesses", "autoscaling:DetachInstances", "autoscaling:DeleteAutoScalingGroup", "rds:StopDBInstance", "rds:StartDBInstance" ], "Resource": "*", "Condition": { "StringLike": { "aws:ResourceTag/Cloudera-Resource-Name": [ "crn:cdp:*" ] } } }, { "Effect": "Allow", "Action": [ "cloudformation:CreateStack", "cloudformation:GetTemplate", "ec2:CreateTags" ], "Resource": [ "*" ], "Condition": { "StringLike": { "aws:RequestTag/Cloudera-Resource-Name": [ "crn:cdp:*" ] } } }, { "Effect": "Allow", "Action": [ "ec2:DeleteVolume", "ec2:CreateSecurityGroup", "ec2:DeleteKeyPair", "ec2:DescribeKeyPairs", "ec2:DescribeAvailabilityZones", "ec2:DescribeImages", "ec2:DeleteLaunchTemplate", "ec2:DescribeVolumes", "ec2:CreateVolume", "ec2:DescribeInstances", "ec2:DescribeRegions", "ec2:DescribeInstanceTypeOfferings", "ec2:DescribeInstanceTypes", "ec2:DescribeRouteTables", "ec2:DescribeSecurityGroups", "ec2:DescribeSubnets", "ec2:DescribeVpcAttribute", "ec2:DescribeVpcs", "ec2:DescribeInternetGateways", "ec2:DescribeVpcEndpoints", "ec2:describeAddresses", "ec2:DescribeNatGateways", "ec2:DescribeVpcEndpointServices", "ec2:ModifySubnetAttribute", "ec2:ModifyVpcAttribute", "ec2:CreatePlacementGroup", "ec2:DescribePlacementGroups", "ec2:ImportKeyPair", "ec2:DescribeLaunchTemplates", "ec2:CreateLaunchTemplate", "ec2:RunInstances", "ec2:DescribeAccountAttributes", "sts:DecodeAuthorizationMessage", "cloudformation:DescribeStacks", "dynamodb:DeleteTable", "dynamodb:DescribeTable", "iam:ListInstanceProfiles", "iam:ListRoles", "dynamodb:ListTables", "autoscaling:DescribeAutoScalingGroups", "autoscaling:DescribeScalingActivities", "autoscaling:CreateAutoScalingGroup", "autoscaling:TerminateInstanceInAutoScalingGroup", "cloudwatch:DeleteAlarms", "cloudwatch:PutMetricAlarm", "cloudwatch:DescribeAlarms", "elasticloadbalancing:CreateLoadBalancer", "elasticloadbalancing:CreateTargetGroup", "elasticloadbalancing:DescribeLoadBalancers", "elasticloadbalancing:DescribeTargetGroups", "elasticloadbalancing:AddTags", "elasticloadbalancing:RegisterTargets", "elasticloadbalancing:DescribeTargetHealth", "elasticloadbalancing:DescribeListeners", "elasticloadbalancing:CreateListener", "elasticloadbalancing:DeleteListener", "elasticloadbalancing:DeleteTargetGroup", "elasticloadbalancing:DeleteLoadBalancer", "elasticloadbalancing:DeregisterTargets", "s3:GetBucketLocation", "cloudformation:DescribeStackEvents", "cloudformation:DescribeStackResources", "cloudformation:DescribeStackResource", "cloudformation:ListStackResources", "cloudformation:UpdateStack", "cloudformation:GetTemplate", "iam:GetInstanceProfile", "iam:SimulatePrincipalPolicy", "iam:GetRole", "rds:AddTagsToResource", "rds:CreateDBInstance", "rds:CreateDBSubnetGroup", "rds:DeleteDBInstance", "rds:DeleteDBSubnetGroup", "rds:ListTagsForResource", "rds:RemoveTagsFromResource", "rds:CreateDBParameterGroup", "rds:DeleteDBParameterGroup", "rds:DescribeEngineDefaultParameters", "rds:ModifyDBParameterGroup", "rds:DescribeDBParameters", "rds:DescribeDBParameterGroups", "rds:DescribeDBSubnetGroups", "rds:DescribeDBInstances", "rds:ModifyDBInstance", "rds:DescribeCertificates", "kms:ListKeys", "kms:ListAliases", "ec2:ModifyInstanceAttribute", "ec2:CreateLaunchTemplateVersion" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "iam:PassRole" ], "Resource": [ "arn:aws:iam::[***YOUR-ACCOUNT-ID***]:role/[***YOUR-IDBROKER-ROLE-NAME***]" ] }, { "Sid": "IdentityAccessManagementLimited", "Action": [ "iam:CreateServiceLinkedRole" ], "Effect": "Allow", "Resource": [ "arn:aws:iam::*:role/aws-service-role/*" ] } ] }
