Known Issue: Ranger Group Mapping
For Ranger AD integration, there is an issue with Ranger not being able to map a user on a group ‘Hdp_admins’ to a policy that allows/denies access to the group ‘Hdp_admins’. The issue is on the capital characters that might be on a AD group name definition.
Most HDP components get the group information for a user via the SSSD daemon. When asked for the groups the user ‘d.threpe’ belongs to we get:
[centos@rjk-hdp25-m-01 ~]$ groups d.threpe
d.threpe : domain_users hdp_admins hadoopSo ‘hdp_admins’ all in lower case. Ranger does not treat this as the same value as ‘Hdp_admins’ which came via the group sync and was applied to some policies.
There is no way to make the group sync write or retrieve the group names all in lower case since there is no AD attribute that rewrites it in lowercase.
This issue can be worked around fortunately (till it gets solved). The solution is to define a local group in Ranger as a shadow group of a real group from AD, but then all in lower case:
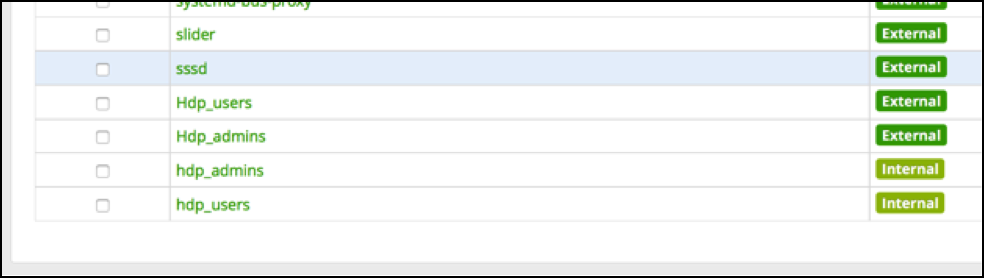
If we now create policies and use that lower case ‘shadow’ group literal the result is that policies are correctly mapped to the AD groups again:
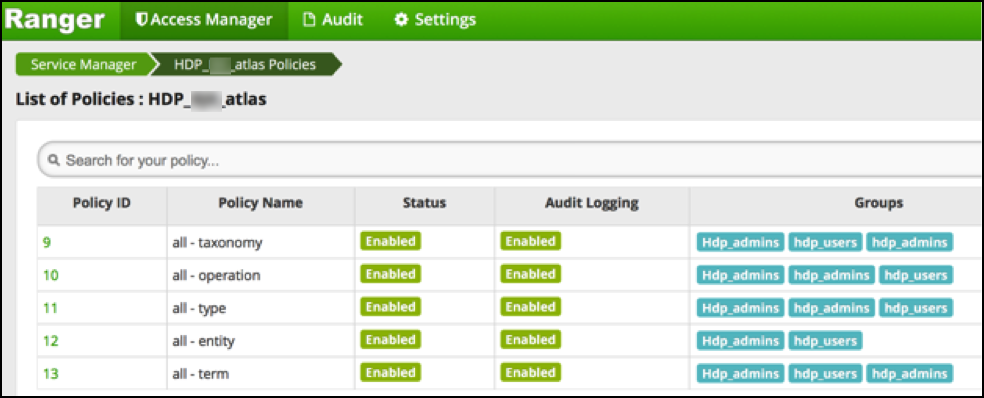
*The ‘Hdp_admins’ entry does not have to be there, it is shown for clarification only. ‘hdp_admins’ is necessary to make it work.

