Performing Threat Triage
To create a threat triage rule configuration, you must first define your rules. These rules identify the conditions in the data source data flow and associate alert scores with those conditions. Following are some examples:
![[Important]](../common/images/admon/important.png) | Important |
|---|---|
In order to apply rules to a sensor, the sensor json file must contain
|
- Rule 1
If a threat intelligence enrichment type is alerted, imagine that you want to receive an alert score of 5.
- Rule 2
If the URL ends with neither .com nor .net, then imagine that you want to receive an alert score of 10.
To create these rules, complete the following steps:
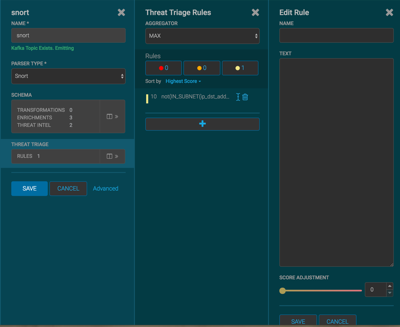
Click the
 (edit button) for your sensor.
(edit button) for your sensor.In the Threat Triage field, click the
 icon (expand window).
icon (expand window).The module displays the Threat Triage Rules panel.
Click the button to add a rule.
The module displays the Edit Rule panel.
Assign a name to the new rule by entering the name in the NAME field.
In the Text field, enter the syntax for the new rule.
For example:
EXISTS(is_alert)
Use the SCORE ADJUSTMENT slider to choose the threat score for the rule.
Click to save the new rule.
The new rule is listed in the Threat Triage Rules panel.
Choose how you want to aggregate your rules by choosing a value from the Aggregator menu.
You can choose between:
- MAX
The maximum of all of the associated values for matching queries.
- MIN
The minimum of all of the associated values for matching queries.
- MEAN
the mean of all of the associated values for matching queries.
- POSITIVE_MEAN
The mean of the positive associated values for the matching queries.
You can use the Rules section and the Sort by pull down menu below the Rules section to filter how threat triages display.
For example, to display only high levels alerts, click the box containing the red indicator. To sort the high level alerts from highest to lowest, choose Highest Score from the Sort by pull down menu.
Click SAVE on the Sensor panel to save your changes.