Create CloudbreakRole
If using role-based authentication, perform these steps to create the CloudbreakRole.
Use the following AssumeRole policy definition:
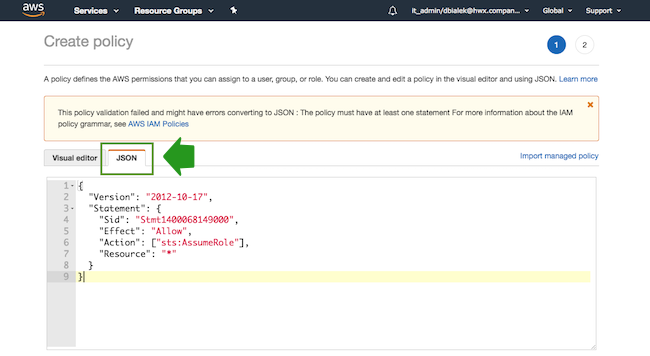
{
"Version": "2012-10-17",
"Statement": {
"Sid": "Stmt1400068149000",
"Effect": "Allow",
"Action": ["sts:AssumeRole"],
"Resource": "*"
}
}Steps
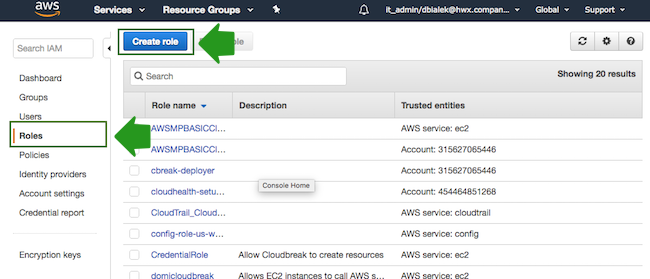
- Navigate to the IAM console > Roles and click Create Role:
- In the “Create Role” wizard, select AWS service role type and then select any service:
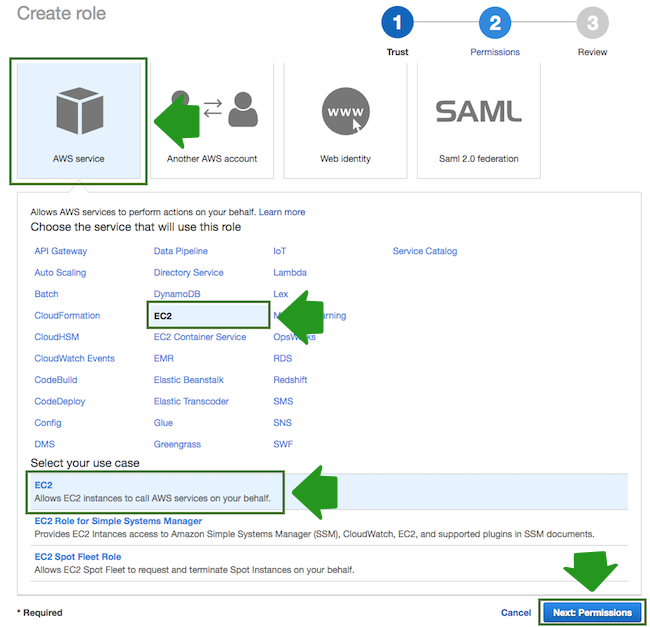
- When done, click Next: Permissions to navigate to the next page in the wizard.
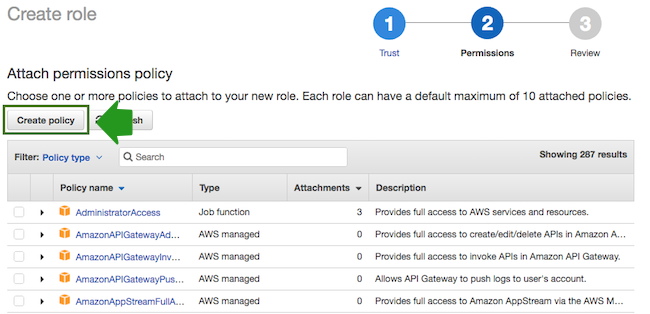
- Click Create policy and the create policy wizard will open in a new browser tab:
- Select the JSON view, and then copy and paste the policy definition. You can
either copy it from the section preceding these steps or download and copy it from here.
 .
.
- When done, navigate to Review policy.
- On the Review policy page, in the Name field, enter a name for your
policy, such as “AssumeRole”:
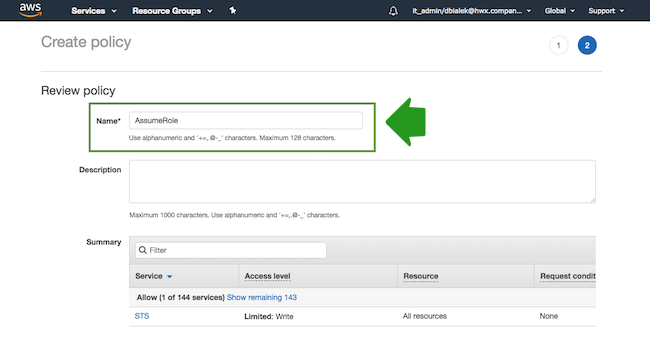
- When done, click Create Policy.
- Return to the previous browser tab where you started creating a new role (since the create policy wizard was opened in a new browser tab).
- Click Refresh. Next, find the policy that you just created and select it by
checking the box:
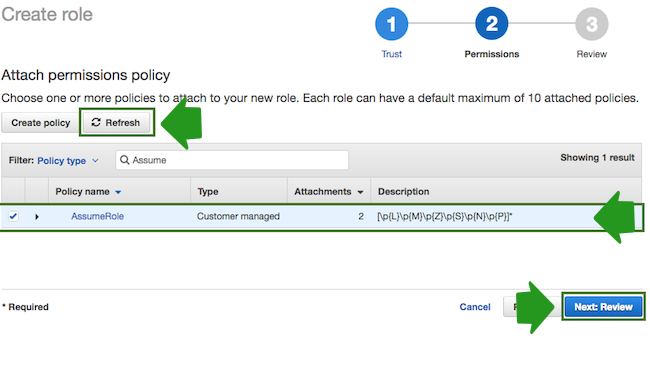
- When done, click Next: Review.
- In the Roles name field, enter role name, for example “CloudbreakRole”:
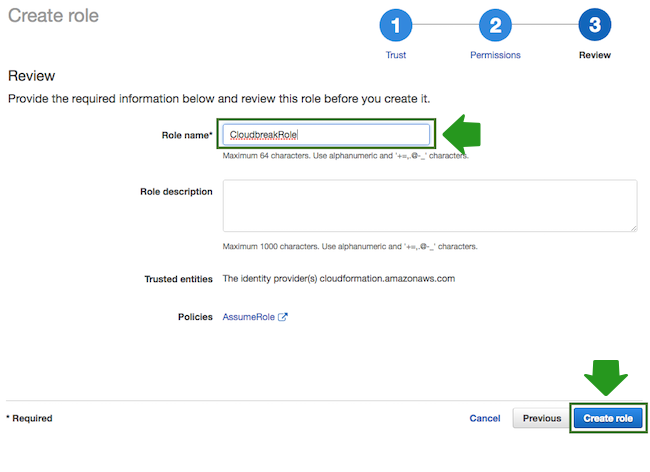
- When done, click Create role to finish the role creation process.
As an outcome of this step, the CloudbreakRole should be created in your IAM console on AWS.

