Using an external authentication source for clusters
Cloudbreak allows you to register an existing LDAP/AD instance as an external source and use it for multiple clusters. You must create the LDAP/AD prior to registering it with Cloudbreak. Once you have it ready, the overall steps are:
- Register an existing LDAP in Cloudbreak web UI or CLI.
- Once registered, the LDAP will now show up in the list of available authentication sources when creating a cluster under advanced External Sources > Configure Authentication.
- Prepare a blueprint as described in Preparing a blueprint for LDAP/AD .
- Create a cluster by using the blueprint and by attaching the authentication source. Cloudbreak automatically injects the LDAP property variables into the blueprint.
Preparing a blueprint for LDAP/AD
In order to use LDAP/AD for your cluster, you must provide a suitable cluster blueprint:
- The blueprint must include one or more of the following supported components: Atlas, Hadoop, Hive LLAP, Ranger Admin, Ranger UserSync.
- The blueprint should not include any LDAP properties. Before injecting the properties, Cloudbreak checks if LDAP related properties already exist in the blueprint. If they exist, they are not injected.
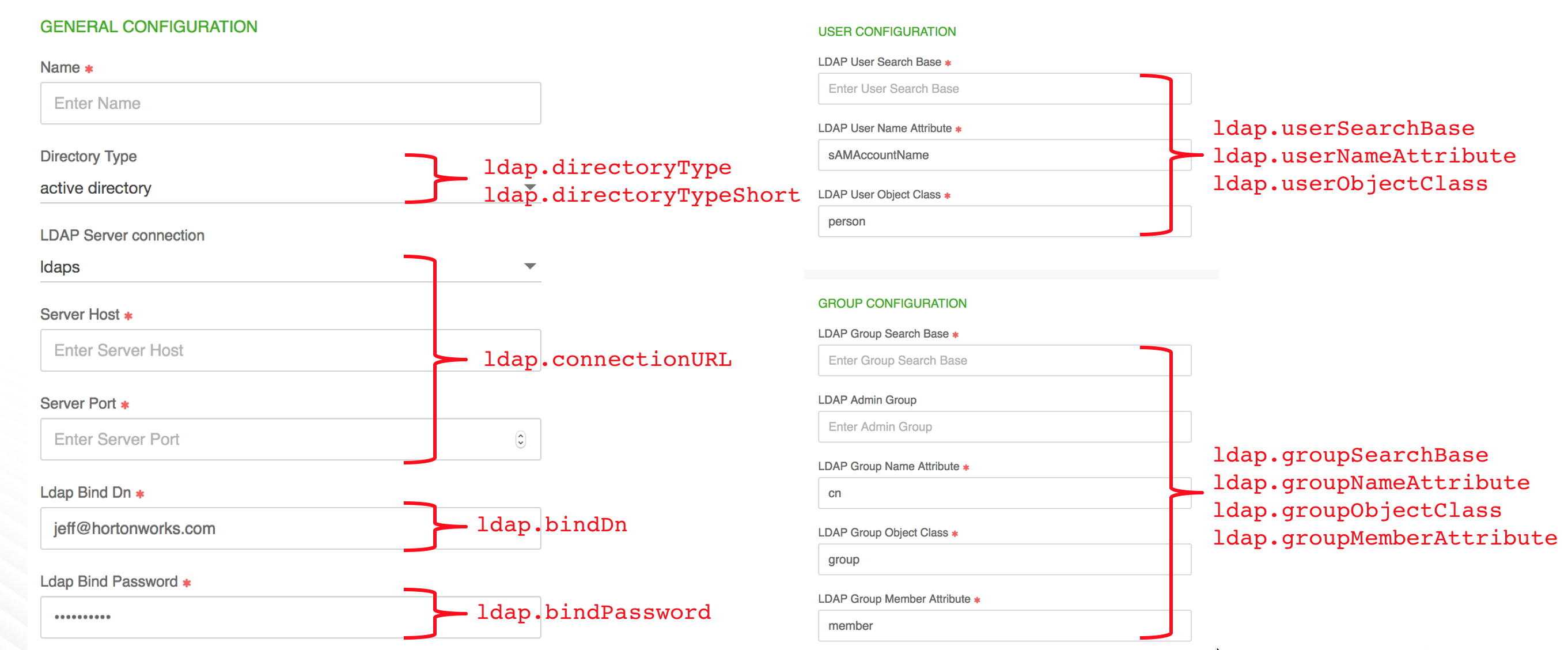
During cluster creation the following properties will be injected in the blueprint:
- ldap.connectionURL
- ldap.domain
- ldap.bindDn
- ldap.bindPassword
- ldap.userSearchBase
- ldap.userObjectClass
- ldap.userNameAttribute
- ldap.groupSearchBase
- ldap.groupObjectClass
- ldap.groupNameAttribute
- ldap.groupMemberAttribute
- ldap.directoryType
- ldap.directoryTypeShort
Their values will be the values that you provided to Cloudbreak:
Register an authentication source
Cloudbreak allows you to register an existing LDAP/AD instance and use it for multiple clusters. You must create the LDAP/AD prior to registering it with Cloudbreak. Once you have it ready, you can:
- Register an existing LDAP in Cloudbreak web UI or CLI.
- Use it as an authentication source for your clusters. Once registered, the LDAP will now show up in the list of available authentication sources when creating a cluster under advanced External Sources > Configure Authentication.
Steps
- From the navigation pane, select External Sources > Authentication Configurations.
- Select Register Authentication Source.
-
Provide the following parameters related to your existing LDAP/AD:
GENERAL CONFIGURATION
Parameter Description Example Name Enter a name for your LDAP. cb-ldap Directory Type Choose whether your directory is LDAP or Active Directory. LDAP LDAP Server Connection Select LDAP or LDAPS. LDAP Server Host Enter the hostname for the LDAP or AD server . 10.0.3.128Server Port Enter the port. 389LDAP Bind DN Enter the root Distinguished Name to search in the directory for users. CN=Administrator,CN=Users,DC=ad,DC=hdc,DC=comLDAP Bind Password Enter your root Distinguished Name password. MyPassword1234!USER CONFIGURATION
Parameter Description Example LDAP User Search Base Enter your LDAP user search base. This defines the location in the directory from which the LDAP search begins. CN=Users,DC=ad,DC=hdc,DC=comLDAP User Name Attribute Enter the attribute for which to conduct a search on the user base. HDCaccountNameLDAP User Object Class Enter the directory object class for users. personGROUP CONFIGURATION
Parameter Description Example LDAP Group Search Base Enter your LDAP group search base. This defines the location in the directory from which the LDAP search begins. OU-scoDC=ad,DC=hdc,DC=comLDAP Admin Group (Optional) Enter your LDAP admin group, if needed. LDAP Group Name Attribute Enter the attribute for which to conduct a search on groups. cnLDAP Group Object Class Enter the directory object class for groups. groupLDAP Group Member Attribute Enter the attribute on the group object class that represents members. member -
Click Test Connection to verify that the connection information that you entered is correct.
-
Click REGISTER.
-
The LDAP will now show up on the list of available authentication sources when creating a cluster under advanced External Sources > Configure Authentication. It can be reused with multiple clusters. Just select it if you would like to use it for a given cluster.