Configuring Ranger Admin
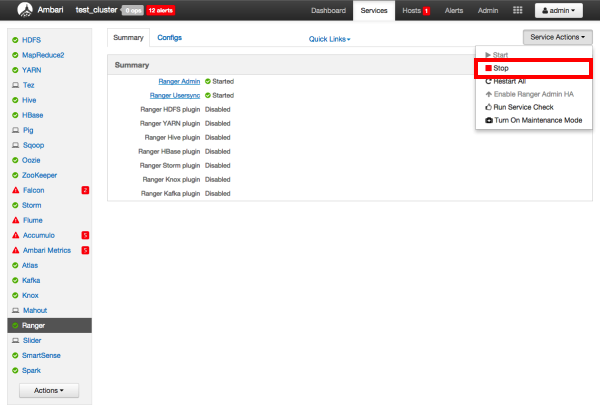
Stop Ranger by selecting Service Actions > Stop.
Use the following CLI commands to change to the Ranger Admin directory and create a self-signed certificate.
cd /etc/ranger/admin/conf keytool -genkey -keyalg RSA -alias rangeradmin -keystore ranger-admin-keystore.jks -storepass xasecure -validity 360 -keysize 2048 chown ranger:ranger ranger-admin-keystore.jks chmod 400 ranger-admin-keystore.jks
When prompted, provide the host name as the value for the "What is your first and last name?" question. then provide answers to the subsequent questions to create the keystore.
![[Note]](../common/images/admon/note.png)
Note When prompted for your password, press the Enter key. This will not work for Java keytool version 1.5.
Use the following steps to disable the HTTP port and enable the HTTPS port with the required keystore information.
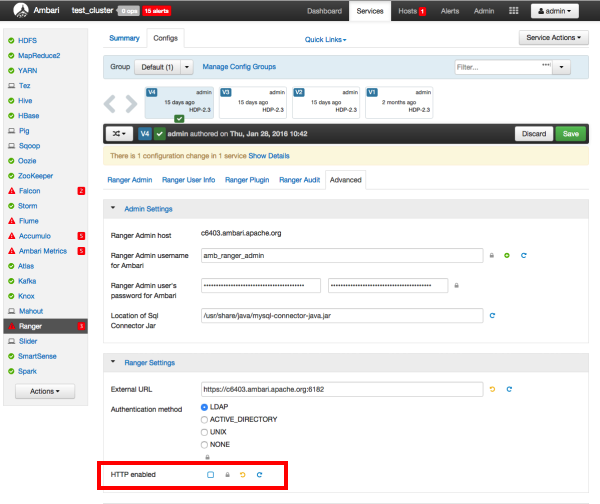
Select Configs > Advanced. Under Ranger Settings, clear the HTTP enabled check box (this blocks all agent calls to the HTTP port even if the port is up and working).
Under Ranger Settings, provide the value in the External URL box in the format
https://<hostname of policy manager>:<https port>.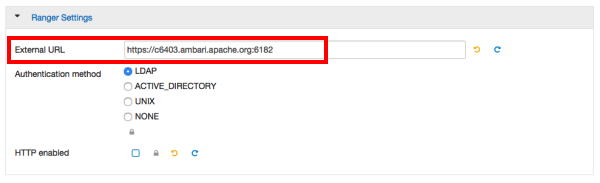
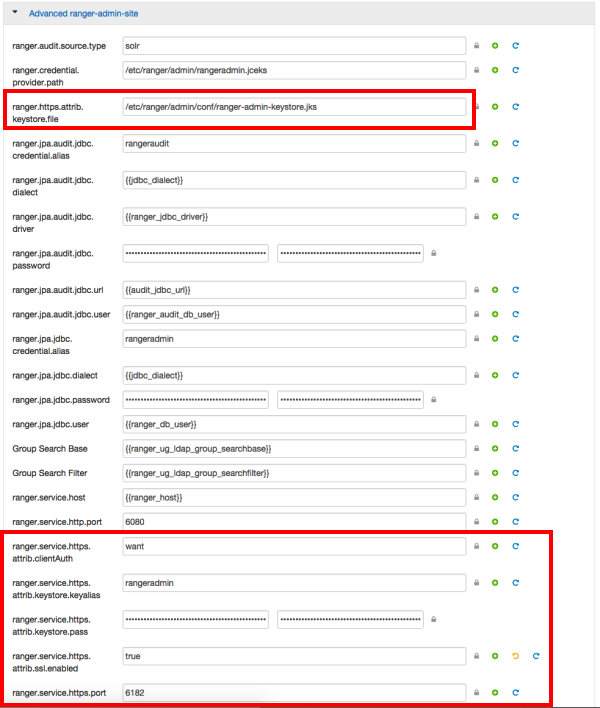
Under Advanced ranger-admin-site, set the following properties:
ranger.https.attrib.keystore.file-- Provide the location of the keystore file created previously:/etc/ranger/admin/conf/ranger-admin-keystore.jks.ranger.service.https.attrib.keystore.pass-- Enter the password for the keystore (in this case,xasecure).ranger.service.https.attrib.keystore.keyalias-- Enter the alias name for the keystore private key (in this case,rangeradmin).ranger.service.https.attrib.clientAuth-- Enterwantas the value. This validates the client cert from all agents, but not the requests from web applications. Setting this value towantrequires the client to have a certificate to use to sign traffic. If you do not want to put certificates on the client machines to do two-way SSL, this parameter can be set tofalseto enable one-way SSL.ranger.service.https.attrib.ssl.enabled-- set this property totrue.ranger.service.https.port-- Make sure that this port is available, or change the value to an available port number.
Under Custom ranger-admin-site, add the following properties:
ranger.service.https.attrib.keystore.file-- Specify the same value provided for theranger.https.attrib.keystore.fileproperty.ranger.service.https.attrib.client.auth-- Specify the same value provided for theranger.service.https.attrib.clientAuthproperty.
To add a Custom ranger-admin-site property:
Select Custom ranger-admin-site, then click Add Property.
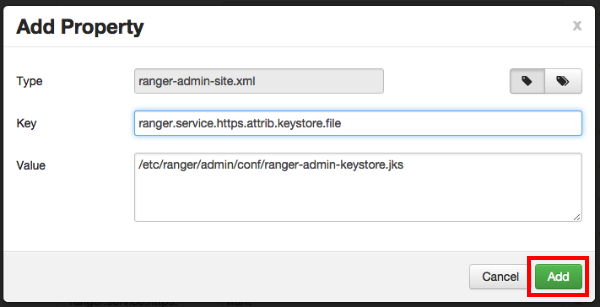
On the Add Property pop-up, type the property name in the Key box, type the property value in the Value box, then click Add.
Save your changes and start Ranger Admin.
When you attempt to access the Ranger Admin UI with the HTTPS protocol on the port specified by the ranger.service.https.port property, the browser should report that it does not trust the site. Click Proceed anyway and you should be able to access the Ranger Admin UI over HTTPS.