Permissions required for key encryption
If planning to use encryption key encryption, ensure that you configure the following permissions.
Cloudbreak credential service account's permissions
If you would like to use a KMS key (CMEK) or a custom key (CSEK), you must:
- Create a new custom role with the following permissions:
- cloudkms.cryptoKeys.get
- cloudkms.keyRings.list
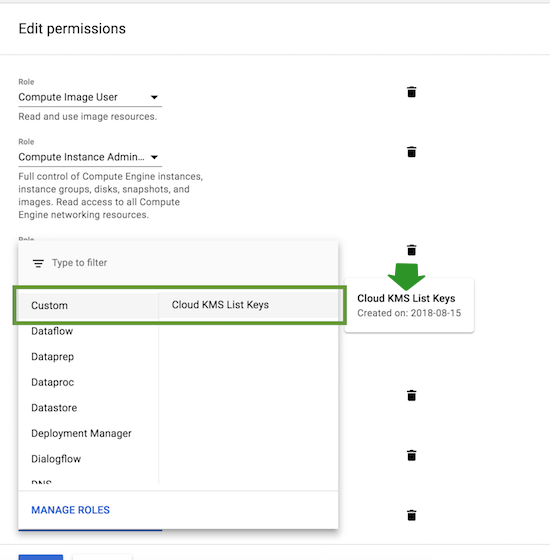
To create a custom role, navigate to IAM & admin > Roles and click on +Create role. Next, click on +Add permissions, select and add the required permissions, and click on Create:

 Note
NoteFor testing purposes, it is also possible to use the built-in Cloud KMS Admin role.
- Assign this role to your Cloudbreak credential’s service
account.
To assign this role, on Google Cloud portal, navigate to IAM & admin > IAM, edit the service account that you created for Cloudbreak credential, click on +Add another role, add the newly created custom role and click on Save. You should find this role under “Custom”:
Compute Engine system service account's permissions
Assign the Cloud KMS CryptoKey Encrypter/Decrypter role to the Compute
Engine system service account as described in Protecting resources with Cloud KMS Keys in Google Cloud documentation.
This is required by Google Cloud.

