Declaring Knox topologies
Learn how to create the Knox topologies to define for Knox how to proxy requests from external users.
Ensure that you have the following information before performing the steps:
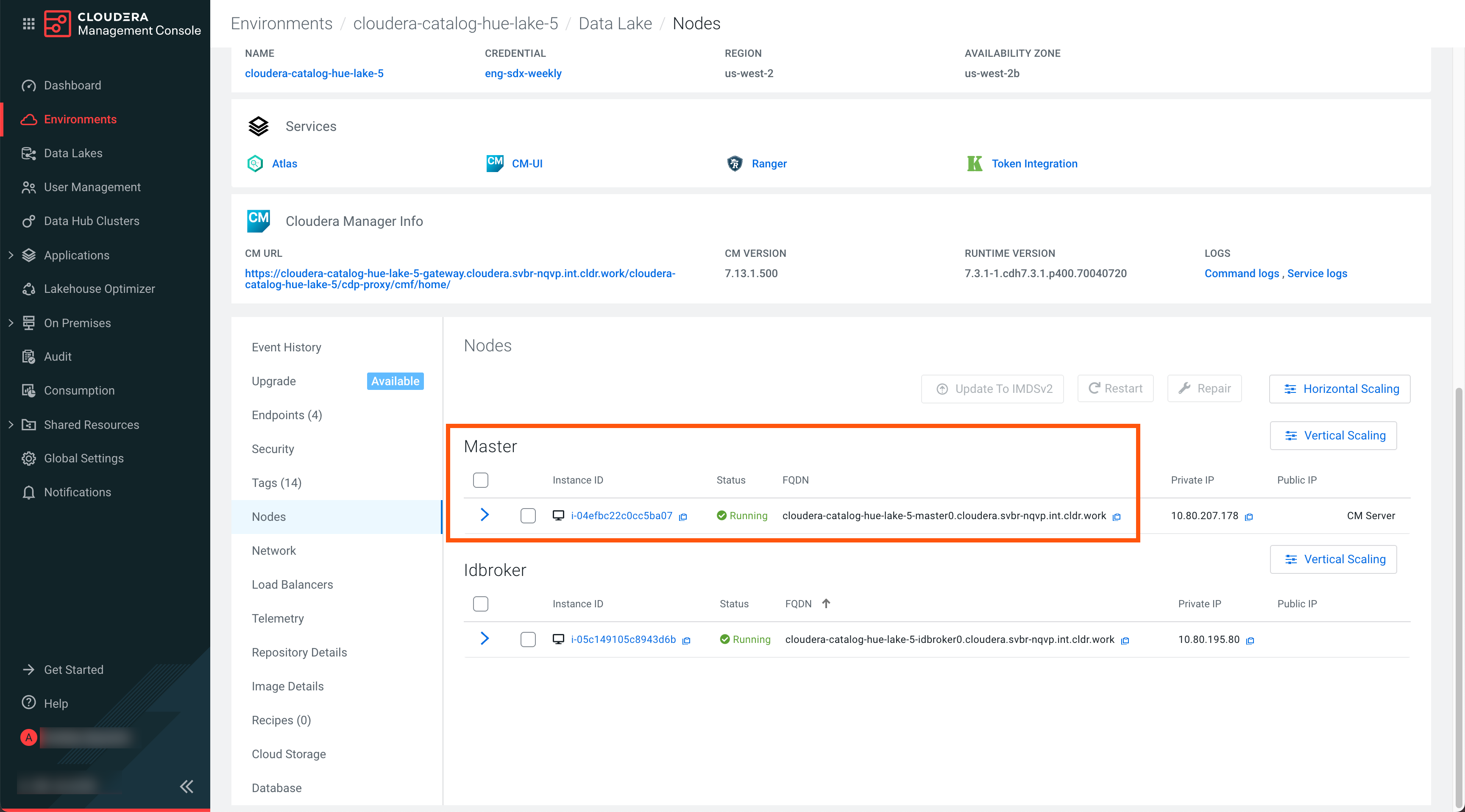
- HMS Host and Ranger Host: To get the HMS Host and Ranger Admin Host, go to Data Lake > Nodes, and copy the FQDN of the Master node.
- Username of the user who will generate the
CLIENT_IDandCLIENT_SECRET.
- Go to Cloudera Manager > Knox > Configuration.
- Select the Knox Gateway scope.
-
Search for and edit the Knox Gateway Advanced Configuration Snippet
(Safety Valve) for conf/cdp-resources.xml property, and add the
following after clicking View as XML:
<property> <name>providerConfigs:cdp-share-access-providers</name> <value>role=federation#federation.name=JWTProvider#federation.enabled=true#federation.param.knox.token.exp.server-managed=true#role=identity-assertion#identity-assertion.name=Default#identity-assertion.enabled=true#identity-assertion.param.group.mapping.$PRIMARY_GROUP=(not(member username))</value> </property> <property> <name>cdp-share-access</name> <value>providerConfigRef=cdp-share-access-providers#KNOXTOKEN:knox.token.ttl=36000000#KNOXTOKEN:knox.token.exp.server-managed=true#HMS-API:url=http://***DATA LAKE MASTER NODE FQDN***:8090#KNOXTOKEN:gateway.knox.token.limit.per.user=-1#identity-assertion.param.hadoop.proxyuser.***USERNAME***.users=#identity-assertion.param.hadoop.proxyuser.***USERNAME***.groups=#identity-assertion.param.hadoop.proxyuser.***USERNAME***.hosts=*</value> </property> <property> <name>providerConfigs:cdp-share-management-providers</name> <value>role=authentication#authentication.name=ShiroProvider#authentication.param.main.invalidRequest=org.apache.shiro.web.filter.InvalidRequestFilter#authentication.param.main.invalidRequest.blockBackslash=false#authentication.param.main.invalidRequest.blockNonAscii=false#authentication.param.main.invalidRequest.blockSemicolon=false#authentication.param.main.pamRealm=org.apache.knox.gateway.shirorealm.KnoxPamRealm#authentication.param.main.knoxAnonFilter=org.apache.knox.gateway.filter.AnonymousAuthFilter#authentication.param.urls./knoxtoken/api/v1/jwks.json=knoxAnonFilter#authentication.param.main.pamRealm.service=login#authentication.param.sessionTimeout=30#authentication.param.urls./**=authcBasic#role=identity-assertion#identity-assertion.name=HadoopGroupProvider#identity-assertion.param.hadoop.proxyuser.impersonation.enabled=true#identity-assertion.param.hadoop.proxyuser.***USERNAME***.users=*#identity-assertion.param.hadoop.proxyuser.***USERNAME***.groups=*#identity-assertion.param.hadoop.proxyuser.***USERNAME***.hosts=*#identity-assertion.param.CENTRAL_GROUP_CONFIG_PREFIX=gateway.group.config.#role=authorization#authorization.name=XASecurePDPKnox#authorization.enabled=false#role=ha#ha.name=HaProvider#ha.enabled=true#ha.param.RANGER=enableStickySession=false;noFallback=false;enableLoadBalancing=true</value> </property> <property> <name>cdp-share-management</name> <value>providerConfigRef=cdp-share-management-providers#RANGER:url=https://***DATA LAKE MASTER NODE FQDN***:6182#KNOXTOKEN:knox.token.ttl=-1#KNOXTOKEN:knox.token.type=JWT#KNOXTOKEN:knox.token.target.url=cdp-proxy-token#KNOXTOKEN:knox.token.audiences=cdp-proxy-token#KNOXTOKEN:knox.token.client.data=homepage_url=homepage/home?profile=token&amp;topologies=cdp-proxy-token#KNOXTOKEN:knox.token.exp.tokengen.allowed.tss.backends=JDBCTokenStateService,AliasBasedTokenStateService#KNOXTOKEN:knox.token.lifespan.input.enabled=true#KNOXTOKEN:knox.token.user.limit.exceeded.action=RETURN_ERROR#KNOXTOKEN:knox.token.exp.server-managed=true</value> </property>Figure 1. Knox topology parameters in the configuration editor after pasting as XML 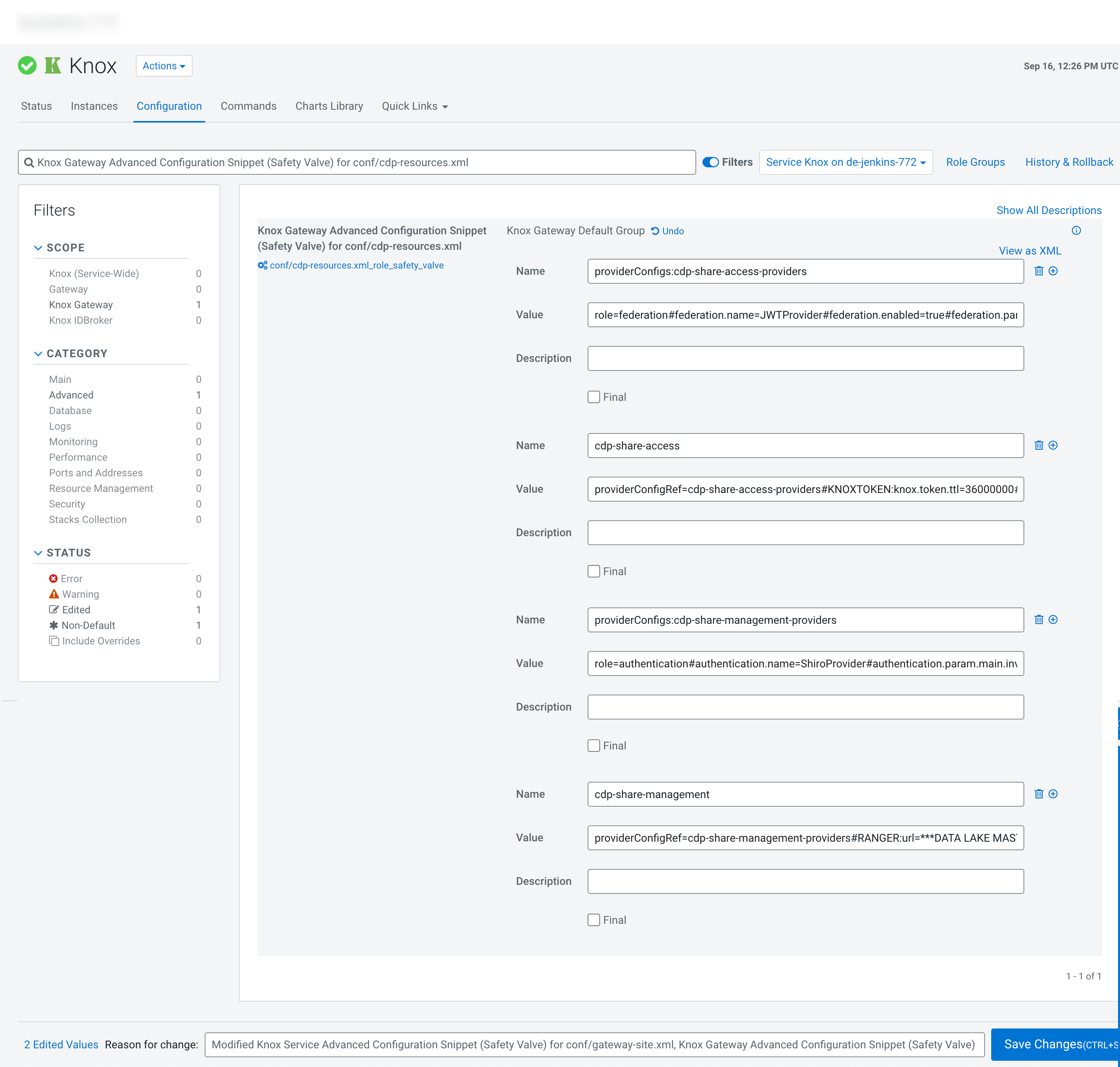
#identity-assertion.param.hadoop.proxyuser.***USERNAME***.users=*#identity-assertion.param.hadoop.proxyuser.***USERNAME***.groups=*#identity-assertion.param.hadoop.proxyuser.***USERNAME***.hosts=*The relevant Knox topologies are created.
-
Click Save Changes and refresh the configuration as
needed.