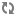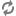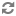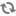Suppose there is a need to immediately block access to an entire sub-tree for a specific user. Applying a named user ACL entry to the root of that sub-tree is the fastest way to accomplish this without accidentally revoking permissions for other users.
Add an ACL entry to block all access to "monthly-sales-data" by user Diana:
> hdfs dfs -setfacl -m user:diana:--- /monthly-sales-data
Run
getfaclto check the results:> hdfs dfs -getfacl /monthly-sales-data # file: /monthly-sales-data # owner: bruce # group: sales user::rwx user:diana:--- group::r-x mask::r-x other::--- default:user::rwx default:group::r-x default:group:execs:r-x default:mask::r-x default:other::---
The new ACL entry is added to the existing permissions defined by the Permission Bits. Bruce has full control as the file owner. Members of either the "sales" group or the "execs" group have Read access. All others do not have access.
It is important to keep in mind the order of evaluation for ACL entries when a user attempts to access a file system object:
If the user is the file owner, the Owner Permission Bits are enforced.
Else, if the user has a named user ACL entry, those permissions are enforced.
Else, if the user is a member of the file’s group or any named group in an ACL entry, then the union of permissions for all matching entries are enforced. (The user may be a member of multiple groups.)
If none of the above are applicable, the Other Permission Bits are enforced.
In this example, the named user ACL entry accomplished our goal, because the user is not the file owner, and the named user entry takes precedence over all other entries.