Encrypting EBS volumes with a CMK generated from AWS CloudHSM
This section provides steps for encrypting a Cloudera Data Hub cluster with a CMK generated from a custom key store on AWS CloudHSM.
AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use their own encryption keys in AWS. CloudHSM runs in your VPC and provides you with the flexibility to integrate with many applications.
When using a custom key store, the default KMS key store is replaced by a dedicated key store, which is hosted on a single tenant CloudHSM cluster on AWS. When a user generates a CMK (Customer Managed Key), the key material is generated and stored in the CloudHSM and KMS forwards all the data encryption requests to the CloudHSM.
For more general information about CloudHSM, see AWS Security Blog.
To set this up, you need to create, initialize, and activate the HSM cluster, and then create a CMK from HSM. Once done, you can use the CMK for encrypting Cloudera Data Hub clusters. Detailed steps are provided below.
Cross-account role permissions
If planning to use encryption, ensure that the cross-account IAM role used for the provisioning credential includes the permissions mentioned in Permissions for using encryption.
Create a CloudHSM cluster
First, create a CloudHSM cluster.
Initialize the CloudHSM cluster
Now that you have created the CloudHSM cluster, you should initialize it.
Activate the CloudHSM cluster
Once you have initialized the cluster, you need to activate it. Activating the cluster can be done through the command line using an Amazon EC2 instance with a CloudHSM client installed on it.
Install the CloudHSM client on an Amazon EC2 instance. The instructions to install the CloudHSM client on an Amazon EC2 instance are documented well in Install and Configure the AWS CloudHSM Client (Linux). Make sure that the EC2 instance is on the same VPC that our cluster is created on.
- Attach the EC2 instance to the security group that was created as a result of creating the HSM cluster.
- To activate the CloudHSM cluster, you need to start the cloudhsm_mgmt_util through a command line utility, which will connect to the new HSM node and automatically enter the cloudHSM CLI. Follow the steps in Activate the Cluster (AWS docs).
Once the Cloud HSM is active, you can start creating CMK’s from the custom key store.
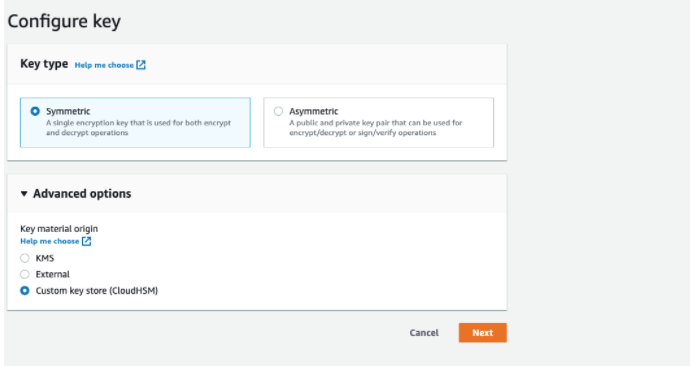
Create a CMK from CloudHSM
Now that you set up CloudHSM cluster, you can create a CMK from CloudHSM.
Encrypting data with a CMK on Cloudera Data Hub clusters
Use these steps to set up encryption for your Cloudera Data Hub cluster data with the CMK created earlier.