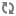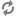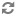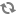Adding Tag-based Policies
Tag-based policies enable you to control access to resources across multiple Hadoop components without creating separate services and policies in each component. You can also use Ranger TagSync to synchronize the Ranger tag store with an external metadata service such as Apache Atlas.
To add a new tag-based policy:
Select Access Manager > Tag Based Policies, then select a tag-based service.
On the List of Policies page, click Add New Policy.
The Create Policy page appears:
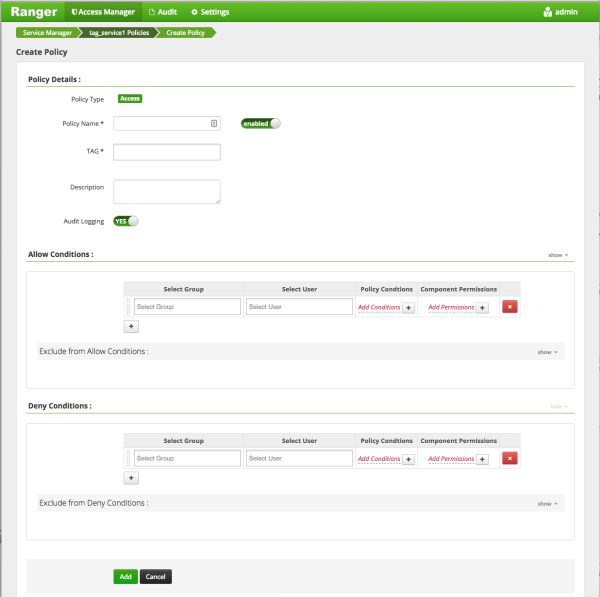
Enter information on the Create Policy page as follows:
Table 3.65. Policy Details
Field Description Policy Type Set to Access by default. Policy Name Enter an appropriate policy name. This name cannot be duplicated across the system. This field is mandatory. TAG Enter the applicable tag name. Description (Optional) Describe the purpose of the policy. Audit Logging Specify whether this policy is audited. (De-select to disable auditing). Table 3.66. Allow, Exclude from Allow, Deny, and Exclude from Deny Conditions
Label
Description
Select Group Specify the group to which this policy applies. To designate the group as an Administrator for the chosen resource, specify Admin permissions. (Administrators can create child policies based on existing policies).
The public group contains all users, so setting a condition for the public group applies to all users.
Select User Specify a particular user to which this policy applies (outside of an already-specified group) OR designate a particular user as Admin for this policy. (Administrators can create child policies based on existing policies). Policy Conditions Click Add Conditions to add or edit policy conditions. Currently "Accessed after expiry_date? (yes/no)" is the only available policy condition. To set this condition, type yes in the text box, then select the green check mark button to add the condition.
Component Permissions Click Add Permissions to add or edit component conditions. To add component permissions, enter the component name in the text box, then use the check boxes to specify component permissions. Select the green check mark button to add the chosen component conditions to the policy. If Deny Conditions does not appear on your Policy Details page, you must first Enable Deny Conditions for Policies.
You can use the Plus (+) symbols to add additional conditions. Conditions are evaluated in the order listed in the policy. The condition at the top of the list is applied first, then the second, then the third, and so on.
Click Add to add the new policy.
Adding a Tag-based PII Policy
In this example we create a tag-based policy for objects tagged "PII" in Atlas. Access to objects tagged "PII" is allowed for members of the "audit" group. All other users (the "public" group) are denied access.
To add a PII tag-based policy:
Select Access Manager > Tag Based Policies, then select a tag-based service.

On the List of Policies page, click Add New Policy.

The Create Policy page appears:

Enter the following information on the Create Policy page:
Table 3.67. Policy Details
Field Description Policy Type Set to Access by default. Policy Name PII TAG PII Audit Logging YES Description Restrict access to resources with the PII tag. Table 3.68. Allow Conditions
Label
Description
Select Group audit
Select User <none> Policy Conditions <none> Component Permissions hive
(select all permissions)
Table 3.69. Deny Conditions
Label
Description
Select Group public
Select User <none> Policy Conditions <none> Component Permissions hive
(select all permissions)
If Deny Conditions does not appear on your Policy Details page, you must first Enable Deny Conditions for Policies.
Table 3.70. Exclude from Allow Conditions
Label
Description
Select Group audit
Select User <none> Policy Conditions <none> Component Permissions hive
(select all permissions)
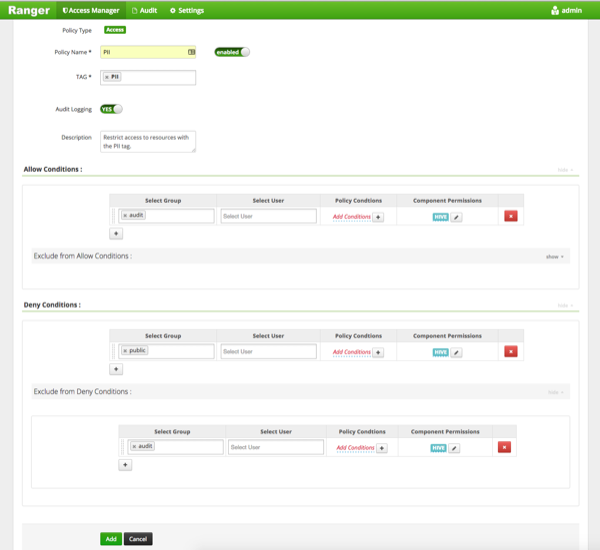
In this example we used Allow Conditions to grant access to the "audit" group, and then used Deny Conditions to deny access to the "public" group. Because the "public" group includes all users, we then used Exclude from Deny Conditions to exclude the "audit" group, in effect reinstating the "audit" group's original Allow access condition.
Click Add to add the new policy.
Default EXPIRES_ON Policy
An EXPIRES_ON tag-based policy is created automatically when a tag service instance created. This default policy denies access to objects tagged with EXPIRES_ON after the expiry date specified in the Atlas tag attribute. You can use the following steps to review the default EXPIRES_ON policy.
Select Access Manager > Tag Based Policies, then select a tag-based service.

On the List of Policies page, click the Edit icon for the default EXIRES_ON policy.
The Edit Policy page appears:
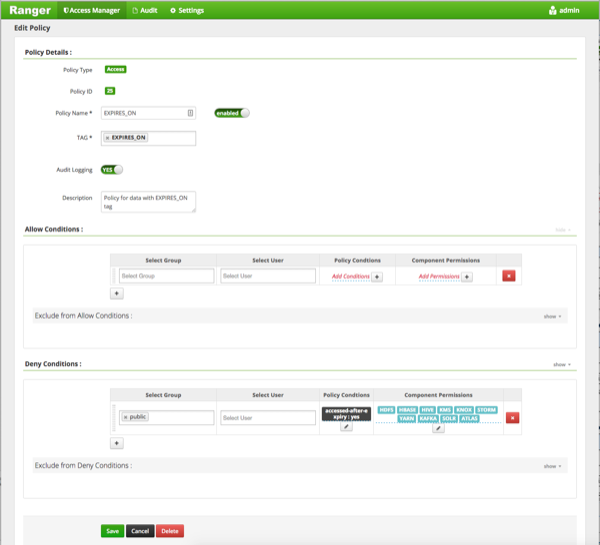
We can see that the default EXPIRES_ON policy denies access to all users, and for all components, after the expiry date specified in the Atlas tag attribute.