Cloudera Navigator Key HSM Overview
Cloudera Navigator Key HSM allows Cloudera Navigator Key Trustee Server to seamlessly integrate with a hardware security module (HSM). Key HSM enables Key Trustee Server to use an HSM as a root of trust for cryptographic keys, taking advantage of Key Trustee Server’s policy-based key and security asset management capabilities while satisfying existing, internal security requirements for treatment of cryptographic materials.
Key HSM adds an additional layer of encryption to Key Trustee Server deposits, and acts as a root of trust. If a key is revoked on the HSM, any Key Trustee Server deposits encrypted with that key are rendered irretrievable.
The following diagram demonstrates the flow of storing a deposit in Key Trustee Server when Key HSM is used:
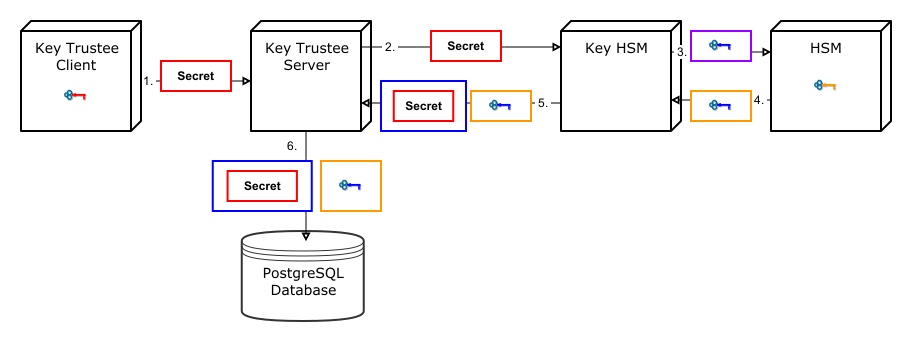
- A Key Trustee client (for example, Navigator Encrypt or Key Trustee KMS) sends an encrypted secret to Key Trustee Server.
- Key Trustee Server forwards the encrypted secret to Key HSM.
- Key HSM generates a symmetric encryption key and sends it to the HSM over an encrypted channel.
- The HSM generates a new key pair and encrypts the symmetric key and returns the encrypted symmetric key to Key HSM.
- Key HSM encrypts the original client-encrypted secret with the symmetric key, and returns the twice-encrypted secret, along with the encrypted symmetric key, to Key Trustee Server. Key HSM discards its copy of the symmetric key.
- Key Trustee Server stores the twice-encrypted secret along with the encrypted symmetric key in its PostgreSQL database.
The only way to retrieve the original encrypted secret is for Key HSM to request the HSM to decrypt the encrypted symmetric key, which is required to decrypt the twice-encrypted secret. If the key has been revoked on the HSM, it is not possible to retrieve the original secret.
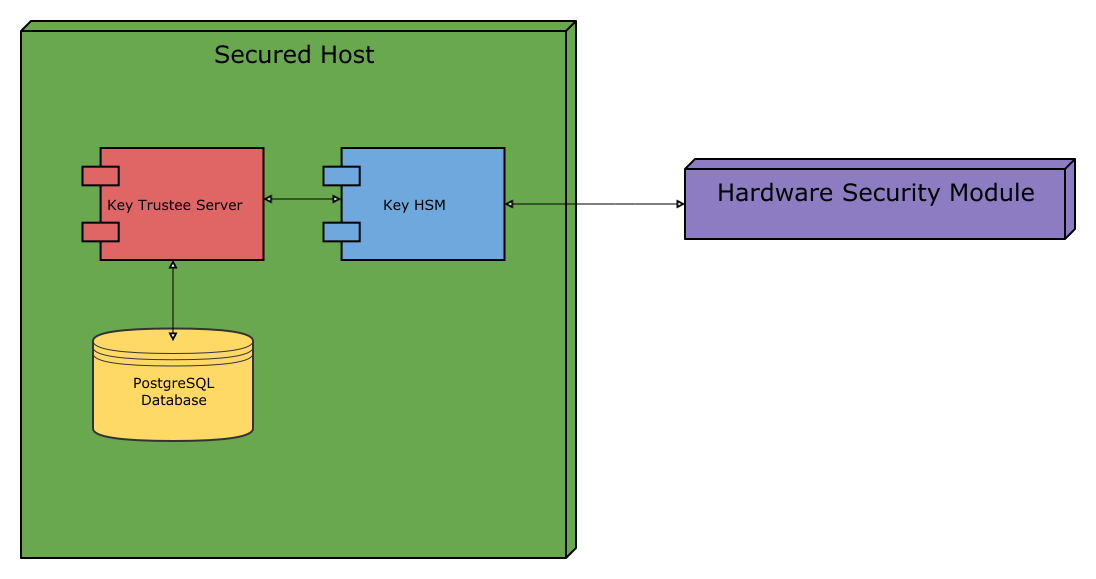
Key HSM Architecture
For increased security, Key HSM should always be installed on the same host running the Key Trustee Server. This reduces the attack surface of the system by ensuring that communication between Key Trustee Server and Key HSM stays on the same host, and never has to traverse a network segment.
The following diagram displays the recommended architecture for Key HSM:
For instructions on installing Navigator Key HSM, see Installing Cloudera Navigator Key HSM. For instructions on configuring Navigator Key HSM, see Initializing Navigator Key HSM.